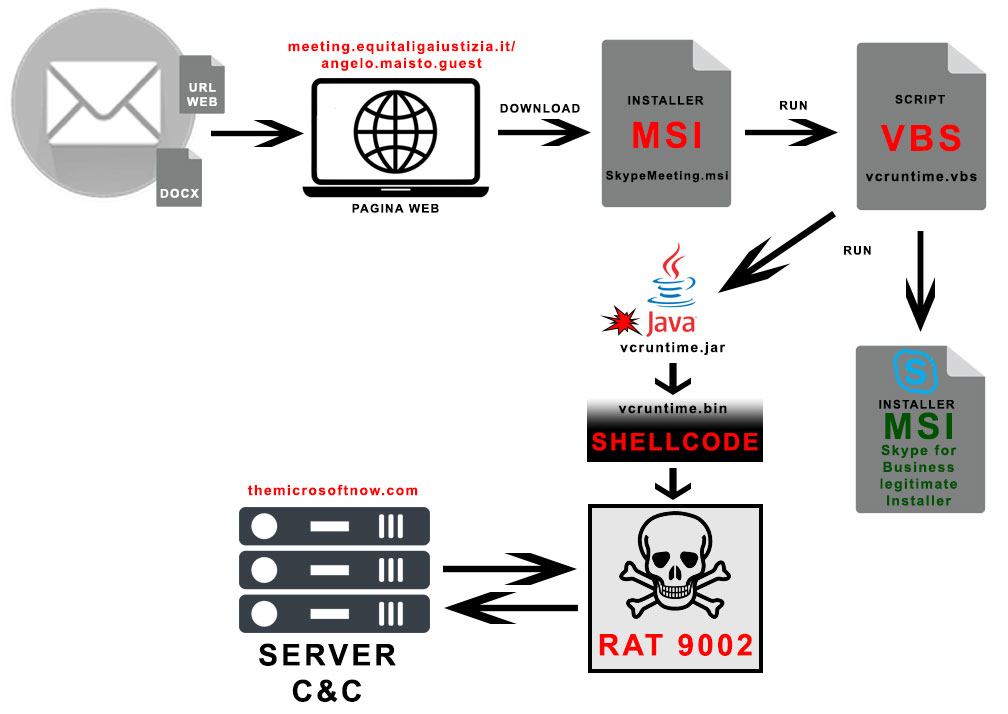
The infection chain
The Chinese hacker group APT17 targeted Italian companies and government institutions using a modified version of the notorious 9002 RAT malware, disguised as a Skype application. This was reported by the Italian company TG Soft in their recent report.
The attacks occurred on June 24 and July 2, 2024. In the first instance, the attackers used a Microsoft Office document, and in the second, a simple link. Both methods enticed victims to install a Skype for Business package via a fake domain that mimicked an official Italian resource: “meeting[.]equitaligaiustizia[.]it/angelo[.]maisto[.]guest”. Upon installation, victims received the 9002 RAT remote access Trojan on their computers.

APT17, also known as Aurora Panda and Bronze Keystone, was first described in 2013 by Mandiant. At that time, the hackers exploited vulnerabilities in Internet Explorer for cyber espionage. The 9002 RAT malware, also known as Hydraq and McRAT, first gained notoriety in 2009 during Operation Aurora, which targeted Google and other major companies.
In the recent attacks, the perpetrators used phishing methods to trick recipients into clicking the link and downloading the Skype for Business MSI installer. Running this installer executes a Java Archive (JAR) file through a Visual Basic (VBS) script, which simultaneously installs the legitimate Skype for Business to avoid arousing suspicion. The installed Java application then decrypts and runs shell code that activates the 9002 RAT.
The 9002 RAT is a modular Trojan capable of monitoring network traffic, taking screenshots, listing files, managing processes, and executing commands from a remote server to facilitate network reconnaissance. TG Soft noted that this malware is continuously updated, including fileless variants, which significantly reduce the likelihood of detection.
These incidents underscore the necessity of constantly updating security systems and training employees in cyber defense methods. With the increasing activity of hacker groups such as APT17, any company or government institution can become a target. Regular audits and awareness of current threats can significantly mitigate the risks of successful attacks.


