Proofpoint reports that Iranian hackers launched a phishing attack on a prominent Jewish religious leader using several spoofed email addresses.
A direct connection between the attack and members of the IRGC could not be established. However, the hackers’ activities have been monitored by other experts for many years and share numerous characteristics with the operations of APT42, also known as TA453, Mint Sandstorm, Charming Kitten, and Yellow Garuda.
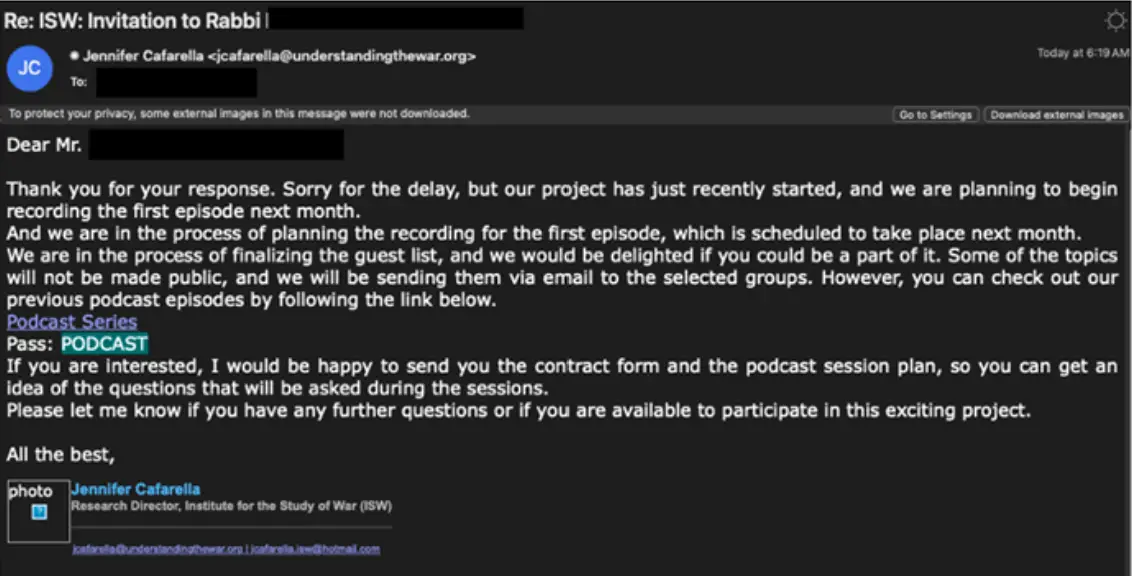
The attackers initially sent several emails, posing as the Director of Research at the American think tank Institute for the Study of War (ISW), and invited the target to appear as a guest on a podcast. The initial email did not contain any malicious links, allowing the group to establish contact and gain the target’s trust.
However, after receiving a response from the target, TA453 sent a link to a document hosted on the DocSend platform. The document contained a link to a legitimate ISW podcast, protected by a password. This was likely done to acclimate the target to the idea of entering passwords and clicking on links.
Following another email exchange, the hackers sent a link to Google Drive containing a ZIP archive titled “Podcast Plan-2024.zip.” Inside the archive was an LNK file designed to download the BlackSmith malware toolkit, which in turn deployed the AnvilEcho PowerShell trojan. Notably, the LNK file was disguised as a PDF, and a fake PDF was displayed to the user while the malware was being downloaded in the background.
The primary objective of AnvilEcho is to collect and exfiltrate data to the attacker. The modular nature of the trojan allows it to evade detection and complicates analysis, as the operators actively employ encryption and protection evasion techniques.
It was also determined that the attack targets align with the strategic goals of Iranian intelligence and are part of a broader phishing campaign aimed at politicians, human rights activists, dissidents, and scholars.
The attack on the religious leader began on July 22, and it has been revealed that this is not the first instance of fake podcast invitations being used by TA453. Earlier, in February 2024, Proofpoint documented similar phishing attacks utilizing fake domains registered by the group in January. The fake podcast invitation represents a new tactic, but TA453 has already employed various social engineering methods to persuade its targets to open or download malicious content.


