Outdated devices with high-speed internet have increasingly become liabilities to global cybersecurity—a trend starkly illustrated in 2025. According to Qrator Labs, March witnessed the largest DDoS attack ever recorded, orchestrated by a botnet comprising 1.33 million compromised devices—six times larger than the most extensive botnet of the previous year.
The attack occurred on March 26, targeting an undisclosed client in the online betting sector. It lasted approximately two and a half hours. Notably, 51.1% of the infected devices originated from Brazil, with the rest distributed across Argentina, Russia, Iraq, and Mexico. Experts affirm that geoblocking proved ineffective, as botnet operators rapidly reallocated IPs across regions using pre-established contingencies.
Qrator Labs attributes the botnet’s scale to widespread reliance on outdated hardware in developing countries. Many low-cost smartphones—particularly Chinese models without Google protections—ship with preinstalled malware. Researchers estimate around five million of these devices have been neutralized and disconnected from command servers. However, the broader pattern persists: the longer unsupported devices remain in circulation, the greater the risk of their assimilation into botnets.
The issue is compounded by such devices supporting 4G, featuring powerful modems and robust connectivity—making them ideal launch points for attacks. This has triggered an unprecedented surge in activity: DDoS incidents in Q1 2025 rose by 110% year-over-year, following a 50% increase in 2024.
Qrator Labs CTO Andrey Leskin states that the world has never faced attacks of this magnitude. A botnet of this size can generate tens of millions of requests per second, overwhelming unprotected systems within minutes.
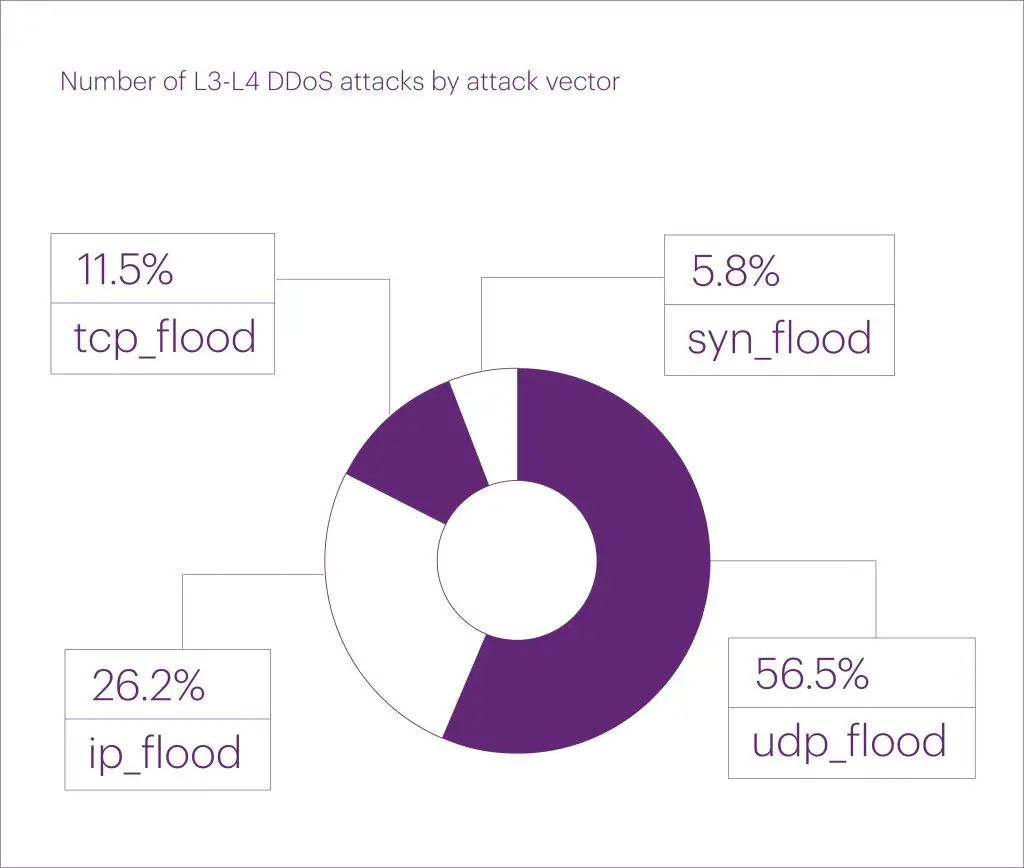
At the network (L3) and transport (L4) layers, most attacks targeted IT and telecom (26.8%), fintech (22.3%), and e-commerce (21.5%). At the application layer (L7), fintech led with 54% of attacks, followed by marketplaces at 14.4%.
Beyond direct disruptions, botnets are also deployed for subtler abuses: data scraping, metric falsification, brute-force attempts, and other forms of automated exploitation.
Given the global dependence on connectivity and the escalating proliferation of vulnerable endpoints, the scale and frequency of such cyber threats will continue to rise. Without intervention, far more destructive attacks are imminent.


