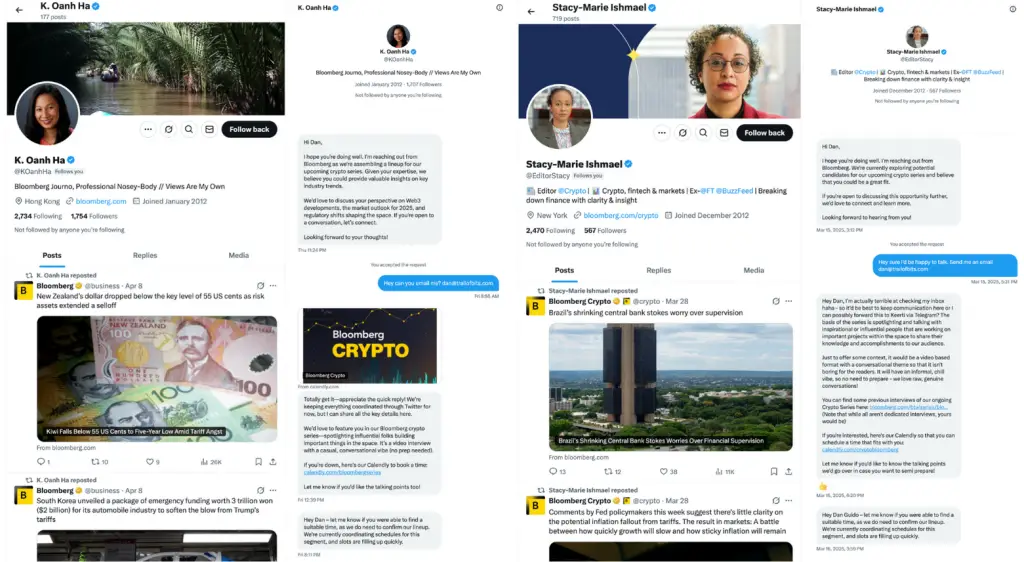
X DMs between Dan Guido (Trail of Bits CEO) and sockpuppet accounts from ELUSIVE COMET
Zoom’s remote access functionality has become the foundation of a new, highly sophisticated attack campaign targeting professionals in the cryptocurrency and financial sectors. A feature once lauded for its collaborative utility—allowing participants to grant control of their devices during video calls—is now being exploited by threat actors to deploy malware and exfiltrate sensitive data.
One such group, designated ELUSIVE COMET by the nonprofit cybersecurity organization The Security Alliance (SEAL), has been impersonating representatives of the venture capital firm Aureon Capital, along with its affiliated entities, Aureon Press and The OnChain Podcast. The attackers have created convincing websites and active social media profiles, posing as reputable industry figures in order to build trust with their targets.
The victims are approached via the platform X or email with invitations to participate in a podcast interview. Upon agreeing, a Zoom call is initiated, during which the target is asked to share their screen—ostensibly to present a deck or project. At that moment, the attacker sends a request for remote control of the computer. If the victim is unaware, they may inadvertently grant access.
A particularly deceptive aspect of the attack is the assailant’s tactic of altering their Zoom display name to “Zoom,” mimicking a legitimate system prompt—such as “Zoom is requesting remote control access.” This subtle trick lowers the target’s guard; instinctively clicking “Allow” without hesitation becomes dangerously easy. As recounted by Jake Gallen, founder of the NFT platform Emblem Vault, he was unaware of the precise moment he relinquished control. The consequences were severe—he lost access to several accounts and nearly $100,000.
A similar attempt was made against the CEO of the consulting firm Trail of Bits, but it was thwarted. The firm’s staff noticed discrepancies: suspicious social media profiles, reluctance to communicate via email, and fake scheduling pages—all of which served as red flags, enabling them to detect the threat in time.
Of particular concern is the fact that Zoom’s remote control permissions are enabled by default in many configurations. Unless manually disabled by the user or administrator, this feature remains vulnerable to exploitation. Experts urge organizations dealing with cryptocurrency or other sensitive data to either abandon Zoom entirely or, at the very least, disable remote access capabilities.
The ELUSIVE COMET campaign exemplifies a shift in modern cyber threats: away from traditional code-based vulnerabilities and toward operational security failures. Human error, inattention, and misplaced trust in familiar interfaces are increasingly exploited as entry points. As technical defenses grow more robust, adversaries are pivoting toward social engineering and psychological manipulation to breach their targets.


