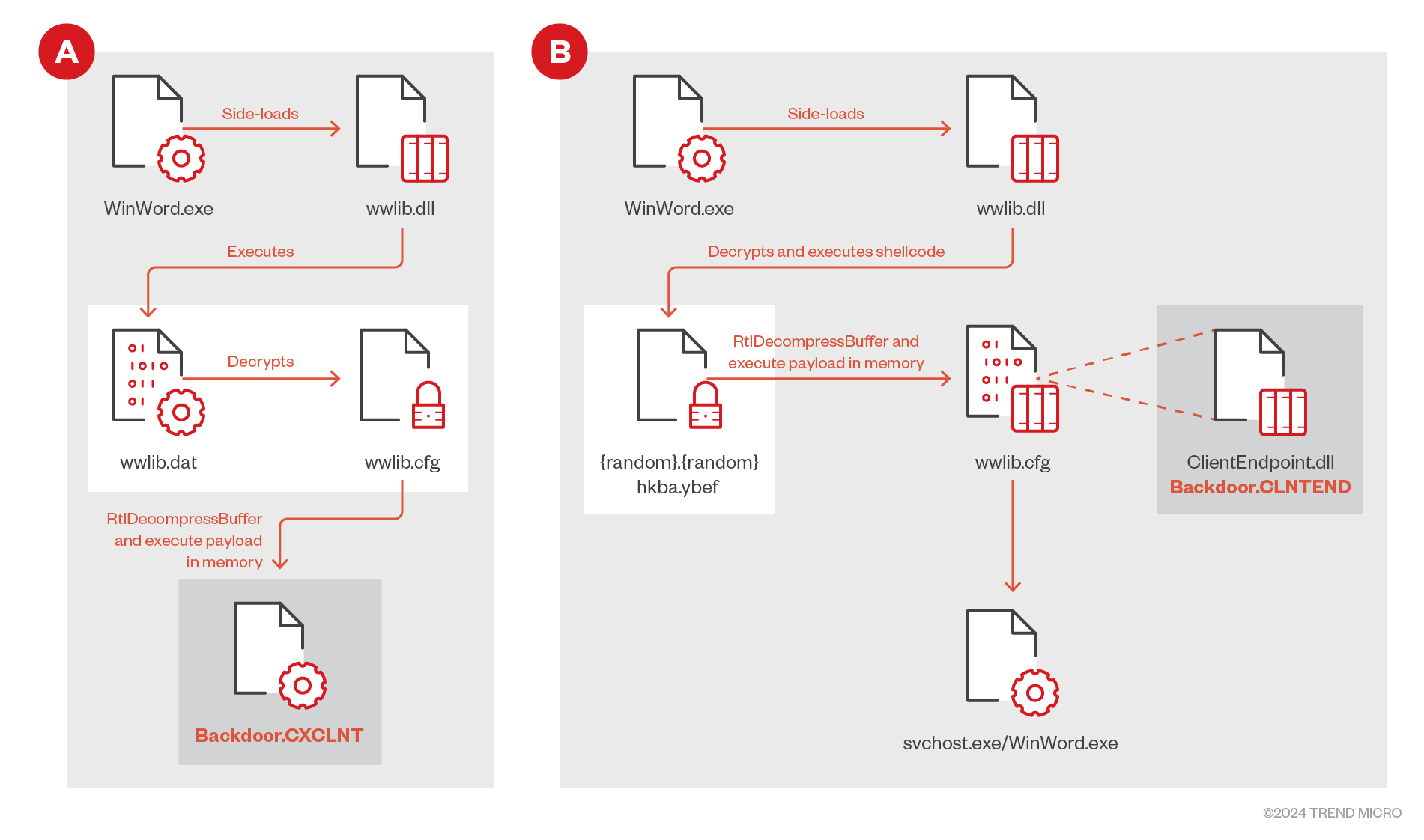
Execution flow between previous and recent activities involving CXCLNT and CLNTEND
An unknown cyber group, likely linked to Chinese-speaking hacker collectives, began actively targeting Taiwanese drone manufacturers in 2024. According to Trend Micro, the threat is being tracked under the name TIDRONE, with its primary focus being industrial espionage directed at military supply chains.
The exact method of infiltration into these companies’ systems has yet to be determined; however, researchers have identified the use of malware known as CXCLNT and CLNTEND. Both are distributed through remote desktop management tools such as UltraVNC and others.
A common characteristic among all victims was the presence of the same enterprise resource planning (ERP) software, which suggests the possibility of a supply chain attack.
Cyberattacks within the TIDRONE operation typically occur in three stages aimed at:
- Elevating privileges by bypassing User Account Control (UAC);
- Harvesting account credentials;
- Disabling antivirus software on compromised devices.
The deployment of the malicious programs is executed through the loading of a malicious DLL library via Microsoft Word, granting attackers access to confidential information.
CXCLNT can upload and download files, erase traces of its activity, gather system information, and initiate subsequent stages of the attack. CLNTEND, first detected in April 2024, possesses even more extensive capabilities, supporting multiple network protocols including TCP, HTTP, HTTPS, and SMB.
Researchers Pierre Li and Vicky Su from Trend Micro note that the alignment of file compilation times with the cyber group’s activity in previous espionage incidents confirms its connection to certain Chinese-speaking hacker groups.
This incident underscores the vulnerability of supply chains, particularly in sectors related to military technology.


