Triada Trojan infection chain | Image: Kaspersky
Newer versions of Android have significantly strengthened system security by prohibiting the modification of system partitions, even with superuser privileges. This has led to an unexpected consequence: malicious programs preinstalled within device firmware have become nearly impossible to remove. Cybercriminals have exploited this development by embedding trojans directly into system applications.
According to a report by Kaspersky Lab, this is precisely how the Triada malware has evolved—previously known through its Dwphon loader. In March 2025, researchers identified a new variant of Triada embedded within the firmware of counterfeit smartphones sold via online marketplaces. The trojan infected the Zygote process—the parent of all Android applications—thereby achieving complete system compromise.
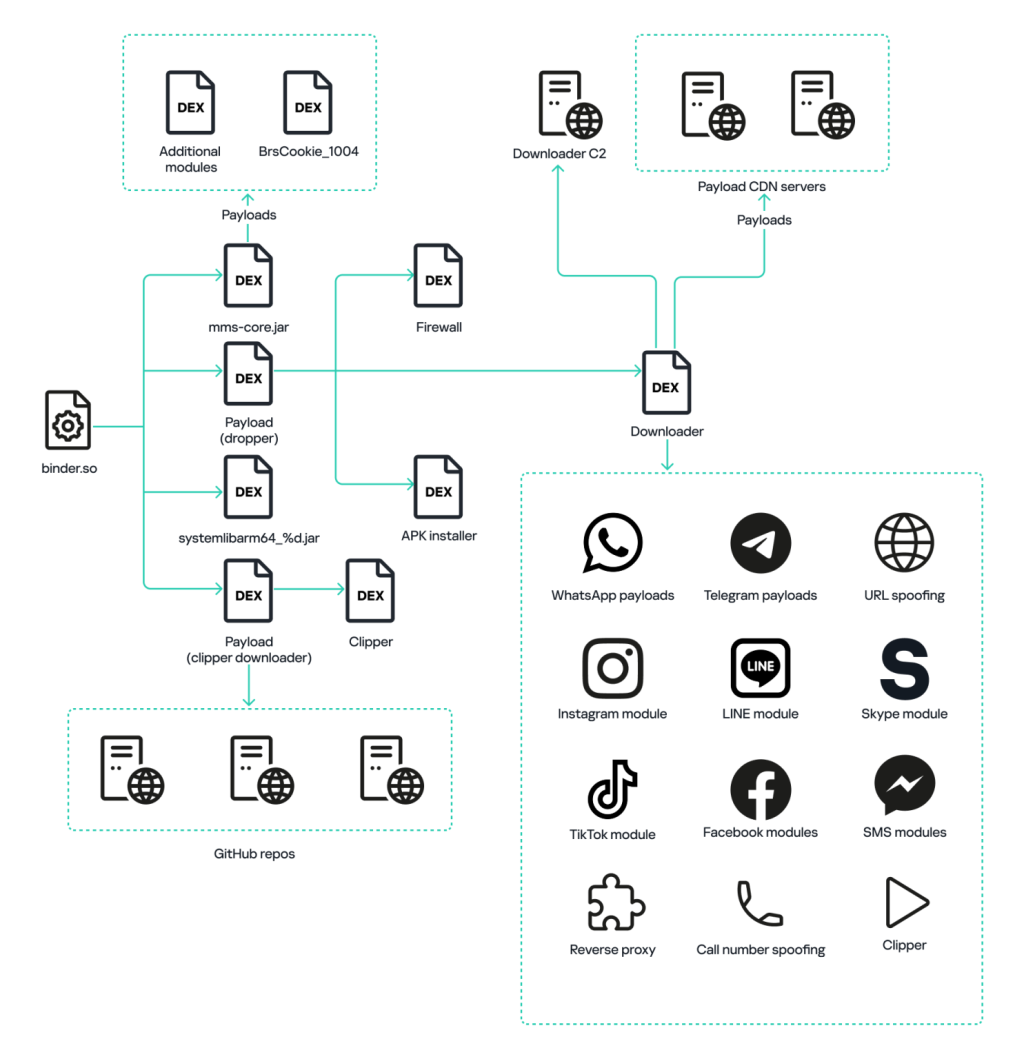
The Triada trojan now employs a complex, multi-stage architecture. Its components are injected into every process through a modified system library, binder.so, integrated within the boot-framework.oat file. This library connects to the Zygote process and launches three modules: an auxiliary module, the primary backdoor mms-core.jar, and a module focused on cryptocurrency theft and the installation of additional malware.
The auxiliary module registers a method call interceptor within application processes, facilitating the subsequent deployment of malicious functionalities. The primary backdoor enables the downloading of new malicious modules from command-and-control servers, targeting devices based on their characteristics and installed applications.
Particular emphasis is placed on attacking cryptocurrency-related applications. Malicious modules substitute wallet addresses in text fields and QR codes, intercept clipboard contents, and can even install malicious APKs without user consent.
Triada actively targets popular applications such as Telegram, WhatsApp, Instagram, various browsers, Skype, LINE, TikTok, and others. Tailored malicious modules have been developed for each app, capable of extracting session tokens, cookies, user data, and even intercepting and deleting messages.
For instance, modules designed for Telegram extract user tokens and delete messages according to predefined templates. Modules for WhatsApp can send messages on behalf of victims and delete sent communications. In Instagram, session cookies are stolen, while in browsers, opened links are redirected to advertising or phishing sites.
Triada can also transform an infected smartphone into a proxy server for redirecting malicious traffic or a covert tool for sending SMS messages to subscribe to premium services. In certain cases, modules modify premium SMS policies to bypass system restrictions.
Of particular concern is the Clipper module, which integrates into the Google Play application and checks the clipboard every two seconds for cryptocurrency addresses, replacing them with attacker-controlled alternatives.
Analysis of Triada’s C2 servers revealed that attackers managed to steal over $264,000 in cryptocurrency over recent months through address substitution and credential theft. Telemetry data indicates over 4,500 infected devices, with the highest infection rates recorded in the United Kingdom, the Netherlands, Germany, Brazil, and other countries.
Triada showcases a high level of technical sophistication, with module code containing comments in Chinese. Similarities with the infrastructure of the Vo1d malware project have also been observed, suggesting a potential link between the groups. The spread of infected devices is tied to shipments of counterfeit smartphones, often distinguished by forged firmware fingerprints. It is quite possible that device suppliers were unaware of the embedded threat.
To mitigate the impact of infection, it is recommended to reflash the device with a clean, official firmware, avoid using messengers and cryptocurrency wallets until the device is sanitized, and install a reliable antivirus solution to prevent future attacks.


