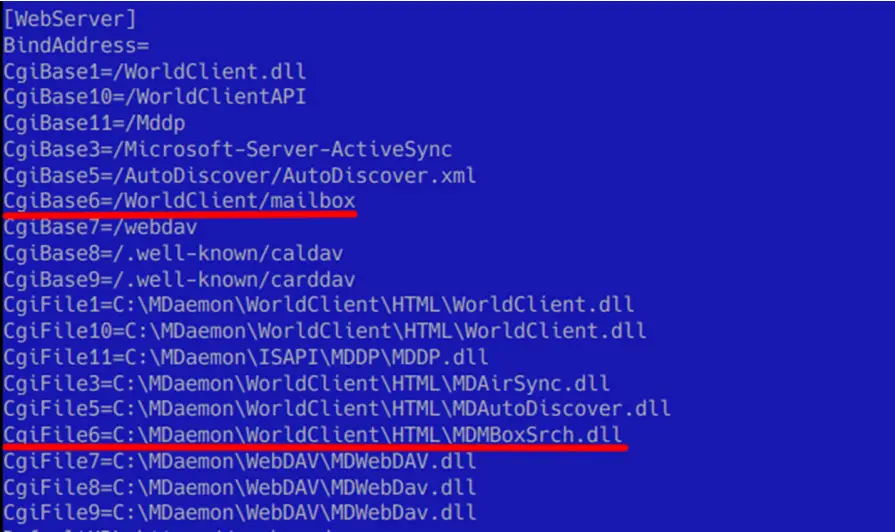
Sample of the WorldClient.ini file containing plugin entries
At the international Virus Bulletin conference, experts from Kaspersky Lab presented their research on The Mask (Careto) group, renowned for its sophisticated cyberattacks since 2007. This group has historically targeted diplomatic entities, governmental organizations, and academic institutions. After years of inactivity, The Mask has resurfaced, showcasing new and intricate methodologies.
One of the most notable incidents occurred in 2022, involving the compromise of an organization in Latin America. The attackers infiltrated an MDaemon mail server by injecting a malicious extension via the WorldClient component. This extension’s configuration enabled persistent access, allowing the perpetrators to control the infected infrastructure through HTTP requests.
The deployed malicious module, FakeHMP, offered a wide array of capabilities, including data harvesting, keystroke logging, screenshot capturing, and the deployment of additional malware. To propagate within the network, the attackers exploited a legitimate driver, hmpalert.sys, which facilitated the injection of malicious libraries into critical processes such as winlogon.exe. In 2024, researchers identified a similar infection technique, this time leveraging Google Updater instead of previously utilized task scheduler exploits.
Further analysis revealed that the same organization had been targeted in 2019 through the use of Careto2 and Goreto frameworks. Careto2 included modules for configuration management, file filtering, and data storage, while Goreto, written in Golang, enabled interaction with Google Drive for command execution. The persistence techniques employed included COM hijacking and the use of virtual file systems.
Notably, the file naming conventions and plugin structures observed in the 2019 attacks echoed those used in campaigns from 2007 to 2013. This, coupled with the unique attributes of the malicious payloads, allowed experts to conclusively attribute these modern attacks to The Mask group.
The Mask remains one of the most complex threats in the realm of cybersecurity. Its innovative techniques, such as driver-based payload delivery and the exploitation of cloud storage systems, highlight both technical expertise and adaptability to evolving environments. Experts anticipate that future campaigns by this group will maintain their hallmark sophistication.
Most recently, Careto re-emerged in May 2024, resuming operations after a decade-long hiatus. Active since 2007, the group disappeared in 2013, having compromised 380 unique targets across 31 countries, including the United States, the United Kingdom, France, Germany, China, and Brazil.


