Cisco Talos experts have identified a new wave of attacks by the UAT-5647 group (RomCom), targeting Ukrainian governmental bodies and unnamed Polish organizations since late 2023.
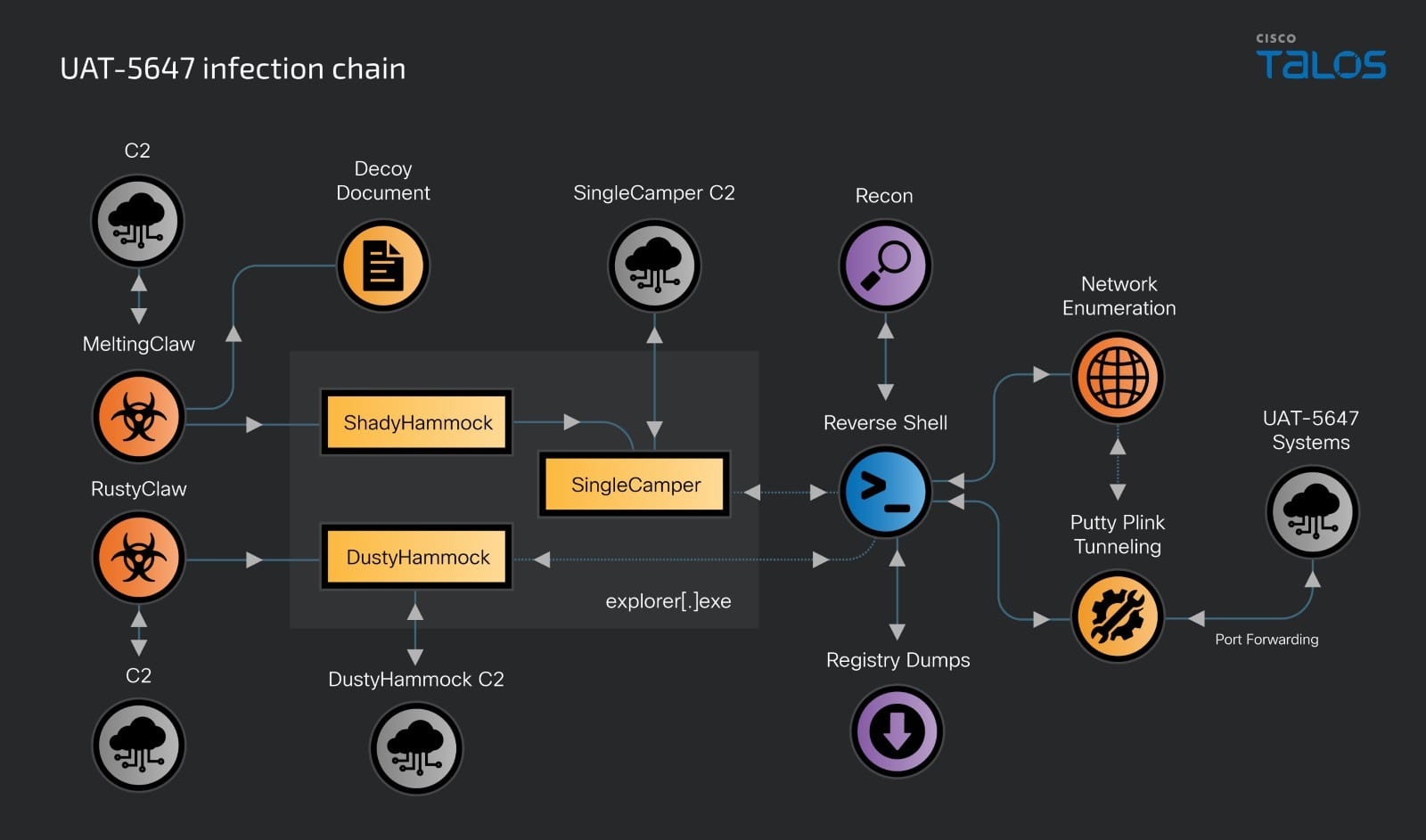
The latest campaign features an updated version of the RomCom malware, dubbed SingleCamper. The malware is loaded directly from the registry into the system’s memory and leverages the Loopback Address for communication with its loader. The UAT-5647 group’s toolkit has expanded significantly and now includes four malware families: two loaders and two backdoors.
Hackers are actively employing penetration techniques on border devices, redirecting traffic from internal interfaces to remote servers, complicating the detection process during incident response. Through these attacks, UAT-5647 aims to establish long-term access to targeted systems for data theft and may later resort to ransomware for financial gain.
The primary infection vector is phishing messages containing the RustClaw or MeltingClaw loaders, which facilitate the installation of the DustyHammock (Rust) and ShadyHammock (C++) backdoors. DustyHammock executes commands from the command center, while ShadyHammock activates malicious components and can receive commands via local interfaces.
Once inside the network, attackers conduct reconnaissance using tools like PuTTY Plink to create tunnels between internal interfaces and external servers. This tactic allows hackers to evade detection and gain access to confidential information and network device configurations, such as TP-LINK routers.
The group actively uses port scans and commands to analyze system information and network connections. Commands like “net view” and “ping” are executed on target devices to identify open ports and resources, enabling access to shared folders and critical information.
In this latest attack chain, UAT-5647 relies on multiple programming languages, including GoLang, C++, Rust, and LUA, to develop multifunctional malicious components. These malware programs are designed to gather data, download additional files, and activate PuTTY Plink for further lateral movement across the network.
Notably, SingleCamper can send commands to its loader, ShadyHammock, via a local interface, allowing remote control of the compromised system and the execution of commands at the system level without interacting with external servers.
The UAT-5647 attacks are ongoing, and Talos analysts predict that the group will intensify its efforts to gain long-term access and steal data while continuing to deploy ransomware to destabilize infrastructure and generate profit.


