Experts from JPCERT conducted a study that enables the identification of ransomware attacks through the analysis of Windows event logs. Typically, one of the most challenging tasks in detecting such attacks is determining the attackers’ entry vector.
The analysis of potential vulnerabilities, such as VPN devices, often takes considerable time, especially when there are multiple possible points of entry. Therefore, effective detection begins with identifying the attacker group by examining encrypted files and ransom notes left on the infected device.
However, as the experts point out, it is not always possible to identify an attack based solely on these artifacts. Consequently, they decided to explore whether information from Windows event logs could be used to determine the type of ransomware involved.
The study confirmed that some ransomware programs leave distinct traces in Windows event logs, making it possible to identify them. The analysis focused on four primary Windows event logs: Application Log, Security Log, System Log, and Setup Log, as well as several ransomware families.
Conti
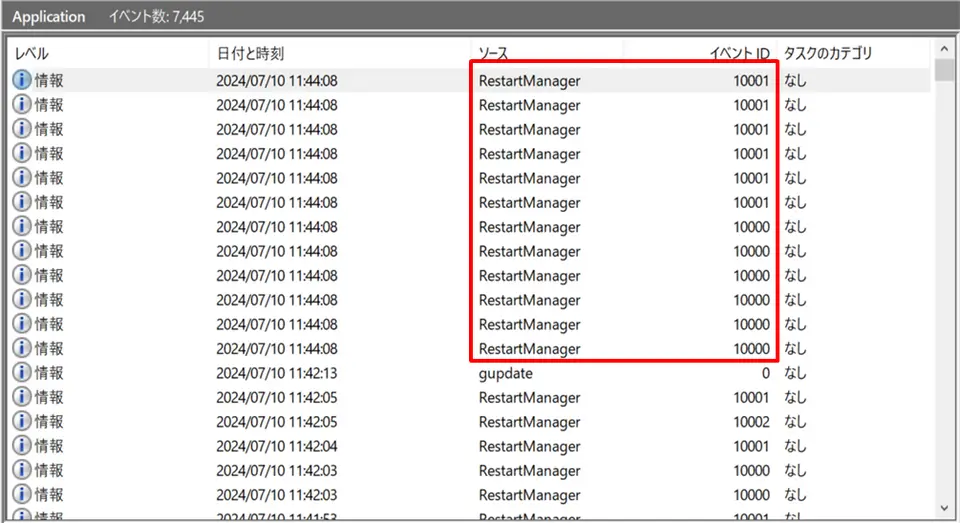
One of the first ransomware programs detected in the logs was Conti. This ransomware was first identified in 2020, and in 2022, its source code was leaked, leading to numerous modifications. During file encryption, Conti uses the Restart Manager function, resulting in a large number of events (ID: 10000, 10001) being recorded in a short period.
Additionally, similar events are logged by other programs related to Conti, including Akira, Lockbit3.0, HelloKitty, Abysslocker, Avaddon, and Bablock.
Phobos
Phobos is a ransomware program first identified in 2019. It is capable of deleting shadow volume copies and system backup directories on infected devices, leaving characteristic traces:
– ID 612: Automatic backup was canceled.
– ID 524: System directory was deleted.
– ID 753: Backup system successfully started.
Similar traces can also be found in the logs of other programs related to Phobos, such as 8base and Elbie.
Midas
Midas is another ransomware program, first identified in 2021. Its distinctive feature is that it leaves traces in the logs indicating changes in network service settings, which may suggest attempts to spread the infection.
BadRabbit
The study also uncovered characteristic traces in the logs associated with BadRabbit. BadRabbit’s status as a ransomware program was first confirmed in 2017. Its unique trait is that it records entries (ID: 7045) related to the injection of the cscc.dat component for data encryption.
Bisamware
Bisamware is a ransomware program identified in 2022. It targets Windows users and spreads through vulnerabilities in Microsoft tools. When executed, it logs the start (ID 1040) and completion (ID 1042) of the Windows installer transaction.
Common Signs in Logs
Ransomware types such as Shade, GandCrab, AKO, Avoslocker, BLACKBASTA, and VICE SOCIETY share common characteristics in event logs (ID: 13, 10016), indicating issues with access to the COM server related to the Volume Shadow Copy Service.
For some older ransomware programs, such as WannaCry, Petya, and Ryuk, researchers were unfortunately unable to identify clear signs in event logs. Nevertheless, the discovery of such patterns may significantly accelerate the detection of malware infections in the future.
The analysis of Windows event logs opens new possibilities in the fight against cybercrime, demonstrating that even the most sophisticated attackers leave digital traces. This approach not only speeds up the identification of threats but also highlights the importance of continuous monitoring and analysis of system logs as an integral part of a cybersecurity strategy.


