The open-source PHP package Voyager has been found to contain three critical vulnerabilities that allow arbitrary code execution on a server with a single click. Sonar security researcher Yaniv Mizrahi identified flaws affecting the file upload and processing functionality, as well as a module responsible for dynamic interactions within the administrative panel.
With an active Voyager account, merely clicking on a malicious link is enough to trigger the execution of concealed malicious code, which is disguised as a seemingly innocuous image or video file. The attack is further compounded by the ability to embed harmful scripts within polyglot files—files that appear harmless but can stealthily inject PHP code into the system.
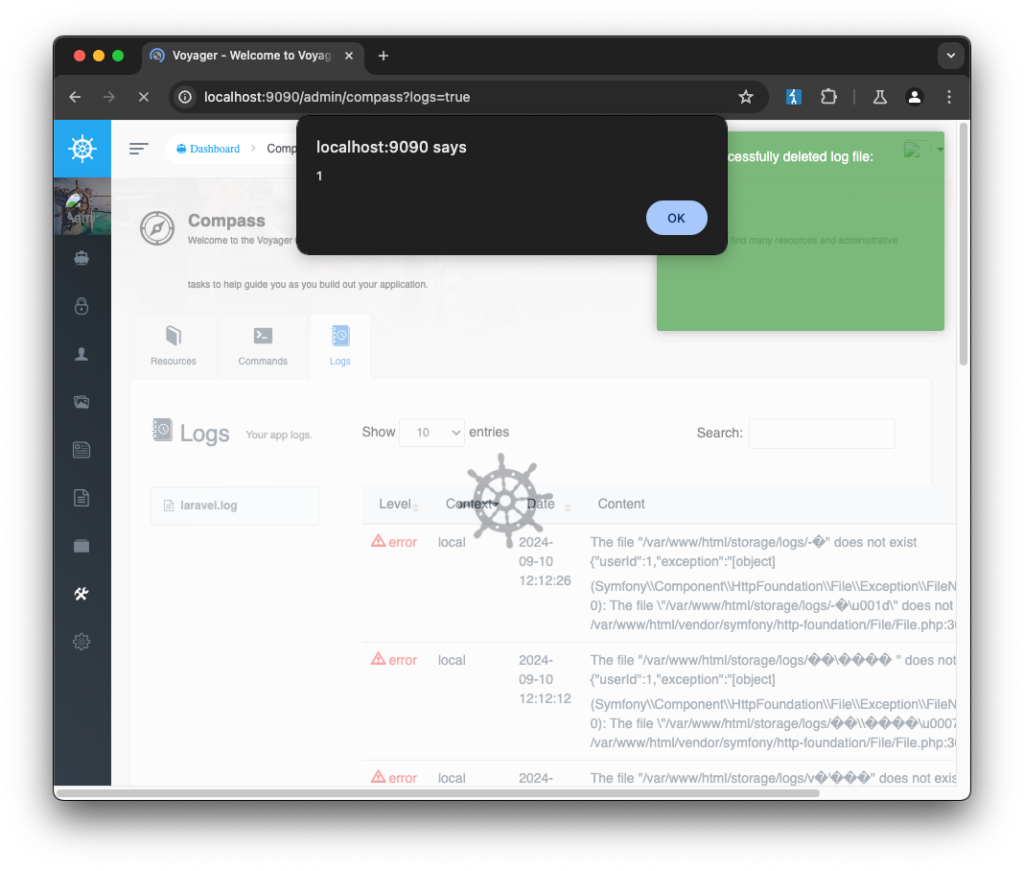
The identified vulnerabilities have been assigned the following CVE identifiers: CVE-2024-55417, CVE-2024-55416, and CVE-2024-55415. The first bypasses MIME type validation, allowing attackers to write files into arbitrary directories. The second enables JavaScript execution when a Voyager user clicks a malicious link within the “Compass” panel. The third flaw permits unauthorized file theft and deletion, granting attackers additional leverage. When combined with an XSS vulnerability, this creates a plausible scenario in which sensitive data can be extracted or erased simply by enticing a privileged user to click on a specially crafted URL.
The severity of the situation is exacerbated by the fact that an official patch has yet to be released, despite developers being notified of the issue in mid-September 2024. According to recent community reports, there is still no clear timeline for the release of a security update.
Late last year, a surge in vulnerabilities was observed across widely used open-source projects, with Python and JavaScript libraries facing similar security flaws. Many cybersecurity experts argue that more rigorous auditing of source code is essential to ensure that such security gaps are identified and addressed swiftly. Given the increasing frequency of supply chain attacks, projects that form the backbone of critical infrastructure must adhere to stricter testing and review protocols.
Developers utilizing Voyager are strongly advised to exercise caution, temporarily restrict access to file upload functionalities, and conduct thorough reviews of their source code. The growing demand for advanced vulnerability analysis tools reflects the heightened scrutiny surrounding open-source security, yet without timely patches, the risk remains significant.
The open-source community has increasingly called for a decentralized code review system to reduce the likelihood of such security lapses in the future. In light of recent attacks targeting source code repositories and the proliferation of malicious software packages, maintaining vigilance when working with any open-source libraries has become a fundamental security practice.
Until an official security update is available, it is strongly recommended to refrain from deploying Voyager in sensitive environments. Organizations that have already integrated the package are now intensifying internal security audits, implementing additional protective layers, and closely monitoring for unauthorized activity.
Mitigating these vulnerabilities requires a multi-layered security approach, including principle-of-least-privilege enforcement, network segmentation, and continuous log analysis. Such measures are particularly crucial in detecting and preventing unauthorized file uploads, ensuring a proactive defense until an official patch is released.