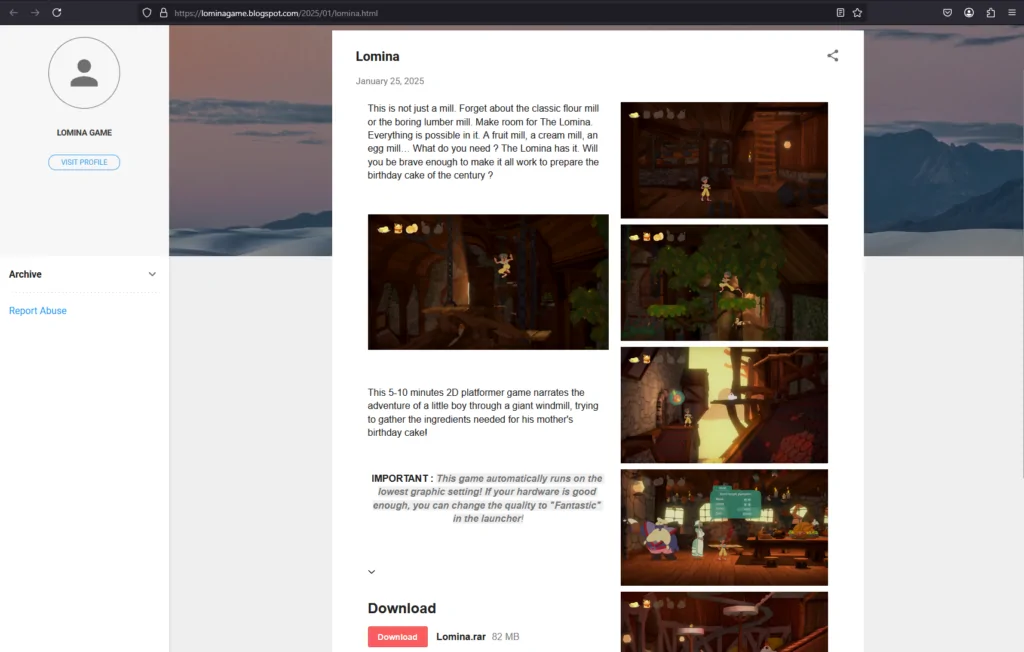
A Blogspot webpage that is used to deliver the rar file containing AgeoStealer. (Source: Flashpoint)
By early 2025, credential theft through malware had become a veritable goldmine for cybercriminals. Infostealers alone were responsible for up to 75% of all compromised accounts in 2024—amounting to approximately 2.1 billion credentials out of a total of 3.2 billion. New variants of such malicious tools continue to emerge on underground markets, and among the latest is AgeoStealer—a threat specifically targeting the gaming community.
This malware spreads through unconventional means: attackers directly approach potential victims on Discord and other popular platforms, offering them a chance to “test a new video game.” The user receives a password-protected archive containing an installer disguised as a Unity application. In reality, it is a modified NSIS file that executes a malicious JavaScript script.
AgeoStealer demonstrates sophistication at every stage of its operation. Once executed, it registers itself for autostart, conceals its presence through obfuscated code, checks for virtual environments or debugging tools, and terminates them to thwart analysis. These evasive techniques enable it to persist stealthily within the system, bypassing conventional security mechanisms.
Its primary targets are web browsers—Chrome, Firefox, Edge, and Opera. The infostealer scans active processes to locate those associated with storing login credentials, cookies, and tokens, then extracts the relevant data. It also inspects standard user directories such as Desktop and Downloads, with particular focus on large files that may harbor sensitive information.
After data collection, the information is compressed and uploaded to GoFile.io, allowing the attackers to retrieve it remotely without raising red flags or triggering defense systems. All of this occurs swiftly and silently in the background, making early detection virtually impossible.
According to Flashpoint analysts, AgeoStealer’s principal threat lies in its trifecta of ease of distribution, operational efficiency, and continuous adaptation to emerging defenses. Its architecture allows cybercriminals to rapidly tailor its features to current needs, exploiting the emotional engagement of gamers as a vulnerability.
The gaming community has become an enticing target not only because of its sheer size but also due to users’ often lax attitudes toward downloading files in informal settings. Beneath the façade of a beta release or early access demo, lurk mechanisms capable of stealing banking credentials, cryptocurrency wallet access, and private files. Whereas infostealers were once tools of broad-based attacks, they are increasingly evolving into precision instruments of digital espionage and asset theft.
Organizations and individual users alike must reconsider their security strategies, particularly in the context of social engineering. The ability to recognize novel threats and promptly update defenses is now critical. Monitoring these attack vectors in real-time and identifying malware variants is no longer the sole domain of antivirus software—it demands the concerted efforts of comprehensive analytical platforms.
AgeoStealer is not merely another strain of malicious code—it exemplifies a modern trend where the point of attack is no longer a flaw in software, but a flaw in human behavior. As long as gaming platforms remain vibrant hubs for communication and file exchange, such exploitative schemes will only continue to proliferate.


