Mindmap of malware campaign
YouTube has become the target of a new phishing campaign aimed at content creators. An unidentified group is employing automated infrastructure to send fraudulent offers of collaborations and advertising deals. Successful attacks result in victims losing access to their accounts and confidential data.
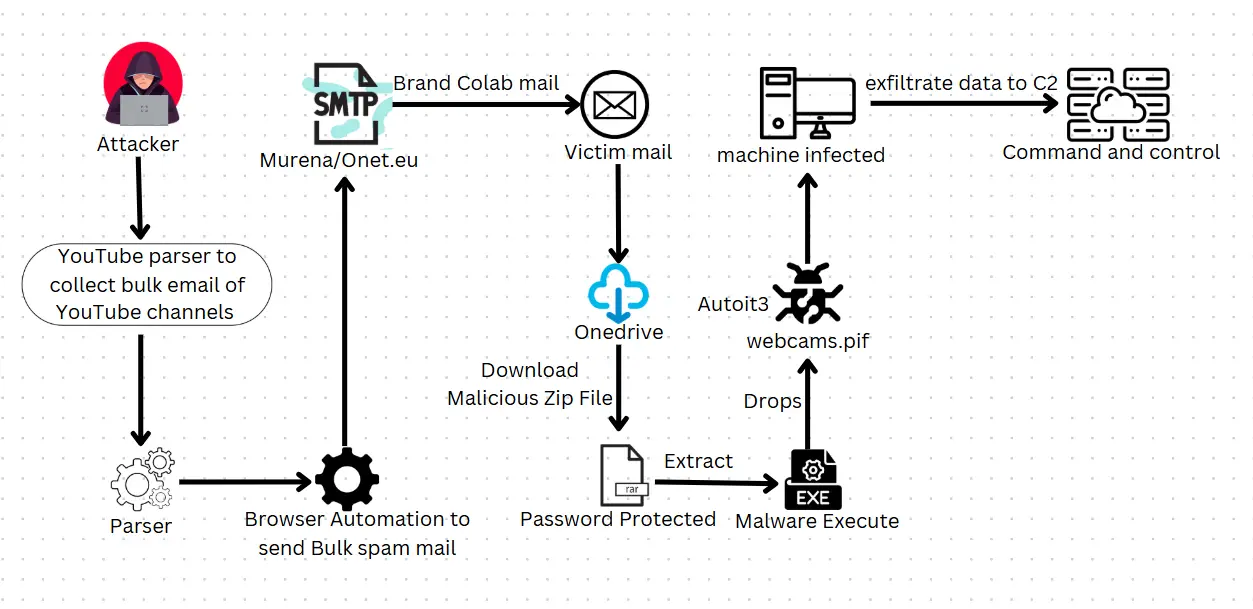
According to the analytics platform CloudSEK, the attackers have sent malicious emails to over 200,000 YouTube users. The campaign leverages 340 SMTP servers, each dispatching up to 1,000 emails from a single address. Masquerading as offers from well-known brands, the emails entice victims with promises of payment for short advertisements, but instead deliver malicious payloads.
The harmful links are meticulously disguised as attachments in Word, PDF, or Excel formats. These files, hosted on legitimate platforms like OneDrive and password-protected to bypass antivirus checks, deliver the Lumma Stealer malware upon being opened.
CloudSEK expert Mayank Saharia explained that the emails originate from spoofed or compromised addresses, making them appear credible. Once deployed, the malware steals passwords, financial data, and provides remote access to infected systems.
To collect target email addresses, the attackers use scrapers that automatically extract contact information from YouTube channels. The mass phishing campaign is automated using platforms such as Murena and Onet.eu, with templates employed to create temporary accounts and messages, effectively impersonating PR and media agencies.
The attack infrastructure comprises over 340 SMTP servers, 26 SOCKS5 proxy networks, and 46 remote desktops to obfuscate their operations. Researchers gained access to Murena.io accounts, confirming the scale of the campaign.
The attackers primarily target marketing and sales professionals in leadership roles, as they are more likely to engage with collaboration offers.
When the malicious file is executed, Lumma Stealer downloads additional components, including “webcams.pif” and “RegAsm.exe,” while disabling antivirus solutions. Lumma Stealer operates as a subscription-based service for information theft, harvesting passwords, cryptocurrency wallet data, and other sensitive files, while also enabling remote control of the compromised device.
Experts warn of the necessity for heightened vigilance when receiving emails with attachments or offers from unfamiliar senders. The scale and sophistication of the campaign underscore the attackers’ professional-level preparation and resources.


