Since early March 2025, cybersecurity specialists at Volexity have documented a series of highly sophisticated attacks targeting employees of NGOs and human rights organizations in Eastern Europe. The primary objective of these campaigns was to gain access to corporate Microsoft 365 accounts through carefully crafted social engineering and the manipulation of OAuth 2.0 authentication flows, all conducted via legitimate Microsoft services.
The attackers adopted an unconventional approach: contact with victims was initiated via secure messaging platforms such as Signal and WhatsApp. Impersonating diplomats from European consulates, the adversaries invited targets to participate in exclusive video meetings centered on international cooperation. Once rapport was established, victims received links to genuine Microsoft login pages, where OAuth was used to generate an authorization code.
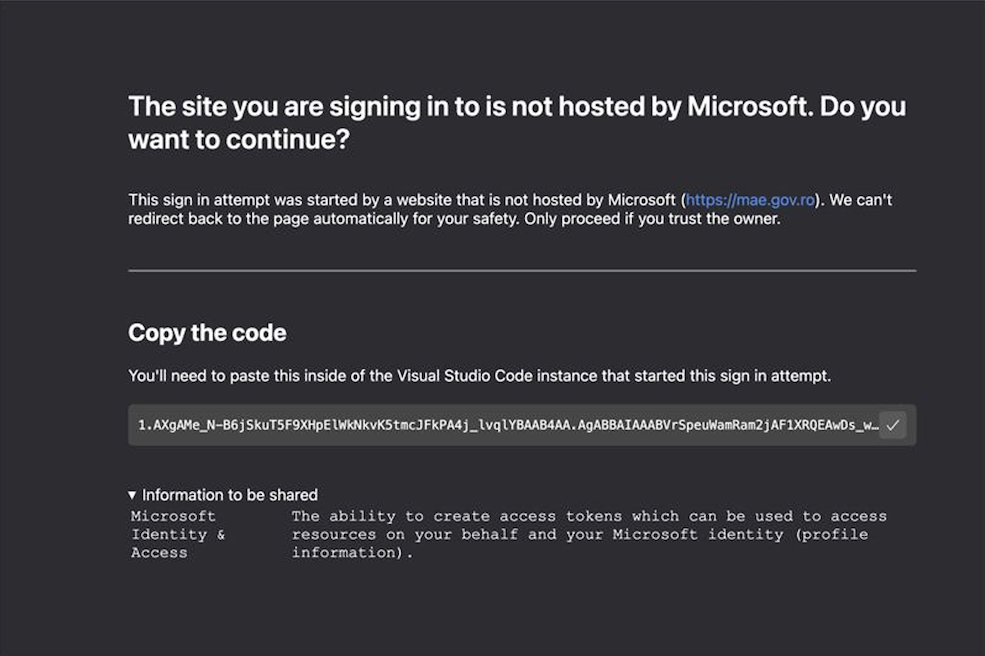
The deception hinged on a clever twist — merely clicking the link was not enough. The attackers would request the victim to return the system-generated code, claiming it was necessary to join the virtual meeting. Once obtained, this code allowed the adversaries to access the victim’s Microsoft 365 account, register a new device to the corporate infrastructure, and begin exfiltrating data, including emails and internal correspondence.
In one documented case, the attackers exploited the VSCode infrastructure. Upon clicking the link, the user was redirected to the web-based version of the code editor, where the authorization code was displayed. The victim was then instructed to copy and paste the code back to the attacker—often via the same messaging app used for initial contact.
Another variant of the attack began with a seemingly innocuous email sent from a compromised government address. The message contained no malicious links but simply invited the recipient to confirm their interest in a private meeting. Once the user replied, further instructions followed via messenger, once again leading to a request for the OAuth code.
A defining characteristic of this technique was the exploitation of the device registration API. After securing the authorization code, the attacker would register a new device within the corporate environment and subsequently prompt the user to complete a two-factor authentication (2FA) request—allegedly to gain access to the meeting materials. This final step not only verified access but also granted the adversary full control of the mailbox.
Subsequent log analysis revealed that email data was downloaded from these newly registered devices, often originating from proxy IP addresses geographically aligned with the victims.
The insidious nature of this methodology lies in its exclusive use of Microsoft’s official infrastructure. At no point are victims redirected to malicious domains or required to install unauthorized applications, which significantly hinders detection. Users encounter only familiar Microsoft domains, lowering their guard and increasing the likelihood of success for these social engineering tactics.
As a precaution, experts advise organizations to configure alerts for suspicious client_id usage, monitor new device registrations—especially those from questionable IP ranges—and limit access to sensitive data to trusted devices only. Additionally, it is vital to train staff to recognize social engineering attempts, particularly those initiated through personal or obscure communication channels.
While the scope of these attacks remains limited, their precision targeting and technical sophistication pose a serious threat. Individuals involved in humanitarian aid, human rights advocacy, and international diplomacy are particularly at risk. Given the success and stealth of these operations, experts warn that such techniques are likely to proliferate in the near future.


