Cybersecurity researchers have uncovered a novel Adversary-in-the-Middle (AitM) phishing tool targeting Microsoft 365 accounts, capable of stealing credentials and two-factor authentication (2FA) codes. This tool, named Sneaky 2FA, has been in active use since October 2024.
The French cybersecurity firm Sekoia first detected the activity of this phishing kit in December, identifying approximately 100 domains associated with its deployment. Its moderate proliferation suggests that the tool has gained considerable traction among cybercriminals.
Sneaky 2FA is distributed as a Phishing-as-a-Service (PhaaS) offering through the Sneaky Log service, hosted on Telegram. Buyers receive an obfuscated version of the source code under a licensing model, allowing them to independently execute phishing campaigns.
One common attack method involves sending emails containing fake payment receipts. Recipients are prompted to open attached PDF files with QR codes, which redirect them to counterfeit authentication pages when scanned.
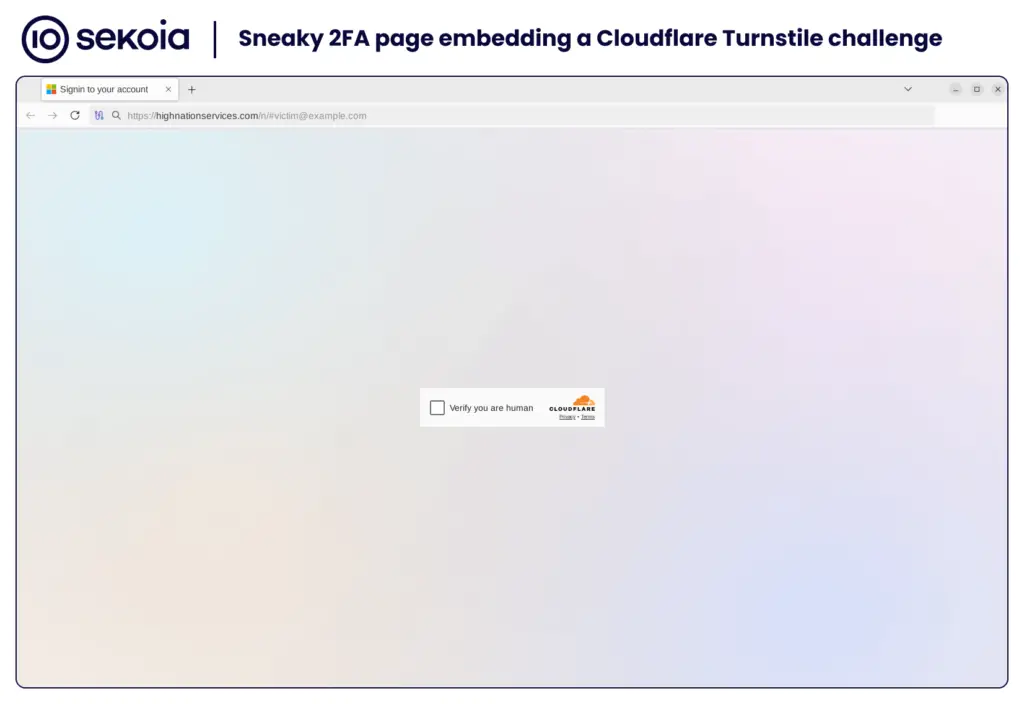
According to Sekoia, these phishing pages are hosted on compromised servers, often powered by WordPress or other managed domains. To enhance credibility, the victim’s email address is pre-filled on these fake pages. The tool employs robust evasion techniques, including traffic filtering and Cloudflare Turnstile checks, to block analysis and automated detection.
An intriguing feature of Sneaky 2FA is the redirection of visitors with suspicious IP addresses (e.g., from cloud data centers or VPNs) to a Microsoft-related Wikipedia page. This tactic, dubbed WikiKit by TRAC Labs researchers, helps mislead security analysts.
To deceive victims, the tool mimics Microsoft interfaces using blurred graphics, creating an illusion of legitimacy. License checks performed on the server ensure that the kit is accessible only to clients with active keys, priced at $200 per month.
Investigators also discovered potential links between Sneaky 2FA and the notorious W3LL Panel phishing kit, previously exposed by Group-IB. Similar licensing models and data transmission methods suggest a connection between these tools.
Further analysis revealed that several domains associated with Sneaky 2FA were previously used for other prominent phishing kits, including Evilginx2 and Greatness. This indicates that some cybercriminals are transitioning to the new service.
Sekoia has noted unusual transitions between User-Agent strings during the authentication process, a distinctive pattern that helps identify the use of Sneaky 2FA. This anomaly sets the tool apart from legitimate interactions, enabling analysts to pinpoint malicious activities.