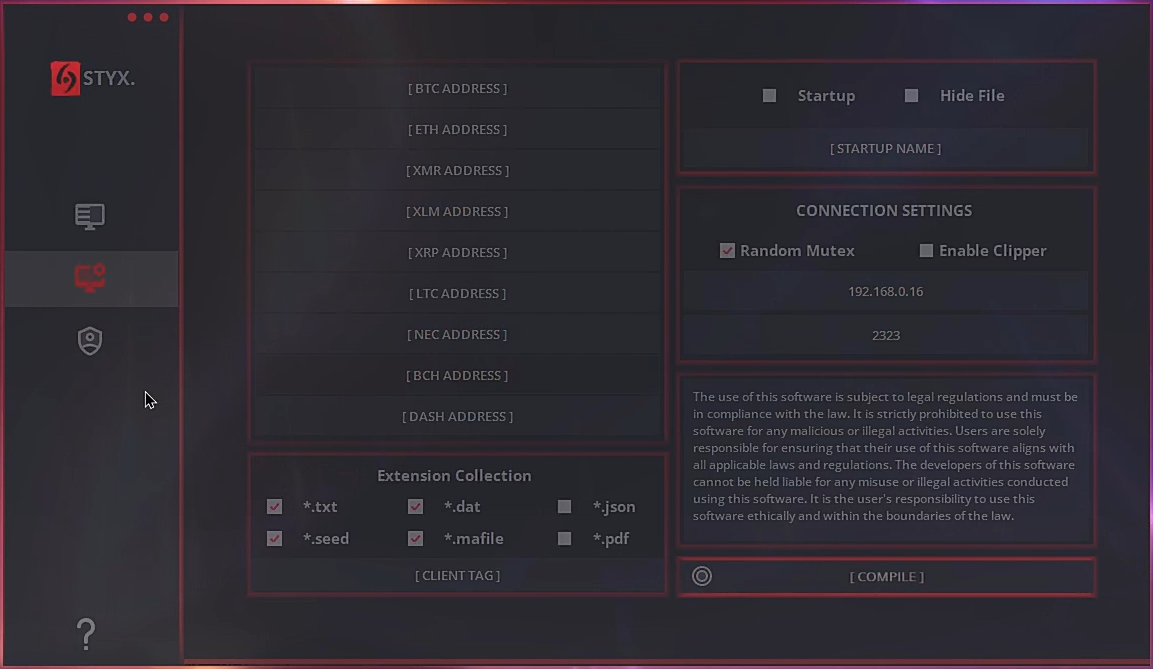
Styx Stealer builder (screenshot from the YouTube video).
Researchers at Check Point Research (CPR) have uncovered a new malware called Styx Stealer, which is capable of exfiltrating browser data, sessions from Telegram and Discord messengers, as well as cryptocurrency. Despite its recent emergence, this virus has already been observed in attacks, including those targeting the company’s clients.
The developer of Styx Stealer has been linked to one of the threat groups behind the notorious malware Agent Tesla, known by the alias Fucosreal. This malicious actor participated in a spam campaign also aimed at the company’s clients. During the debugging process of Styx Stealer, the developer made a critical error, inadvertently exposing data from their computer. This allowed researchers to obtain a significant amount of information, including client details, profit figures, and contact information for other cyber criminals.
Styx Stealer was created based on an earlier version of another notorious virus, Phemedrone Stealer, which gained widespread notoriety following the exploitation of a vulnerability in Windows Defender SmartScreen in early 2024. Phemedrone was initially available on GitHub but was later removed, leading to the emergence of various modifications, one of which became Styx Stealer. This malware is sold through the website styxcrypter[.]com and includes features for automatic execution, clipboard monitoring, and protection against analysis.
CPR determined that the developer of Styx Stealer also created and utilized Telegram bots to transmit the stolen data. During the investigation, it was revealed that the creator of Styx Stealer actively collaborated with another cybercriminal known as Mack_Sant, who provided him with a token for use in Styx Stealer.
Additional information obtained during the investigation showed that Styx Stealer was used in attacks on companies from various industrial sectors, including diamond and metallurgical industries, among others. However, despite the active attempts to distribute the malware, researchers were able to prevent any damage to clients.
This case serves as a vivid example of how even seasoned cybercriminals can make mistakes that expose their identities and plans. As a result of the developer’s error, Check Point Research was able to acquire crucial data that will aid in combating cyber threats and protecting companies from similar attacks.


