
A recent investigation by Kaspersky Lab has uncovered a new ransomware family, Ymir, actively deployed by cybercriminals. This malware employs advanced evasion techniques, executing operations in memory through functions such as malloc and memmove.
In the attack chain analyzed by experts, the attackers infiltrated the victim’s system via PowerShell, installed utilities like Process Hacker and Advanced IP Scanner, and subsequently launched the Ymir ransomware. The malware encrypts files using the ChaCha20 algorithm, appending the extension “.6C5oy2dVr6” and leaving behind ransom demands in PDF files.
Static analysis revealed that Ymir employs CryptAcquireContext and CryptGenRandom functions for cryptographic operations. The malware also includes commands for automatic deletion via PowerShell, and critical libraries are loaded directly into memory, making detection particularly challenging.
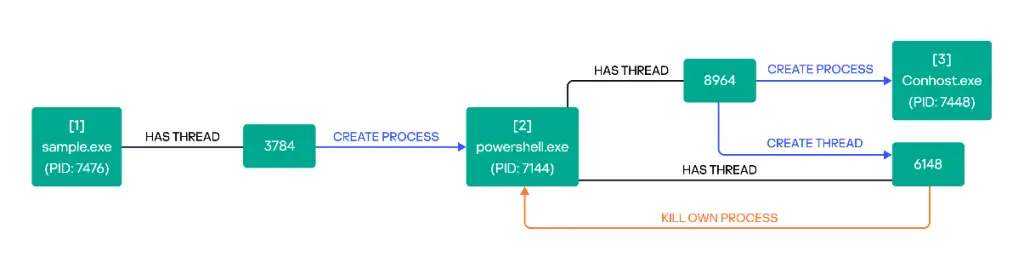
During dynamic analysis, it was observed that Ymir extensively uses the memmove function for enumerating and encrypting files. The use of the MinGW compiler points to experienced developers with a strong familiarity with Windows systems.
Interestingly, Ymir lacks built-in network capabilities for data exfiltration, despite claims in the ransom note suggesting data theft. This implies that the attackers may have preemptively extracted data via other means, such as FTP or cloud services, or they may have simply bluffed.
While investigating Ymir, Kaspersky experts discovered its connection to another malware, RustyStealer, used for data harvesting and maintaining access to compromised systems. RustyStealer utilized PowerShell scripts to create covert communication channels, enabling attackers to move undetected within the infected infrastructure.
Using a YARA rule derived from the analysis of Ymir, a similar sample was detected in Pakistan, indicating that the attackers are actively testing their developments on vulnerable systems, concealing their location through VPNs and Tor.
Among the uncovered data was a comment in Lingala, a language spoken in Africa, potentially hinting at the malware developers’ origin. However, no definitive information about the group behind the attacks has yet been identified.
Experts caution that this new ransomware poses a significant threat to companies, particularly those lacking comprehensive response measures. Detection is hindered by the ransomware’s ability to remain concealed and swiftly erase traces of its presence within the system.


