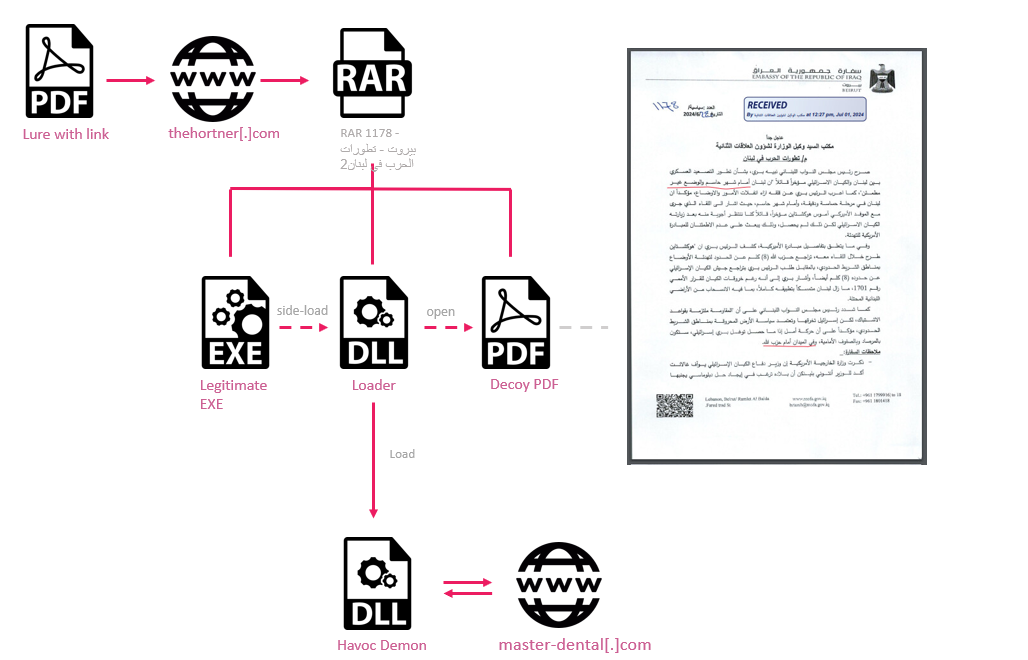
Havoc Infection Chain
Hackers affiliated with Hamas have expanded their digital assault strategies beyond cyberespionage, launching destructive campaigns against Israeli organizations. The activities of the threat actor, known as WIRTE, have also targeted the Palestinian Authority, Jordan, Iraq, Saudi Arabia, and Egypt, according to a recent report by Check Point.
Despite the ongoing conflict between Israel and Hamas, WIRTE’s operations have not subsided. They continue to exploit current events as a pretext for espionage and attacks on Israeli targets. In recent months, the hackers have executed at least two waves of destructive attacks aimed at Israeli organizations.
Active since August 2018, WIRTE is part of the so-called “Gaza Cyber Gang,” also known as Molerats or TA402. This group employs a variety of malicious tools, including BarbWire, IronWind, and Pierogi, to carry out attacks across the Middle East.
Experts note that the group leverages regional tensions to disseminate malicious archives containing the IronWind loader and the Havoc framework. In October 2024, a phishing campaign was uncovered targeting Israeli hospitals and municipalities. Emails were sent from an address associated with an ESET partner in Israel and contained an updated version of the SameCoin Wiper ransomware.
This malicious software is capable of destroying files and changing desktop backgrounds to images featuring the insignia of Hamas’s military wing, the al-Qassam Brigades. Previously, the wiper was used to sabotage Windows and Android devices, masquerading as security updates.
The hackers continue to evolve their arsenal of tools, which includes spyware, backdoors, and phishing pages, enabling them to combine espionage with destructive attacks on critical infrastructure.


