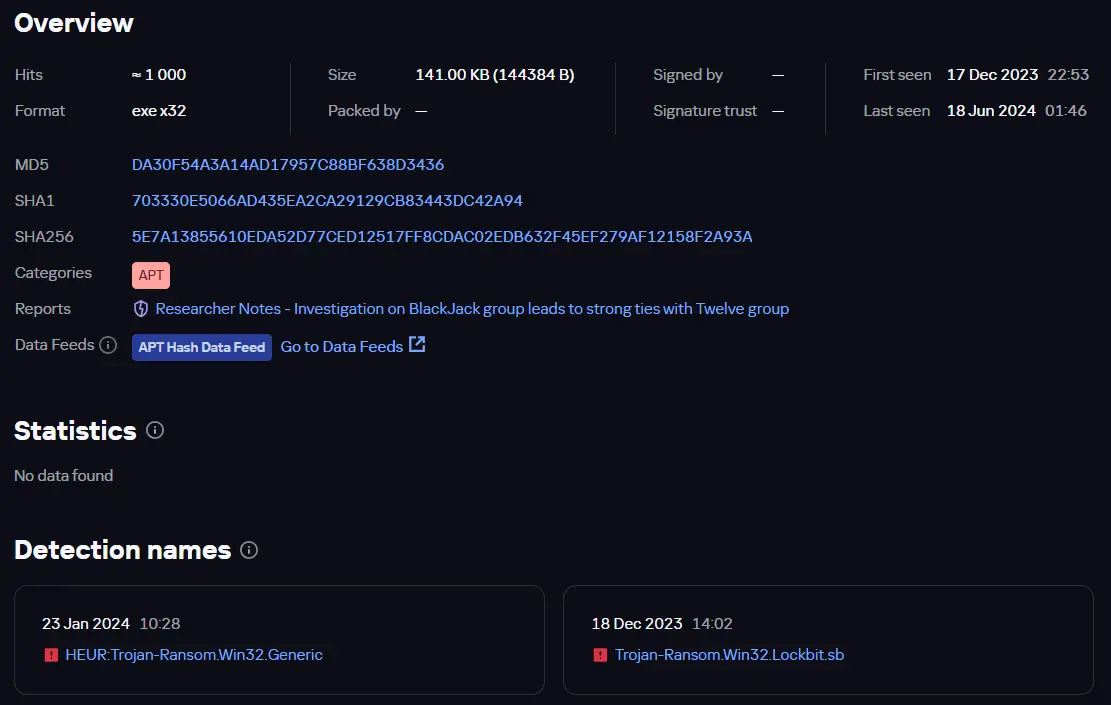
BlackJack file information
Kaspersky Lab has announced that two hacktivist groups—Twelve and BlackJack—may be operating within the same structure. According to research findings, both groups utilize similar malware and employ identical methods for its distribution and execution. These groups first became active at the end of 2023, launching attacks on companies based in Russia. Although the hackers present their actions as financially motivated, their primary goal appears to be data theft and the destruction of IT infrastructure.
BlackJack, one of the groups, uses publicly available software in its attacks, such as the SSH client PuTTY and the leaked wiper Shamoon, indicating their limited resources compared to larger cybercriminal organizations. In addition, they make extensive use of the LockBit ransomware, which was created using leaked source code, and employ the tunneling tool ngrok to maintain persistent access to compromised systems.
Both groups do not rely solely on malware. They also utilize legitimate tools and utilities, such as Radmin and AnyDesk, for remote system control. This extensive use of open and accessible tools makes their attacks less detectable in the early stages and complicates the tracking process.
Research has revealed that the attacks of both groups follow the same patterns: the malware is deployed in identical network directories, and execution is carried out via task schedulers. Additionally, the methods used to cover their tracks, such as clearing event logs using PowerShell, are identical for both groups.
Despite their attempts to portray their actions as financially motivated attacks, Twelve and BlackJack seem more focused on causing maximum disruption to the IT environments of their targeted organizations.


