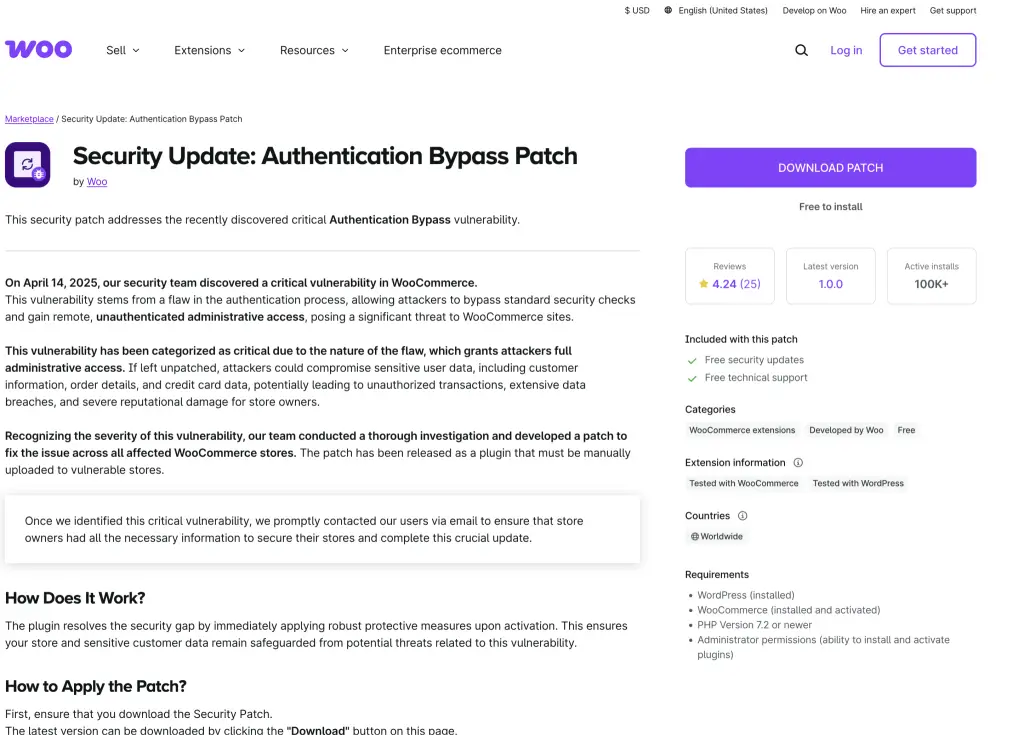
Specialists at Patchstack have uncovered a large-scale phishing campaign targeting users of the WooCommerce platform. Threat actors are distributing counterfeit security notifications, urging website owners to install a “critical update” that, in reality, implants a backdoor into WordPress systems.
The attack hinges on social engineering: unsuspecting administrators, persuaded to download and install what appears to be an essential patch, inadvertently deploy a malicious plugin. This plugin creates a hidden administrator account, uploads web shells, and ensures persistent access to the compromised site.
According to researchers, this campaign is a continuation of a similar operation conducted in late 2023, during which fraudsters also targeted WordPress users by disseminating fake patches for a fabricated vulnerability. Analysts note recurring patterns: an unusual set of web shells, identical techniques for concealing the malicious payload, and similar phrasing in the phishing emails.
The emails originate from help@security-woocommerce[.]com and warn recipients that their site has been subjected to hacking attempts exploiting a vulnerability described as “unauthorized administrative access.”
To “protect” the online store and its data, the attackers offer a download link for the patch via a built-in button, accompanied by detailed installation instructions. To add urgency, the message claims: “Warning: Our latest security scan on April 21, 2025, confirmed that this critical vulnerability directly affects your site.”
Clicking the “Download Patch” button redirects victims to a counterfeit WooCommerce page. The attackers exploit a particularly insidious domain, woocommėrce[.]com, which differs from the legitimate domain by a single character — substituting the Latin “e” with the Lithuanian “ė” (U+0117). This subtle discrepancy is nearly impossible to detect with the naked eye.
Upon installing the patch (a file named “authbypass-update-31297-id.zip”), a scheduled task with an arbitrary name is created. This task executes every minute, attempting to create a new user account with administrator privileges. Subsequently, the malicious plugin registers the compromised site via an HTTP GET request to woocommerce-services[.]com/wpapi and retrieves the second stage of the concealed payload.
Several PHP web shells — including P.A.S.-Form, p0wny, and WSO — are then deployed within the wp-content/uploads/ directory. Experts estimate that these tools grant full control over the compromised resource, enabling attackers to inject advertisements, redirect users to malicious pages, conscript the server into DDoS botnets, steal payment card data, or encrypt website contents for extortion — whatever their malicious intents may be.
To conceal its activities, the malicious plugin removes itself from the list of installed extensions and hides the administrator account it created. Patchstack recommends that website owners vigilantly check for suspicious signs: administrator accounts with random eight-character names, unusual scheduled tasks, the presence of the authbypass-update folder, and outbound requests to domains such as woocommerce-services[.]com, woocommerce-api[.]com, or woocommerce-help[.]com.
The report also emphasizes that once indicators of compromise become public knowledge, cybercriminals typically modify their tactics. Thus, defenders should not limit themselves to checking only these specific signs.


