The security team behind the enterprise backup platform Commvault has issued a warning regarding a critical vulnerability in its Command Center management interface, allowing remote attackers to execute arbitrary code without prior authentication. The flaw, identified as CVE-2025-34028, has been assigned a maximum CVSS score of 10.0, ranking it among the most severe vulnerabilities disclosed in recent times.
The vulnerability affects the Commvault 11.38 Innovation Release, specifically versions from 11.38.0 through 11.38.19. Patches addressing the issue have been made available in versions 11.38.20 and 11.38.25. The flaw was discovered by security researcher Sonny of watchTowr Labs, who reported it on April 7, 2025.
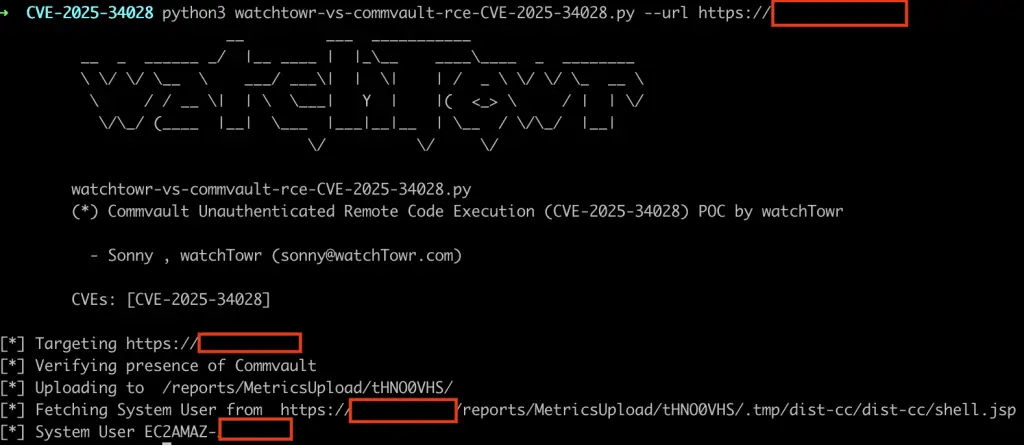
At the heart of the vulnerability lies the mishandling of requests to the internal resource deployWebpackage.do, which fails to properly filter destination addresses. This oversight enables a Server-Side Request Forgery (SSRF) attack, even without user authentication. The vulnerable mechanism imposes no restrictions on connections to external hosts, creating the risk of malicious archive retrieval.
An attacker could craft a specially designed HTTP request to initiate the download of a ZIP archive from an external server. The archive’s contents would then be unpacked into a temporary directory, after which the attacker, leveraging the servicePack parameter, could relocate files into a vulnerable server directory. The final step involves triggering a malicious .jsp script placed along a predetermined path, granting the attacker full control over the compromised system.
To aid in identifying evidence of exploitation, watchTowr has released a specialized artifact generator, enabling organizations to scan their installations for signs of compromise. This proactive measure may facilitate a timely response and mitigate potential damage.
In light of recent attacks against similar solutions—including backup software from Veeam and NAKIVO—experts stress the critical importance of urgently patching vulnerable Commvault instances. Such systems traditionally house sensitive data and serve as gateways to critical infrastructure, making them highly attractive targets for adversaries.


