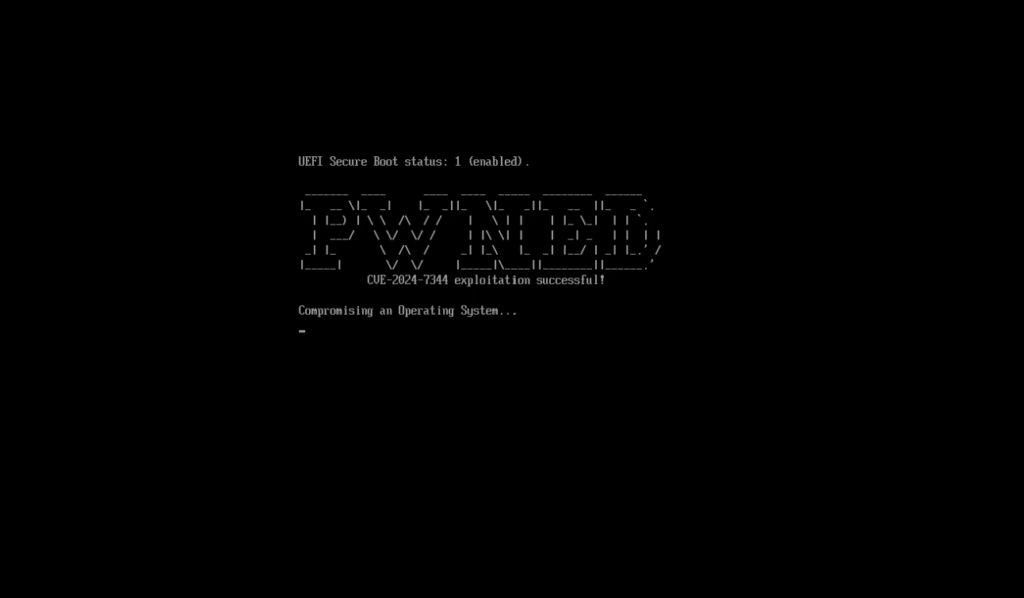
The CVE-2024-7344 vulnerability, associated with bypassing UEFI Secure Boot protection, presents a significant threat by enabling attackers to deploy bootkits even with Secure Boot enabled. The issue stems from an application signed by Microsoft, utilized in various third-party system recovery tools.
Bootkits pose a severe security risk as they operate before the operating system loads and can persist even after the OS is reinstalled, making them exceptionally difficult to detect. This vulnerability exploits a flawed PE loader, allowing the execution of arbitrary UEFI binaries while bypassing signature verification.
ESET researchers discovered that the application employs an unconventional loading method, manually decrypting and executing binary data from a file named “cloak.dat.” This bypass of security checks can be leveraged by threat actors to replace the OS loader and inject malicious files into the EFI partition.
The vulnerability affects system recovery, backup, and disk management tools, with the following products being identified as impacted:
- Howyar SysReturn (up to version 10.2.023_20240919)
- Greenware GreenGuard (up to version 10.2.023-20240927)
- Radix SmartRecovery (up to version 11.2.023-20240927)
- Sanfong EZ-back System (up to version 10.3.024-20241127)
- WASAY eRecoveryRX (up to version 8.4.022-20241127)
- CES NeoImpact (up to version 10.1.024-20241127)
- SignalComputer HDD King (up to version 10.3.021-20241127)
Notably, CVE-2024-7344 can be exploited even without these applications installed. Simply placing the vulnerable binary file, “reloader.efi,” along with a malicious “cloak.dat” file, is sufficient to compromise the system.
Microsoft addressed this vulnerability in its January 2025 update, revoking the certificates of affected applications to prevent their execution. The update is automatically applied to Windows users. ESET has also provided PowerShell commands to verify the successful implementation of these protections.
Experts strongly recommend updating the operating system and any affected applications to their latest versions promptly to eliminate any potential attack vectors.