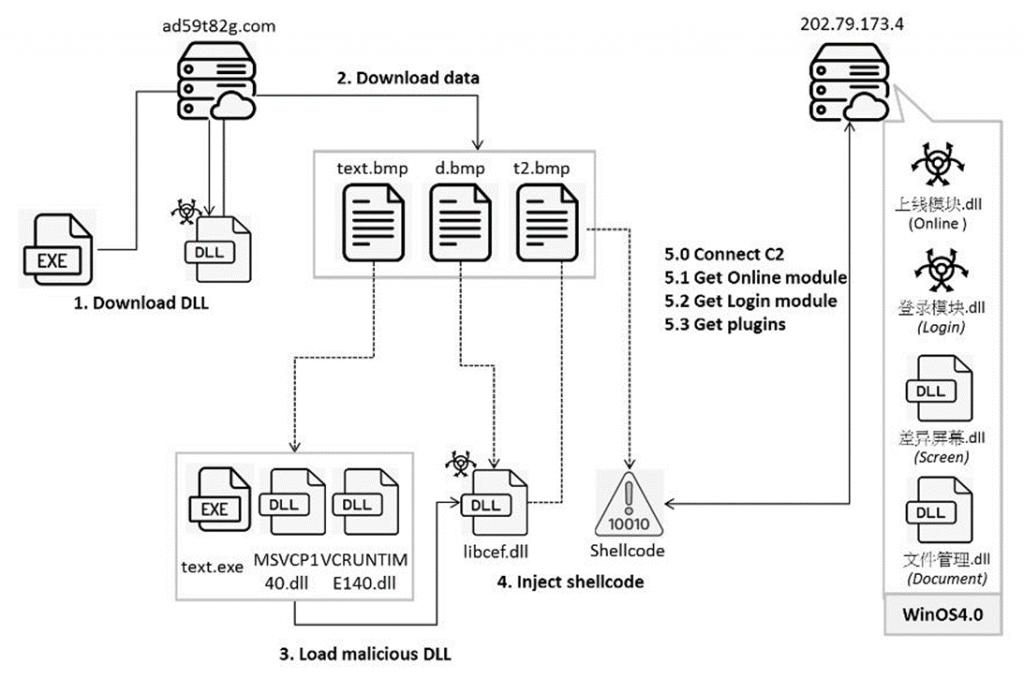
Attack chain
Cybersecurity researchers report that the notorious malware framework Winos4.0, previously observed in various cyberattacks, is now being distributed through gamer applications, including installation, acceleration, and optimization tools for games.
According to Fortinet, Winos4.0 is based on Gh0st RAT and features a modular architecture, allowing attackers to efficiently control numerous devices and execute a variety of commands. Experts from Trend Micro and KnownSec 404 Team detected activity related to Winos4.0 as early as June, with the dissemination campaigns dubbed Void Arachne and Silver Fox.
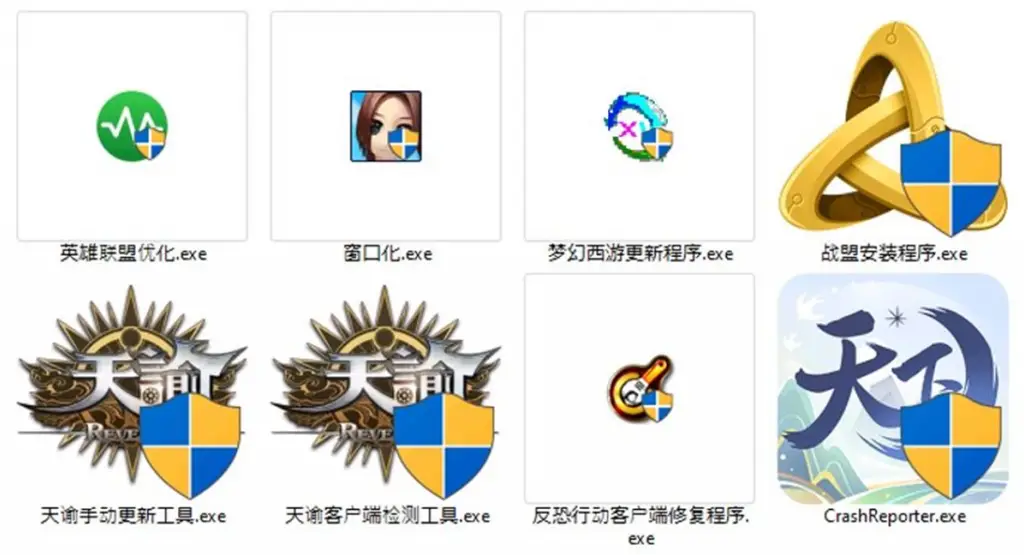
The attacks primarily target Chinese-speaking users, utilizing black hat SEO, social media, and the Telegram messenger to propagate the framework.
The infection mechanism begins with the download of a fake BMP file from a remote server, which is then decoded into a DLL library. This file creates an environment for loading additional malicious components, including executables and extra libraries, such as “libcef.dll.”
A DLL named “学籍系统” (translated as “Student Registration System”) hints at a possible intention to target educational institutions. During operation, Winos4.0 establishes a connection with a command server, receiving instructions to perform malicious actions like gathering system information and extracting data from cryptocurrency wallets such as OKX Wallet and MetaMask.
The Winos4.0 framework also supports the loading of additional plugins, enabling attackers to take screenshots and transmit confidential documents. Fortinet describes Winos4.0 as a powerful tool, comparable to Cobalt Strike and Sliver, capable of managing infected systems and providing deep access to user data.
Not all helpers and optimizers are as benign as they seem: often, seemingly harmless gaming utilities conceal potent tools for surveillance and data theft. Exercise caution, as each thoughtless download could result in data loss and financial harm.


