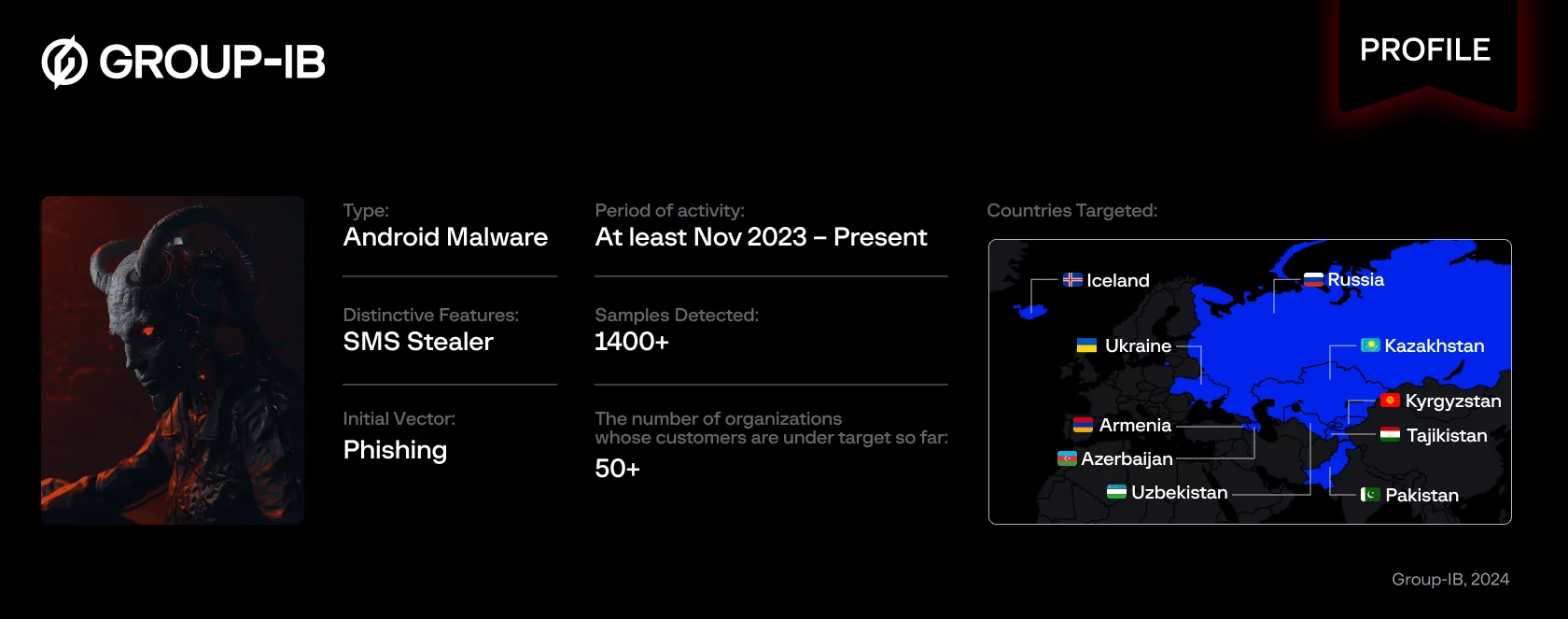
A new malicious campaign has been detected in Uzbekistan, propagating an Android malware known as Ajina.Banker. Discovered by Group-IB specialists in May 2024, this Trojan has been operational since November 2023 and currently boasts around 1400 unique versions.
Ajina.Banker derives its name from a mythical Uzbek spirit renowned for its cunning and shapeshifting abilities. The attackers exploit this camouflage capability by disguising the malware as popular applications, including banking services and government portals. This deception tricks users into willingly installing the Trojan onto their devices.
The primary method of Ajina.Banker distribution is social engineering through the Telegram messenger. Hackers create numerous accounts from which they send links to malicious files. These files are disguised as enticing offers, promotions, or even tax authority applications. As a result, users, lured by promises of “lucrative rewards” or “exclusive access,” install the malware, unaware of its true nature.
The attack mechanism also involves sending messages with attached malicious files directly, without any additional explanation. The attackers actively utilize various channels to disseminate the Trojan, thereby circumventing the built-in security systems of some chats.
According to researchers, Ajina.Banker’s attacks are not limited to Uzbekistan. The Trojan also collects data on financial applications in countries such as Armenia, Azerbaijan, Kazakhstan, Kyrgyzstan, Russia, and even Iceland. Additionally, the program gains access to SIM cards and intercepts incoming SMS messages, including two-factor authentication (2FA) codes, posing further risks to users.
Group-IB’s investigations have revealed that Ajina.Banker has multiple versions, indicating its active development. The latest versions of the Trojan are capable of stealing phone numbers, bank card details, and PIN codes, making it extremely dangerous.
Interestingly, Ajina.Banker operates on an affiliate program model: the main group manages the infrastructure, while distribution and attacks are carried out through a network of partners who receive a share of the stolen funds.
Security experts advise users to exercise extreme caution when receiving suspicious messages and downloading applications. They should only use trusted app stores like Google Play, carefully review app permissions, and install security software to prevent such threats.


