Cybersecurity experts are increasingly gathering information about suspected criminals from unexpected sources—vast troves of compromised credentials, browser profiles, and other system data available on Telegram. The perpetrators themselves are being ensnared, as their devices become infected with malware that, in turn, exposes their identities to researchers and law enforcement.
Last week, Hudson Rock reported that it had uncovered data on two alleged fraudsters—Mujtaba Raza and Mohsin Raza—who are listed among the FBI’s most wanted. In April 2021, U.S. authorities charged the men with conspiracy to produce and distribute fraudulent documents, as well as identity fraud involving counterfeit identification.
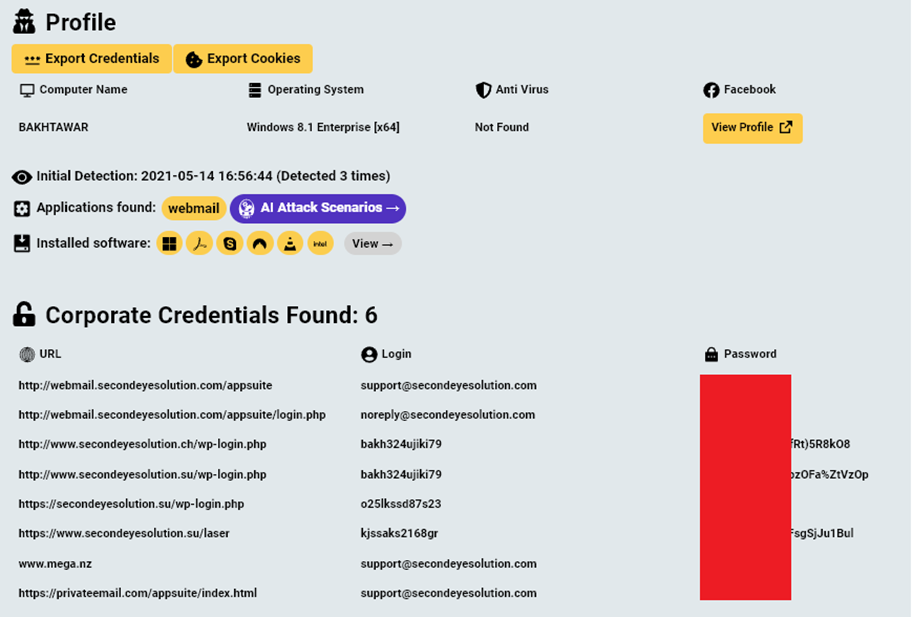
According to investigators, the men operated an illicit online business called SecondEye Solution, based in Karachi, Pakistan. The company sold digital copies of fake passports, driver’s licenses, and national IDs for more than 200 countries. The criminals advertised their services on hacker forums.
After the charges were filed, Mujtaba and Mohsin went into hiding and have remained fugitives. However, Hudson Rock managed to obtain information about them using data collected via infostealers. These programs infect computers, gathering credentials and other information, which often end up publicly available on Telegram. Commonly mentioned infostealers include RedLine, Raccoon, and Erbium, which are frequently spread through fake software, cryptocurrency wallets, or pirated software.
Among the uncovered data were accounts linked to SecondEye, as well as cloud storage associated with those accounts. Of particular interest were browser logs from an infected device, which contained browsing history, autofill data with addresses and passport numbers, as well as IP addresses and computer names. One screenshot captured by the malware showed the use of a Skype account under the brand Forwarderz, another company connected to the suspects.
Hudson Rock believes that the computers belong not to Mujtaba and Mohsin themselves but to their alleged accomplices—Muhammad Kambar and Bahtawar Abbas. However, attempts to obtain comments from the accomplices were unsuccessful.
The collected data was also implicated in recent breaches, during which hackers accessed information from major companies such as AT&T and Ticketmaster. The findings were handed over to the FBI and met all necessary criteria for public disclosure. Neither the FBI nor Hudson Rock has provided further comments.
Instances of using infostealers to unmask criminals are becoming increasingly frequent. In July, Recorded Future uncovered more than 3,300 unique credentials tied to access to websites distributing CSAM content.


