The ConfusedComposer vulnerability, uncovered by researchers at Tenable, stands as yet another illustration of how the internal logic of cloud services can be exploited to gain privileges far beyond what was originally intended. Although the flaw has since been addressed, its implications offer a fresh perspective on security within the Google Cloud Platform (GCP)—particularly in scenarios where automation and service orchestration become a system’s Achilles’ heel.
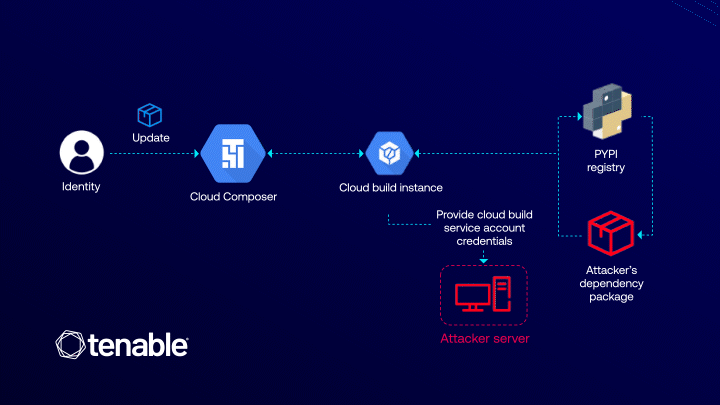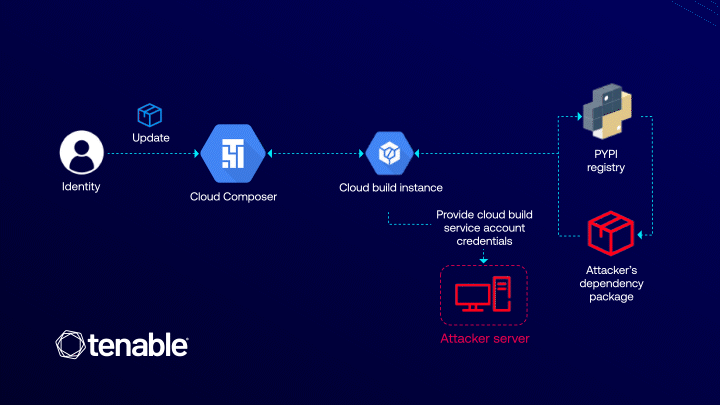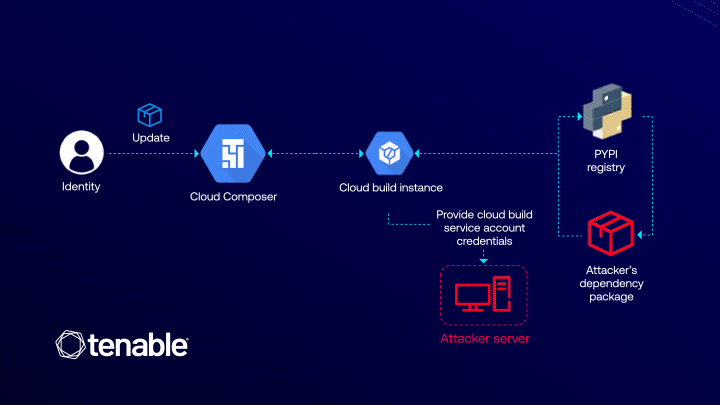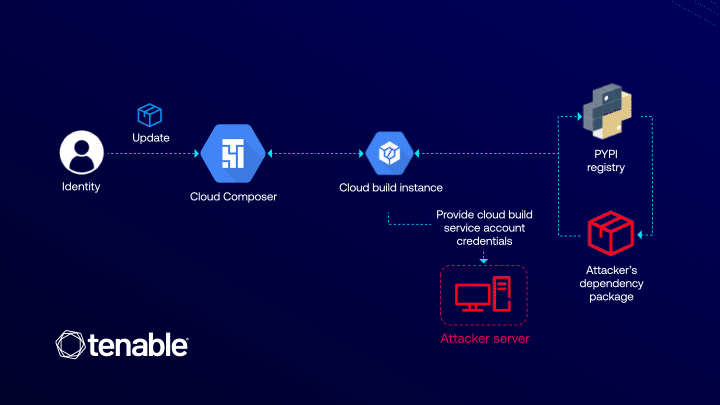
Cloud Composer is a fully managed workflow orchestration service built on Apache Airflow, designed to automate and streamline data pipelines. It is tightly integrated with Cloud Build, a service responsible for building, testing, and deploying applications. The vulnerability emerged at the intersection of these two platforms.
The issue stemmed from the process of installing additional Python libraries in Composer. During this operation, Composer automatically invoked Cloud Build to generate the environment. Crucially, this process was executed using Cloud Build’s default service account, which possesses broad privileges across core GCP services, including access to storage buckets and artifact registries. An attacker, requiring only the composer.environments.update permission, could exploit this behavior.
By injecting a malicious PyPI package into the environment configuration, an attacker could leverage Pip—used by Cloud Build to install dependencies—to execute arbitrary code through setup scripts. This, in turn, would grant access to the Cloud Build environment’s metadata, including the authorization token tied to its service account, thereby enabling lateral movement and control over significant portions of the victim’s cloud infrastructure.
What made the attack particularly insidious was that it did not require direct access to the Composer or Cloud Build service accounts. The sole prerequisite was a seemingly innocuous permission—composer.environments.update—commonly assigned in DevOps and CI/CD workflows. Thus, a legitimate user could escalate privileges to a project-wide administrator without triggering explicit violations of access policies.
Following Tenable’s disclosure, Google restructured the mechanism used to install additional libraries. Composer now employs a less-privileged service account specific to the Composer environment, significantly reducing the potential attack surface. Moreover, the documentation has been revised to better articulate access control best practices and dependency management guidelines.
This incident builds upon the earlier discovery of the ConfusedFunction vulnerability, contributing to a newly emerging class of exploits researchers are calling the “Jenga Effect.” Much like the eponymous game—where the removal of a single, seemingly minor block can topple an entire structure—cloud environments are often susceptible to catastrophic failures stemming from obscure dependencies and hidden orchestration behaviors.
In a world increasingly defined by automation and abstraction, security must extend beyond surface-level permissions to encompass the deeper architecture of interdependent services. ConfusedComposer serves as a compelling reminder of this imperative.


