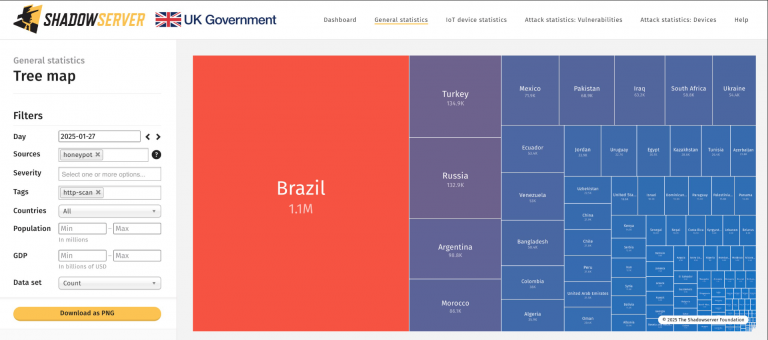
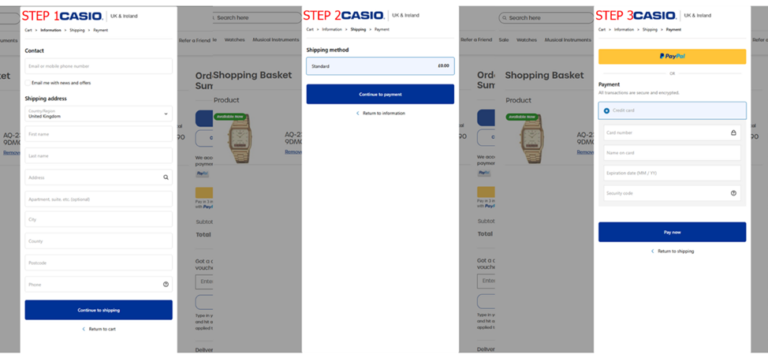
The United States Agency for International Development (USAID) fell victim to a cryptojacking attack, resulting in significant financial losses across its cloud services.
The incident occurred in the fall of 2024, when cybercriminals gained access to the agency’s test environment through a password spraying attack. After compromising a global administrative account, the attackers created an additional user profile and began mining cryptocurrency using USAID’s Microsoft Azure cloud infrastructure.
The unauthorized consumption of cloud resources led to an estimated loss of approximately $500,000. In response, the agency implemented stringent password policies, enforced mandatory multi-factor authentication (MFA), and enhanced security monitoring to mitigate further threats.
The exploitation of government computing resources for illicit cryptocurrency mining is not uncommon. For instance, in 2024, one such campaign targeted misconfigured Kubernetes clusters to mine Dero cryptocurrency.
According to experts, cryptojacking remains particularly challenging to detect, as perpetrators often erase traces of their activity and disable security mechanisms following a breach. Such attacks are frequently orchestrated by well-organized cybercriminal syndicates or state-sponsored hackers. North Korea is among the nations suspected of supporting these operations.
Mitigation strategies against cryptojacking include the mandatory adoption of multi-factor authentication and rigorous oversight of privileged accounts. In 2024, Microsoft announced plans to enforce MFA across Azure, though the deployment process only commenced later that year.