
Cybersecurity researchers have uncovered a new variant of the ZLoader malware, now leveraging DNS tunneling technology to communicate with its command-and-control (C2) server. This discovery underscores the continued evolution of the tool by threat actors who reactivated its use last year.
According to a recent report by Zscaler, version 2.9.4.0 of ZLoader introduces significant enhancements, including a custom DNS protocol for C2 communication and an interactive shell supporting over a dozen commands. These features bolster its utility in ransomware attacks, increasing the malware’s resilience against detection and mitigation efforts.
ZLoader, also known as Terdot, DELoader, or Silent Night, functions as a loader capable of deploying additional malicious modules. Its activity resumed in September 2023, nearly two years after its infrastructure was dismantled.
The latest version employs a domain generation algorithm (DGA) and advanced anti-analysis techniques. For instance, it avoids execution on devices other than the originally infected ones, a behavior reminiscent of the Zeus banking Trojan on which ZLoader is based.
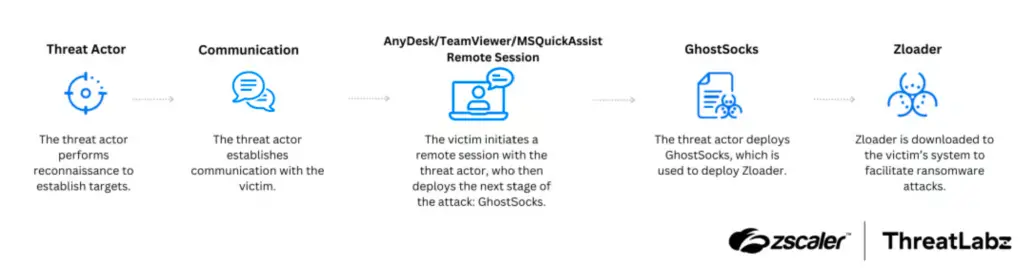
In recent months, ZLoader has been increasingly linked to ransomware attacks involving Black Basta. Threat actors deliver the malware through remote desktop connections, masquerading as technical support services.
Researchers identified a new element in the attack chain—a GhostSocks module that facilitates the installation of ZLoader. This highlights the growing complexity of infection mechanisms and the refinement of evasion strategies.
Moreover, the malware has enhanced its anti-analysis algorithms, incorporating runtime environment checks and API import methods to evade sandbox environments and static detection tools.
One of the most notable features of this variant is its interactive shell, enabling threat actors to execute arbitrary binary files, DLLs, shellcodes, retrieve data, and terminate processes. In addition to using HTTPS with POST requests for C2 communication, ZLoader now supports DNS tunneling, encrypting traffic via TLS within DNS packets.
Experts emphasize that these innovations demonstrate the group’s focus on circumventing detection methods. The addition of these new capabilities further establishes ZLoader as a formidable tool for initial system compromise, paving the way for subsequent ransomware deployment.


