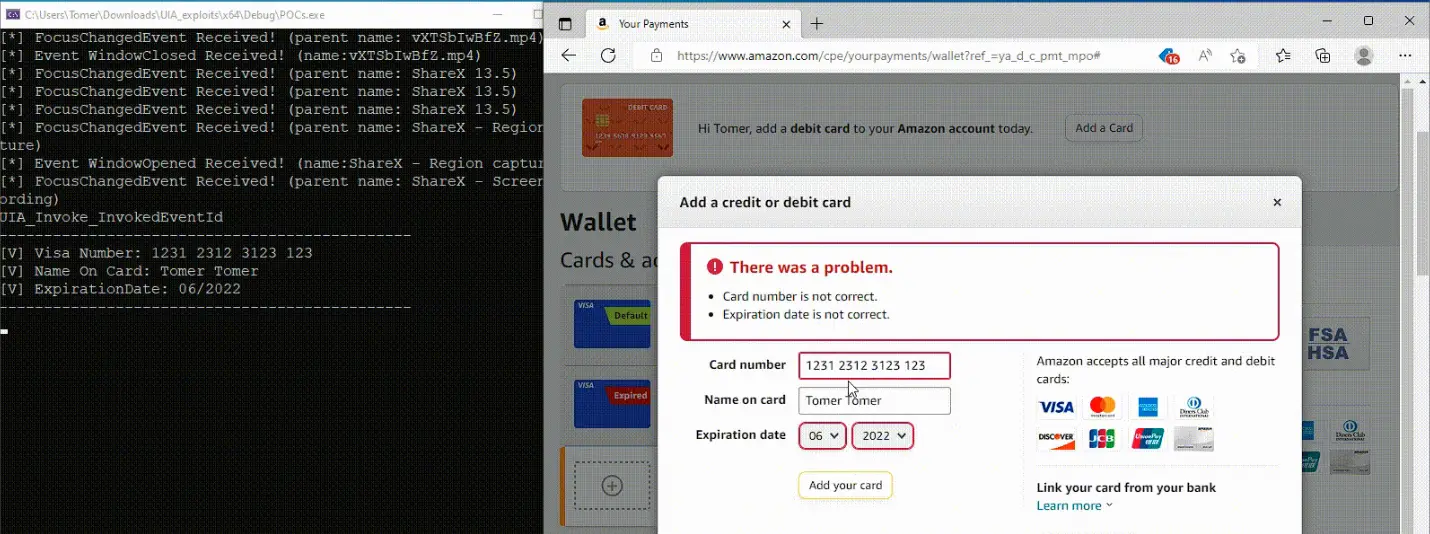
Harvesting credit card information from the browser
Researchers at Akamai have discovered that threat actors are exploiting the built-in Windows UI Automation (UIA) framework, originally designed for interacting with user interface elements, to execute malicious actions covertly. This technique enables attackers to bypass detection systems such as Endpoint Detection and Response (EDR) solutions.
UIA, first introduced with Windows XP as part of the .NET Framework, was developed to assist users with disabilities and facilitate automated testing. However, its capabilities also allow malicious actors to access sensitive data, redirect browsers to phishing sites, and execute hidden commands.
According to the researchers, leveraging this technique requires only convincing the victim to run a specially crafted program that utilizes UI Automation. This permits attackers to interact with interface elements of other applications, intercept messages from messaging platforms, and even send messages without displaying them on the screen.
The framework’s functionality relies on the Inter-Process Communication (IPC) Component Object Model (COM), enabling it to manipulate the user interface of applications in focus. The permissions and privileges granted to UIA are considered standard system functions.
The researchers also noted that preloaded interface elements cached within the system allow attackers to intercept messages not visible on the screen and send text without altering the visible interface. These capabilities make the technique particularly dangerous for corporate applications such as Slack and WhatsApp.
Each described scenario essentially represents the normal functionality of UI Automation, the researchers emphasized. Microsoft has stressed that applications utilizing UIA must possess specific privileges. However, attackers have found ways to circumvent these safeguards, leveraging the framework for malicious purposes.
This technique is reminiscent of attack strategies involving the Accessibility Services API in Android, which is frequently used to steal data from compromised devices. The primary issue lies in the fact that, in Windows, security systems identify UIA actions as legitimate functions rather than potential threats.
The exploitation of UI Automation illustrates how standard operating system features can be repurposed for covert attacks, remaining undetected by antivirus software. Experts recommend heightened vigilance towards such mechanisms and restricting their use on corporate devices.


