Advertisement for Anubis "accesses monetization" service. (Source: Secureworks)
Despite sustained efforts by international law enforcement to dismantle major extortion operations, cybercriminals continue to exhibit remarkable adaptability and resilience. In 2025, experts from Secureworks’ Counter Threat Unit (CTU) observed the emergence of two revamped operational models employed by the DragonForce and Anubis groups, each adopting novel strategies to attract affiliates and boost profitability.
Initially structured around a conventional Ransomware-as-a-Service (RaaS) framework, DragonForce announced its transition in March 2025 to a decentralized “cartel” model. This transformation allows each affiliate to establish an independent “brand” while gaining access to a ready-made infrastructure—complete with administrative and customer panels, file-hosting systems, encryption and negotiation tools, and a dedicated dark web leak site.
Notably, DragonForce no longer mandates the exclusive use of its proprietary malware. Affiliates may deploy their own tools without forfeiting access to the group’s infrastructure. This newfound flexibility broadens the potential partner base, appealing both to technically inexperienced actors and seasoned operatives seeking greater autonomy. However, the shared infrastructure poses an inherent risk: the compromise of a single member could potentially expose the entire network.
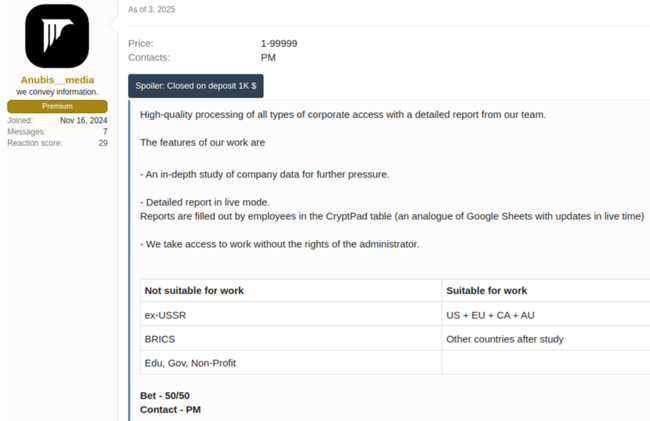
Anubis, meanwhile, has adopted a different approach. Beginning in February 2025, the group promoted its services on underground forums, emphasizing flexibility in extortion tactics. Affiliates may choose from three monetization models: classic encryption with an 80% ransom share, a non-encrypting extortion method offering 60%, and monetization of pre-existing access to victim systems at 50%.
The data-leak extortion model is particularly noteworthy for its pressure tactics. After exfiltrating sensitive information, Anubis publishes an exposé on a Tor-based site along with a link to initiate ransom negotiations. If the victim refuses to comply, the data is made publicly accessible. In addition, the group may disclose the victim’s identity on social media and threaten to notify the company’s clients. Their advertisements also highlight the intent to report breaches to regulatory authorities—a rare practice, though it has precedent, as seen in November 2023 when ALPHV lodged a complaint with the SEC against a non-compliant victim.
The “access monetization” option empowers threat actors who have already infiltrated systems to maximize their advantage by leveraging detailed analyses of confidential data for coercive purposes.
Anubis also explicitly limits its geographical scope. It refrains from targeting post-Soviet states and BRICS member nations. Attacks on government, educational, and nonprofit entities are likewise off-limits—though the conspicuous omission of the healthcare sector renders medical organizations potential targets.
As competition among extortion groups intensifies, so too do efforts to maximize returns through increasingly aggressive tactics. This comes amid a decline in ransom payments, evidenced by a surge in victim listings on leak sites—typically those who refuse to negotiate. In response, cybercriminals are escalating pressure campaigns and refining their strategies, including public exposure and regulatory blackmail.
Secureworks underscores that paying a ransom offers no assurance of data recovery or containment of leaks. Instead, the firm advises organizations to prioritize proactive defense: consistently patch vulnerable systems, implement robust phishing-resistant multi-factor authentication, maintain and routinely test backup systems, monitor network and endpoint activity, and develop comprehensive incident response plans.


