VEILDrive
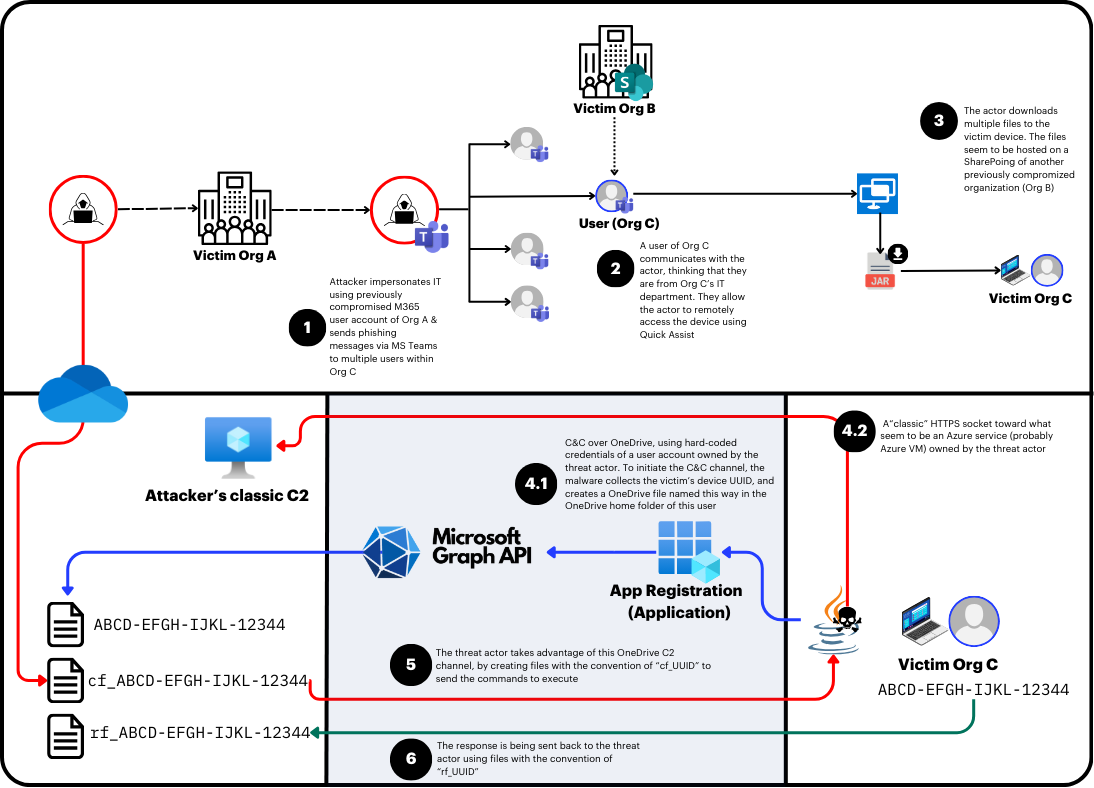
The Israeli cybersecurity company Hunters has detected activity from the cyber group VEILDrive, which utilizes legitimate Microsoft services — Teams, SharePoint, Quick Assist, and OneDrive — to launch phishing attacks and distribute malware. Specialists uncovered this campaign in September 2024 while investigating an incident in a critical U.S. infrastructure organization, designated “Organization C.”
The cyberattack began in August and culminated in the deployment of Java-based malware that leverages OneDrive for command-and-control infrastructure. Attackers sent messages through Teams to employees of “Organization C,” impersonating IT specialists and requesting remote access via Quick Assist.
A distinctive aspect of the attack was the use of an existing victim account from “Organization A,” rather than creating a new one. This tactic allowed them to bypass standard security measures through Microsoft Teams’ external access feature, which by default enables communication with users from other organizations.
The next stage involved sending a download link for an archive file through SharePoint. This archive contained the LiteManager remote access program, which cybercriminals used to create scheduled tasks and further monitor the system. Additionally, they uploaded a second ZIP file containing Java Archive (JAR) malware, enabling it to connect to an attacker-controlled OneDrive account and execute PowerShell commands via the Microsoft Graph API.
The attackers also implemented a backup mechanism — connecting to a remote Azure virtual machine over HTTPS to receive and execute commands on the system.
This attack is not the first to exploit Quick Assist for fraudulent purposes. In May 2024, Microsoft warned of abuse of this service by the Storm-1811 group, who posed as support staff to distribute the Black Basta ransomware.
In recent months, there has also been a surge in the use of SharePoint and OneDrive to evade security systems. Hunters notes that this strategy is based on a simple and structured codebase, making real-time detection of malware significantly more challenging and rendering it unusually “transparent.”


