The new malicious package, SteelFox, is disseminated through forums and torrent trackers, offering users illicit activation of software such as Foxit PDF Editor, JetBrains, and AutoCAD. SteelFox not only mines Monero cryptocurrency but also steals credit card information by exploiting vulnerable drivers to escalate privileges on Windows systems.
Discovered by Kaspersky Lab researchers in August, SteelFox first emerged in February 2023; however, its active distribution has intensified noticeably. Over the past few months, Kaspersky’s products have detected and blocked more than 11,000 infection attempts by this malware.
SteelFox employs the BYOVD (Bring Your Own Vulnerable Driver) technique, previously associated with state-sponsored cybercriminals and extortionist groups. In this case, the malware exploits vulnerabilities CVE-2020-14979 (CVSS: 7.8) and CVE-2021-41285 (CVSS: 7.8) to achieve the highest NT/SYSTEM privileges on compromised systems.
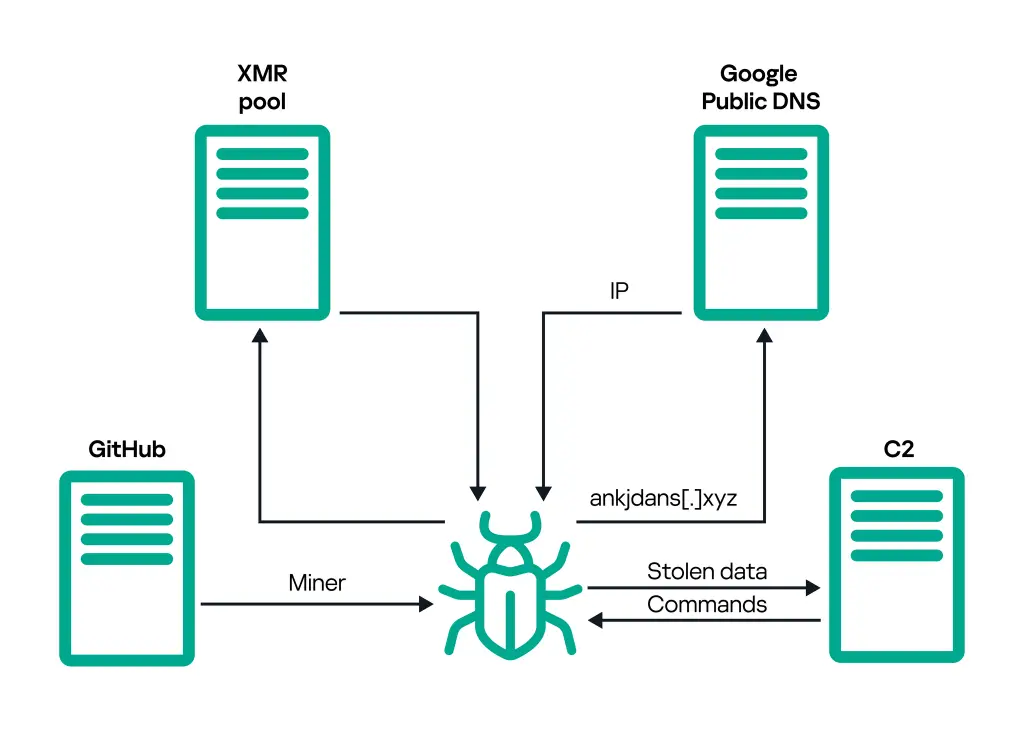
Once administrative privileges are obtained, SteelFox creates a service to launch the “WinRing0.sys” driver, granting it full control over the system. This driver is also used for cryptomining due to built-in support for the XMRig program. To secure communication with its command server, SteelFox employs SSL pinning and TLS 1.3, complicating data interception.
Beyond cryptomining, SteelFox functions as an information stealer, gathering data from 13 web browsers along with system and network information. Stolen data includes credit card details, browsing history, and cookies, posing a significant threat to user privacy.
SteelFox’s command infrastructure relies on concealed domains, with addresses periodically changed via Google Public DNS and DNS over HTTPS (DoH). Although not targeted at specific countries, Kaspersky Lab experts note its activity in Brazil, China, Russia, Mexico, UAE, Egypt, Algeria, Vietnam, India, and Sri Lanka.
Despite its recent surge in activity, SteelFox already demonstrates advanced functionality, underscoring the developer’s skill in integrating external libraries and sophisticated features into the malware.


