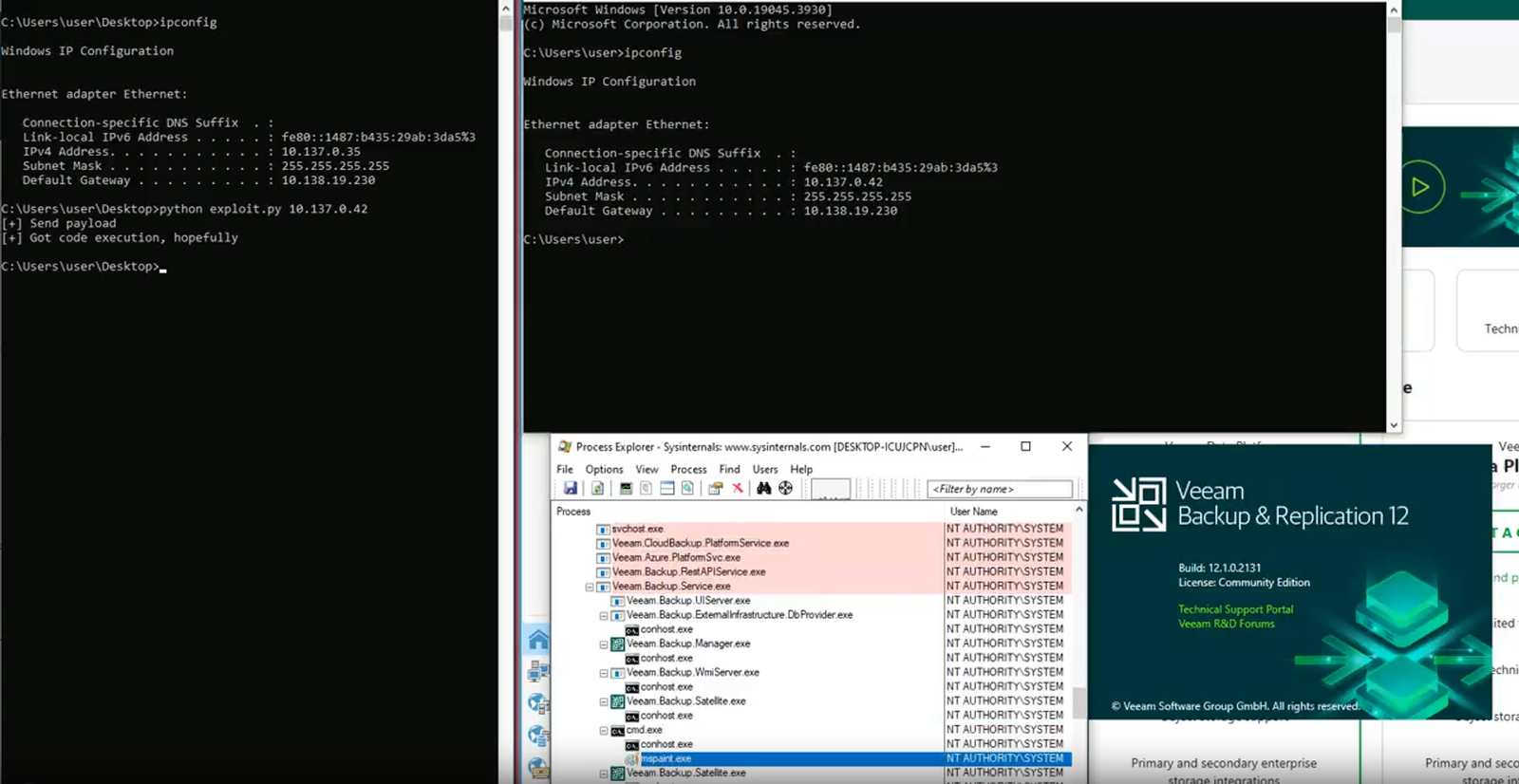
Security researchers from Sophos X-Ops have discovered that hacking groups are actively exploiting a critical vulnerability in the Veeam Backup & Replication (VBR) system, enabling attackers to remotely execute code on vulnerable servers.
The security flaw, identified as CVE-2024-40711, was initially uncovered by security researcher Florian Hauser. The vulnerability stems from the deserialization of untrusted data, allowing unauthenticated attackers to carry out low-complexity attacks.
Veeam acknowledged the vulnerability and released security updates on September 4, 2024. A technical analysis of the vulnerability was later published by experts from watchTowr Labs, who postponed the release of proof-of-concept code until September 15 to give administrators time to mitigate the threat.
VBR, a popular solution for data protection and disaster recovery, has become a prime target for hackers seeking access to company backups. Over the past month, Sophos X-Ops specialists observed that the CVE-2024-40711 vulnerability was being actively exploited in attacks involving the Akira and Fog ransomware. Attackers, after gaining access via compromised credentials, created local accounts with administrative and Remote Desktop user privileges.
In one instance, hackers used Fog to attack a Hyper-V server and then leveraged the rclone utility to exfiltrate data. Around the same time, an attempt was made to deploy the Akira ransomware. Notably, all these incidents shared indicators consistent with earlier attacks involving the same ransomware strains.
It is worth mentioning that in March 2023, Veeam had already patched another vulnerability—CVE-2023-27532—that had also been exploited in attacks targeting backup infrastructure. That vulnerability was observed in attacks by the FIN7 group, known for spreading notorious ransomware such as Conti, REvil, and others.
Veeam products are used by more than half a million customers worldwide, including 74% of companies in the Global 2000 list. This underscores the critical nature of attacks on VBR, as the compromise of such widely used software could lead to large-scale data breaches and disrupt the operations of major organizations across the globe.


