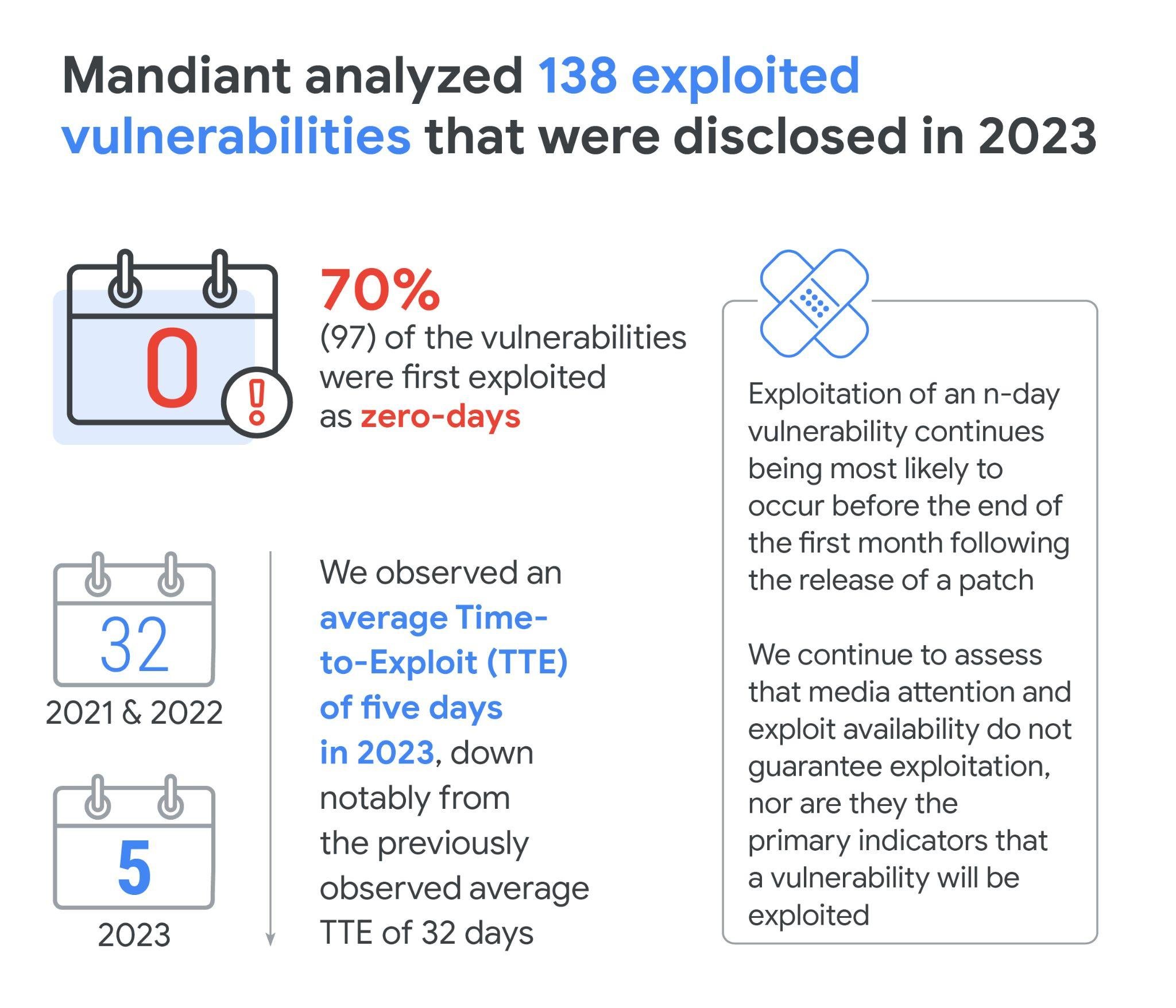
Google Mandiant analysts have issued a warning about a growing trend: hackers are increasingly discovering and exploiting zero-day vulnerabilities in software. The experts examined 138 vulnerabilities identified in 2023 that were actively used in real attacks. The majority of these (97) were exploited as zero-day, meaning before patches were released. The remaining 41 flaws were exploited after patches had been issued and are classified as n-day vulnerabilities. Analysts noted a significant increase in the gap between zero-day and n-day exploitation in 2023, highlighting the rising prevalence of zero-day attacks.
The average time-to-exploit (TTE) for vulnerabilities in 2023 decreased to five days, a record low since observations began. By comparison, in 2018, the first attack on a vulnerability took an average of 63 days, while in 2021-2022, the average dropped to 32 days. This rapid reduction in TTE indicates that malicious actors are exploiting vulnerabilities faster than companies can implement the necessary updates.
Analysts also pointed out the difficulties in collecting accurate data. The dates of initial attacks are not always disclosed or are reported imprecisely, often only indicating a general period such as “Q2 2023.” This complicates efforts to assess the true timelines. Mandiant emphasizes that the actual time-to-exploit could be even shorter than the available data suggests.
In 2021-2022, the ratio of zero-day to n-day attacks remained stable at 62% to 38%, but in 2023, zero-day attacks accounted for 70%. This shift is attributed not only to the rise in zero-day vulnerabilities but also to improved detection tools for identifying such weaknesses. It is expected that these changes will continue, though forecasts remain cautious.
In 2023, more than half of n-day vulnerabilities were attacked within the first month after the patch was released. Fifteen percent of these flaws were exploited within the first 24 hours, and 56% within a month. Notably, nearly all n-day vulnerabilities (95%) were exploited within six months of the patch, indicating an acceleration in attacks on vulnerable systems.
Examples of Successful Attacks
The vulnerability CVE-2023-28121 (CVSS score: 9.8) in the WooCommerce Payments plugin for WordPress serves as an example of how mass exploitation began several months after the flaw was disclosed. The first recorded use of the vulnerability only occurred after a convenient attack tool was made available, enabling malicious actors to launch millions of attacks per day.
Conversely, the vulnerability CVE-2023-27997 (CVSS score: 9.8) in FortiOS garnered significant attention immediately upon discovery, but its exploitation did not commence for several months. The complexity of the attacks and additional system protection measures delayed the flaw’s exploitation and limited its overall scale.
Mandiant also reported an expansion in the number of companies targeted by attacks. In 2023, the list of vulnerable vendors grew by 17% compared to 2021. While long-dominant players like Microsoft, Apple, and Google remain among the most frequently attacked, their share has fallen to less than 40%. Increasingly, lesser-known vendors are becoming the focus of attacks, broadening the range of targets and complicating defenses against threats.
Mandiant underscores that despite the rise in zero-day attacks, n-day vulnerabilities remain a significant concern. In the future, further reductions in time-to-exploit are anticipated, forcing companies to improve detection systems and swiftly apply patches. The growing complexity of infrastructures also demands stronger access controls and segmentation measures to minimize the impact of successful attacks.


