A shadow market has long existed and thrived in the dark web, significantly fueling the entire cybercrime industry. The focus here is on XSS.is — an exclusive forum that has been actively attracting the attention of advanced hackers. Recently, it was revealed that access to accounts on this forum has suddenly become a currency among digital criminals.
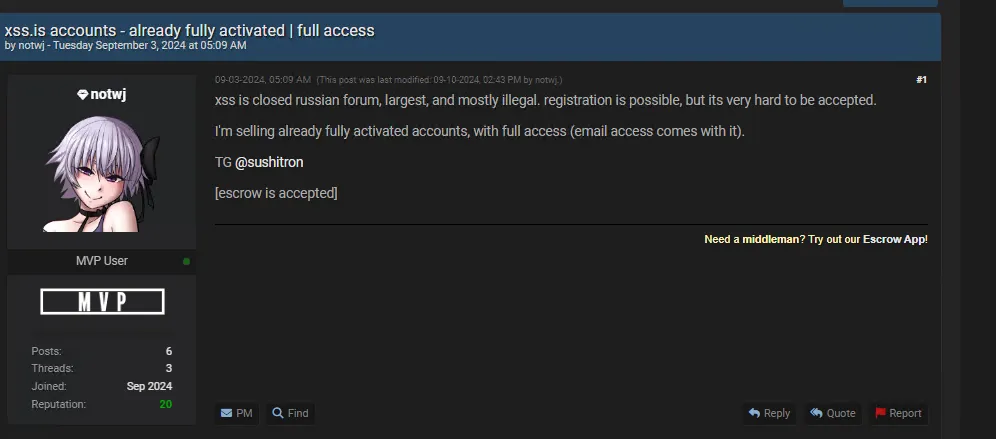
In September 2024, on BreachForums, another cybercriminal forum, a user under the alias “notwj” posted an offer to sell fully activated XSS.is accounts with email access. This offer sparked a frenzy within the cybercrime community. It’s important to note that XSS.is is known for its rigorous vetting process for new members.
The forum requires potential members not only to possess technical skills but also to have a verified reputation in the cybercrime sphere. Candidates must undergo challenging tests involving coding tasks and must be recommended by existing members.
The sale of XSS.is accounts opens the doors to the forum and its software and resources for less skilled, yet equally dangerous hackers, potentially shifting the balance of power in the world of cyber threats. However, the forum’s reputation has taken a considerable hit after this incident.
The sale of XSS.is accounts carries serious implications for cybersecurity. Even novice criminals can now gain access to tools and techniques previously reserved for the elite. This broadens the potential attack surface, creating additional challenges for companies and organizations. Furthermore, it may lead to the emergence of a new underground service — providing access to exclusive forums and platforms.
For law enforcement, the situation becomes more complex: the increasing number of participants in these closed cybercriminal circles could disrupt ongoing investigations and make intelligence gathering more difficult.
Thus, the sale of XSS.is accounts marks a significant turning point in the evolution of cybercrime. This development could not only disrupt established hierarchies but also make sophisticated cyberattacks accessible to a wider range of malicious actors.


