Google has unveiled a new tool for sending encrypted emails, which has already sparked concern among cybersecurity and fraud prevention experts. The feature, currently available in beta for enterprise users, allows Google Workspace customers to send end-to-end encrypted messages. By year’s end, the company plans to extend this capability to include all email addresses, including those outside the Gmail ecosystem. It is precisely this expansion that has raised alarm.
End-to-end encryption ensures that only the sender and the recipient can access the contents of a message, with the data remaining encrypted throughout its entire transmission path. Traditionally, implementing such protection requires an advanced key management system and technical expertise, making it a solution typically reserved for large organizations with stringent security requirements. Google’s new tool aims to simplify this process, reducing the burden on IT departments by offering organization-wide automated key management.
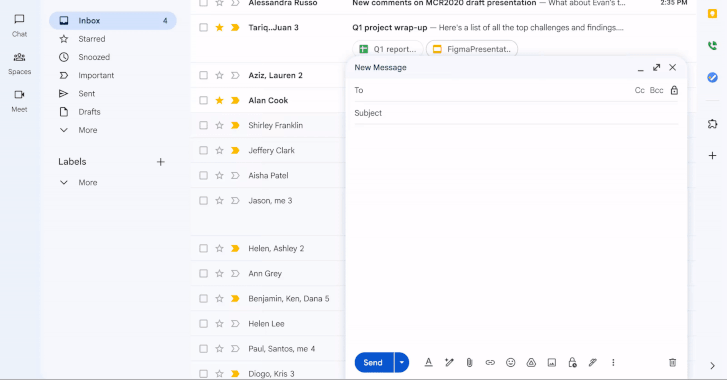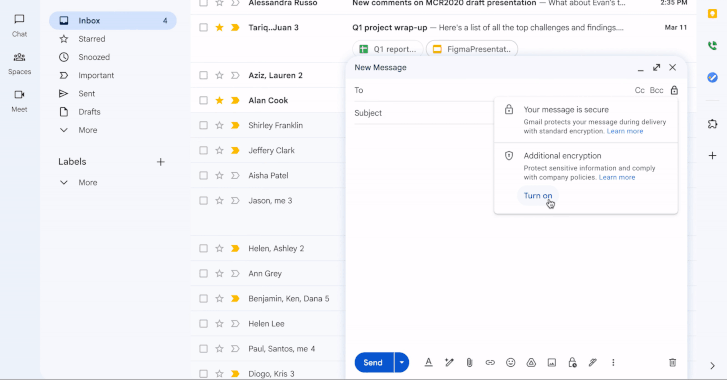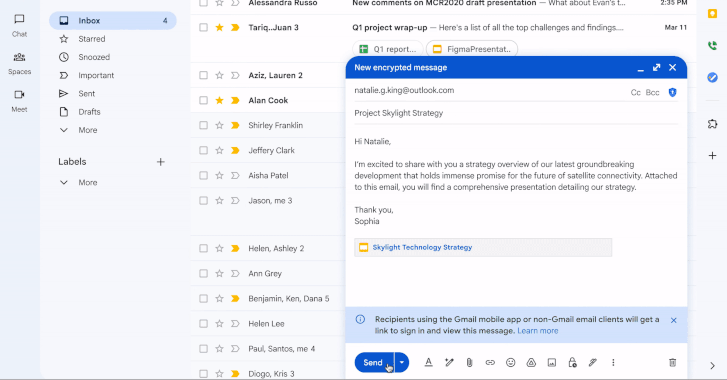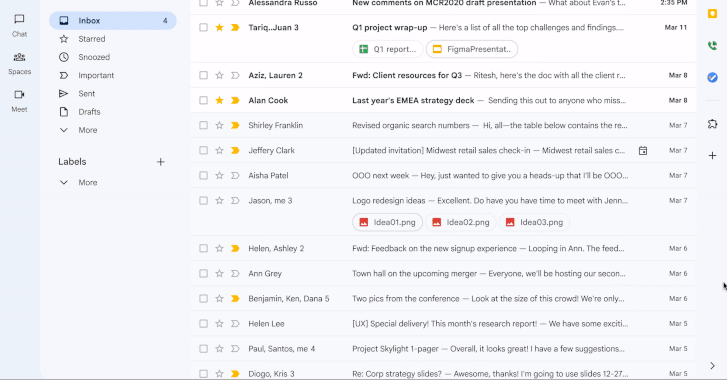
The primary vulnerability lies in scenarios where an encrypted message is sent to a non-Gmail address. In such cases, recipients receive an invitation to view the message through a guest account in a restricted version of Gmail. These messages include a cautionary note: “Be careful when signing in to view this encrypted message. It was sent by an external sender. Make sure you trust the sender and their identity provider.”
This very mechanism, however, may serve as fertile ground for phishing attacks. Cybercriminals could begin distributing fake invitations that closely mimic legitimate ones. A user unfamiliar with the new feature might follow a fraudulent link and unknowingly enter their credentials for email, corporate systems, or other services. Experts warn that Google is, in effect, creating a new channel that attackers can exploit to deceive unsuspecting users unfamiliar with this email format.
Moreover, the fact that encryption keys are managed by Workspace administrators, rather than being locally held by the sender and recipient, means that the system does not offer true end-to-end encryption in the strictest sense. Still, for compliance and internal process needs, the feature may prove beneficial. Yet, for genuinely confidential communication, security professionals recommend using specialized applications such as Signal.
Google asserts that it has accounted for potential threats during the design of this feature. According to a company spokesperson, the warning system mirrors those used when receiving files via Google Drive. However, history has demonstrated that spoofing such notifications outside of Google’s ecosystem is a common and difficult-to-prevent tactic.
The crux of the issue is trust. Users have grown accustomed to perceiving emails from Google as inherently safe, and the phrase “encrypted message” evokes a sense of the highest level of protection. This creates a dangerous illusion of security—one that fraudsters are likely to exploit. Even the built-in warning might not suffice: it can be easily copied and inserted into counterfeit emails, and most recipients are unlikely to scrutinize it closely.
In essence, Google faced a choice: to enable encrypted messaging for all recipients—accepting the phishing risks—or to restrict it solely to Gmail users. The company opted for the former, accompanied by a formal warning. Whether this safeguard will prove effective remains to be seen. For now, the new feature, despite its clear benefits, opens another door for attacks cloaked in the guise of enhanced security.


