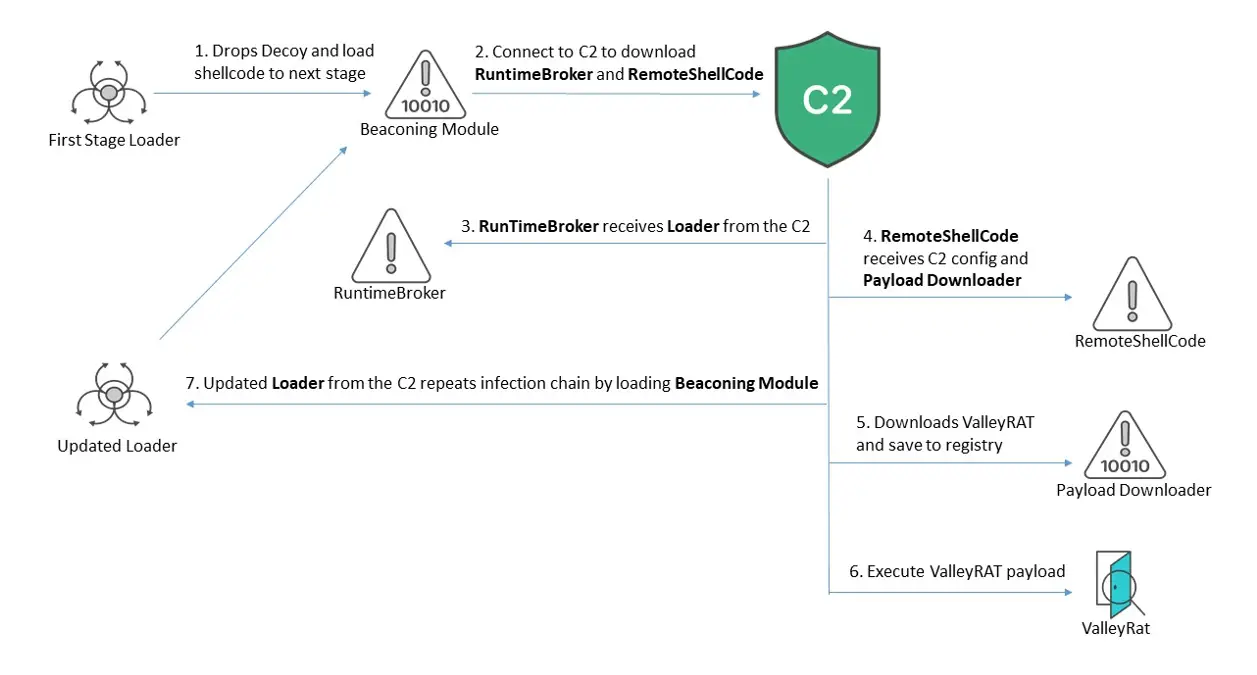
Recently, FortiGuard Labs uncovered a new ValleyRAT malware campaign targeting Chinese-speaking users. Historically, this malware has primarily targeted businesses in the e-commerce, finance, sales, and management sectors.
ValleyRAT is a multi-stage malware that employs various techniques to monitor and control its victims, as well as to deploy additional plugins to inflict greater damage. One of its key features is the active use of shellcode for executing components directly in memory, which significantly reduces the traces of its presence in the system.
To disguise itself, ValleyRAT uses icons of legitimate applications like Microsoft Office and file names associated with financial documents, making it more convincing to users. Upon execution, the program creates an empty file and opens it in a Microsoft Office application to create an appearance of legitimacy.
Once installed, ValleyRAT checks if it is running in a virtual machine, and if it detects signs of virtualization, it terminates its execution. Furthermore, the malware employs a “sleeping mode” technique to evade detection systems, complicating identification by antivirus programs.
During the initialization phase, ValleyRAT adds a task to the Windows Task Scheduler to ensure its automatic execution each time the user logs into the system. It also exploits known vulnerabilities in legitimate applications to gain administrative privileges without notifying the user.
ValleyRAT effectively bypasses antivirus systems, particularly those used in China, further underscoring its targeted focus on Chinese users. The malware kills antivirus processes, modifies their settings in the registry, and takes additional measures to remain undetected.
Moreover, ValleyRAT has the capability for remote command execution and downloading additional components from a command server, allowing attackers to gain full control over the infected system.
This malware can execute various commands, such as monitoring user activity and installing additional malicious modules, making it particularly dangerous for its victims.
Fortinet continues to monitor ValleyRAT’s activity and provides updates to protect its clients from this threat. Fortinet’s antivirus solutions, such as FortiGate and FortiMail, already include signatures to detect and block ValleyRAT.
To protect against such threats, it is recommended to regularly update antivirus software and increase user awareness of potential cyber threats.


