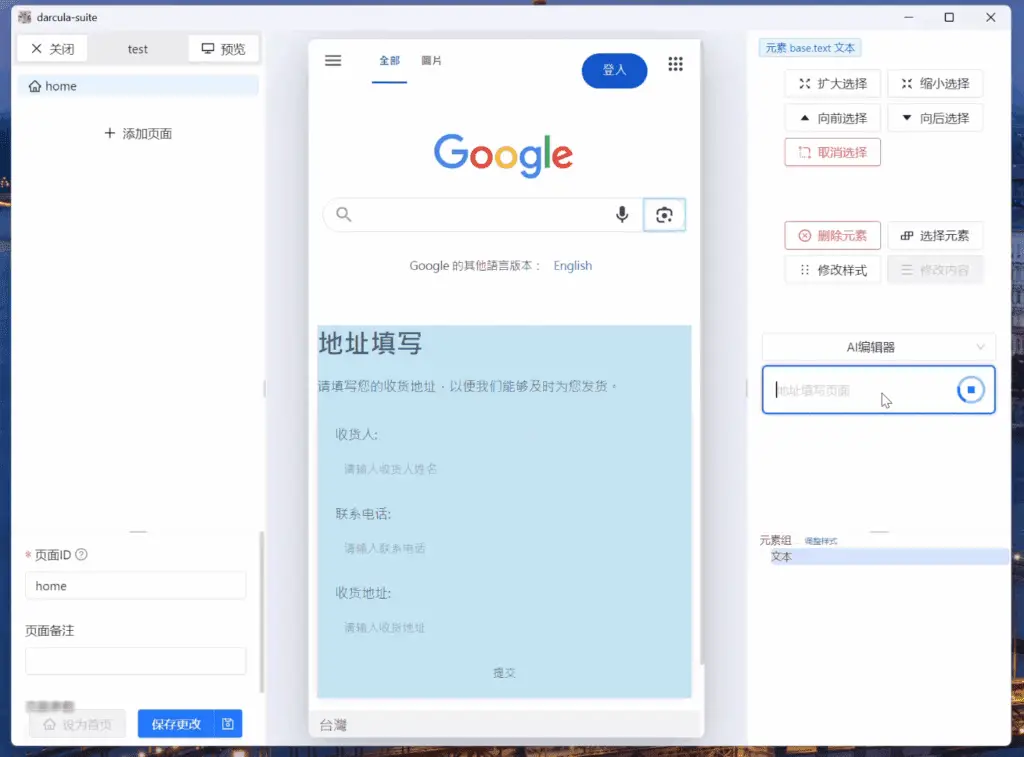
The Darcula platform, employed by cybercriminals for large-scale phishing campaigns, has recently been enhanced with support for Generative Artificial Intelligence (GenAI). This upgrade has made the creation of fraudulent pages even more effortless—allowing even individuals with no technical expertise to generate personalized forms and fabricate company websites within mere minutes.
Darcula first appeared on researchers’ radar in March 2024 as a phishing-as-a-service platform leveraging iMessage and RCS to dispatch counterfeit notifications allegedly from postal services. Even then, its toolkit enabled attackers to deceive users by redirecting them to fraudulent links. However, the integration of GenAI has elevated the threat to an entirely new level: malicious actors can now not only replicate the appearance of brand websites but also customize forms according to the target’s language and region, all without writing a single line of code.
A report from Netcraft emphasizes that these new capabilities have democratized phishing, opening the door to those who previously lacked the requisite technical skills. The automatic generation of multilingual forms and tailoring to specific victims enable attacks to be launched with unprecedented speed and precision. This makes Darcula especially perilous in the hands of mass phishing operators such as the Smishing Triad, an organization active on a global scale.
Recent research by PRODAFT attributes the creation of Darcula to a threat actor operating under the alias LARVA-246. The platform is promoted via a Telegram channel known as xxhcvv / darcula_channel. Darcula’s functionality overlaps with that of other notorious phishing kits, such as Lucid and Lighthouse—all believed to be part of a larger Chinese cybercriminal conglomerate united by a common goal: simplifying and scaling phishing operations.
Beyond simply cloning websites, Darcula allows users to easily configure form fields, translate them into various languages, and swiftly deploy phishing campaigns. This accessibility renders it an ideal tool for novice cybercriminals, dramatically increasing the volume of potential attacks.
Since March 2024, analysts have dismantled over 25,000 Darcula-generated phishing pages, blocked approximately 31,000 IP addresses, and identified more than 90,000 domains linked to its activities. Despite these extensive countermeasures, Darcula continues to evolve and become ever more accessible.
The latest update, officially unveiled on April 23, 2025, has raised serious concerns among cybersecurity experts. The ability to launch fully functional phishing pages in mere moments is now within almost anyone’s reach—one need only select a target and press the generate button.


