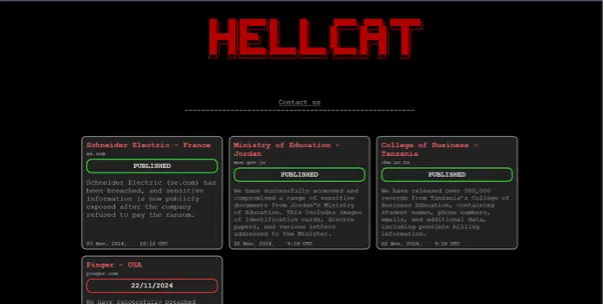
The Hellcat cybercrime group continues its relentless assaults on critical organizations, intertwining extortion with mockery to humiliate its victims. Among its latest attacks is the breach of Schneider Electric, where the hackers demanded a ransom payment of “125,000 baguettes” in a brazen display of derision.
Operating under the Ransomware-as-a-Service (RaaS) model, Hellcat provides encryption tools and attack infrastructure in exchange for a share of the profits. Researchers have linked the group to high-profile members of BreachForums. Like other ransomware syndicates, Hellcat employs double extortion tactics—first exfiltrating sensitive data before encrypting systems and threatening to publish stolen information if the ransom remains unpaid.
What sets Hellcat apart is not only its aggressive tactics but also its deliberate efforts to humiliate its victims. In the case of Schneider Electric, the attackers claimed to have stolen 40GB of internal data before leaking 75,000 employee email addresses and names online. The ransom demand in baguettes was a calculated insult aimed at the French corporation.
According to researchers at Cato Networks, the breach of Schneider Electric was facilitated through a previously unknown vulnerability in Atlassian Jira, underscoring Hellcat’s reliance on exploiting zero-day flaws in corporate systems.
On the same day Hellcat announced the Schneider Electric breach, it also claimed responsibility for compromising Jordan’s Ministry of Education and leaking 500,000 records from the Tanzania College of Business, including students’ personal and financial data.
Later in November, Hellcat listed root access to an American university’s server—linked to an institution generating over $5.6 billion in annual revenue—for sale at $1,500. This would have granted any interested hacking group an opportunity to compromise student records, financial systems, and other critical assets.
Among the group’s other high-profile attacks was the breach of Pinger, a U.S. telecommunications company. Hellcat claimed to have stolen 111GB of data, including 9 million user records, private messages, voice recordings, and proprietary source code. However, the status of the ransom demand and the authenticity of the stolen data remain unverified.
In December, Hellcat escalated its operations, attempting to sell root access to the server of a French energy company for $500, as well as breaching a municipal administration system in Iraq, a clear attempt to target critical infrastructure.
The Hellcat group epitomizes the growing menace of cyber extortion, with its added element of public humiliation making it an especially formidable and dangerous actor in the cyber threat landscape.