Google experts documented several cyberattacks on Mongolian government websites between November 2023 and July 2024. Hackers exploited vulnerabilities in iOS and Android to steal user data.
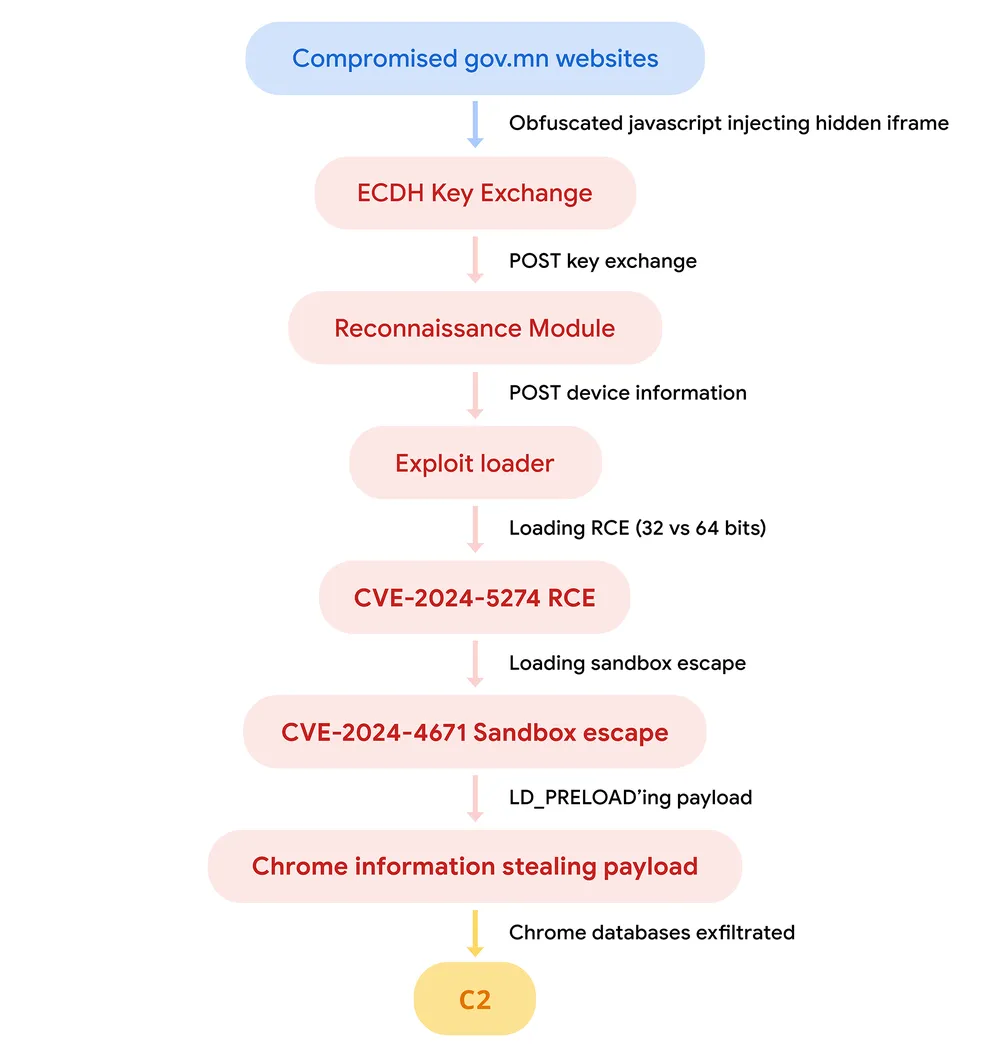
The watering hole attacks involved attempts to compromise users through exploits disseminated via infected websites. Cybercriminals initially targeted iOS users running versions below 16.6.1 by deploying a WebKit exploit. Through compromised websites, malicious code designed to steal cookies was distributed. Subsequently, the hackers shifted their focus to Android users, employing an exploit chain for the Chrome browser, specifically targeting versions m121-m123. These exploits took advantage of vulnerabilities for which patches had already been released but remained hazardous for unpatched devices.
In both campaigns, the attackers utilized exploits similar to those deployed by commercial entities such as Intellexa and NSO Group, known for developing spyware.
Hidden iframes were embedded in Mongolian government websites (cabinet.gov.mn and mfa.gov.mn), which loaded content from a hacker-controlled site. These iframes delivered the CVE-2023-41993 exploit, which stole cookies from iPhone users running older iOS versions. In the case of Android, the hackers employed JavaScript to redirect users to a third-party site, from which the Chrome exploit chain was deployed. This chain included the CVE-2024-5274 and CVE-2024-4671 vulnerabilities, enabling the attackers to exfiltrate information from the devices.
Google promptly notified Apple, Google, and Mongolia’s CERT about the discovered threats, which helped to resolve the issue. However, it remains unclear how the hackers obtained access to the exploits originally developed by commercial companies.


