
Coinbase has resolved a bug in its account activity log that had sparked widespread alarm among users. Previously, the system had erroneously flagged failed login attempts using incorrect passwords as two-factor authentication failures, creating the false impression that attackers possessed clients’ login credentials.
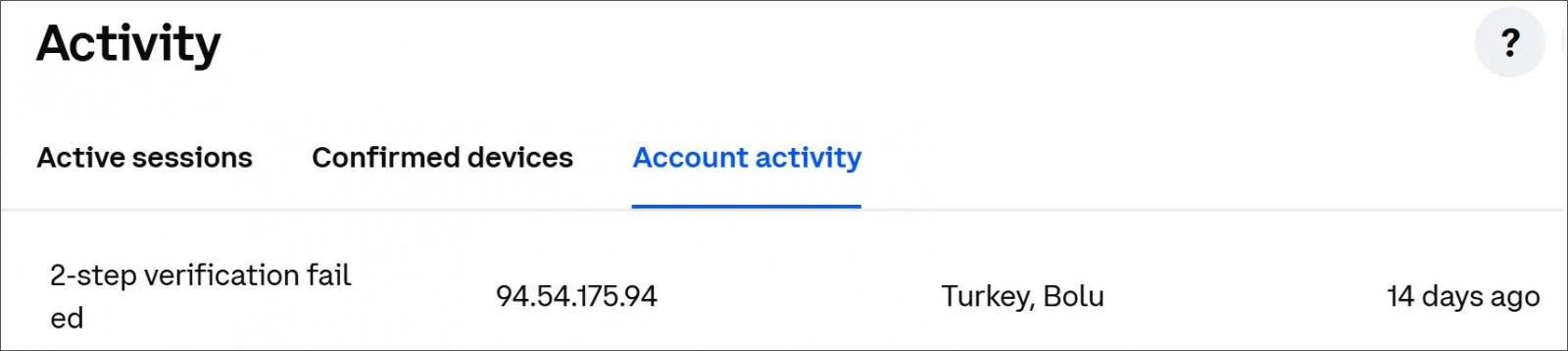
The issue first surfaced in early April. Users encountering errors labeled “second_factor_failure” or “2-step verification failed” feared that their accounts had been compromised. Ordinarily, such messages suggest that the password was entered correctly but that the failure occurred during the second authentication step involving an authenticator app code.
Numerous clients reported to journalists that their passwords were unique and that no other accounts or applications had been targeted, leading many to hastily reset their credentials and spend hours scanning their devices for potential malware.
However, Coinbase later confirmed that its activity log had mistakenly classified failed login attempts — even those involving incorrect passwords — as two-factor authentication failures. In reality, attackers had not progressed beyond the password entry stage.
The company has since issued an update correcting the mislabeling. Henceforth, users encountering such events will see the message “Password attempt failed,” providing a far more accurate reflection of what transpired.
Such logging errors are perilous not only because they cause panic but also because they could be exploited for social engineering attacks, convincing victims that their accounts had indeed been breached. These risks are particularly acute for clients of cryptocurrency platforms, where criminals frequently launch phishing campaigns aimed at stealing two-factor authentication codes or passwords.
Although no specific incidents have been confirmed in which this particular error was used in attacks, the environment was ripe for exploitation, especially given the prevalence of SMS phishing and voice scams impersonating Coinbase employees.
The company reminds users that it never contacts clients by phone or SMS to request password changes or two-factor authentication resets. Any such communications should be treated as fraudulent.


