According to a report by researchers at Trac LABS, the financially motivated hacking group UNC2465 has been actively employing the SMOKEDHAM backdoor as its primary tool for infiltrating corporate networks.
The attackers gain initial access to target systems through a classic triad of techniques: phishing campaigns, trojanized software, and supply chain compromises. This multifaceted approach allows the group to effectively conceal its presence while maneuvering within compromised infrastructures.
Once inside the network, the adversaries deploy tools such as Advanced IP Scanner and BloodHound for reconnaissance, Remote Desktop Protocol (RDP) for lateral movement, and Mimikatz for credential harvesting. Previously, the group utilized ransomware like DARKSIDE and LOCKBIT, but recent malicious campaigns have revealed their use of SMOKEDHAM through malvertising and compromised applications.
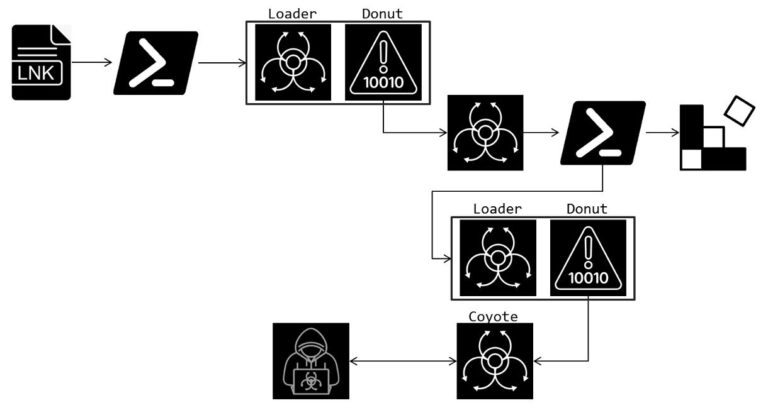
The infection process begins with an NSIS script, which establishes persistence on the infected device and downloads malicious files. The script verifies the presence of necessary components and registry entries to prevent re-execution. It then creates directories, downloads a password-protected archive, and extracts both legitimate and malicious tools.
By modifying registry entries, the script ensures the execution of a malicious shortcut during system startup. It also configures the MSDTC service with elevated privileges, potentially enabling DLL hijacking. In its final stages, a batch script is executed, utilizing PowerShell to download and launch a malicious .NET application from a remote server.
The malware communicates with a command-and-control (C2) server, transmitting details about the infected system, including the computer and user names. The server can issue commands for further system exploration, such as “whoami” or “systeminfo,” and perform arbitrary actions. To evade detection, RC4 encryption is employed.
Additionally, the malware can capture screenshots, upload and download files, and in its PowerShell variant, inject code directly into memory, leaving no traces on the disk.
The attackers further enhance their operations by signing executables containing malicious DLLs with extended validation certificates, enabling the execution of concealed scripts.
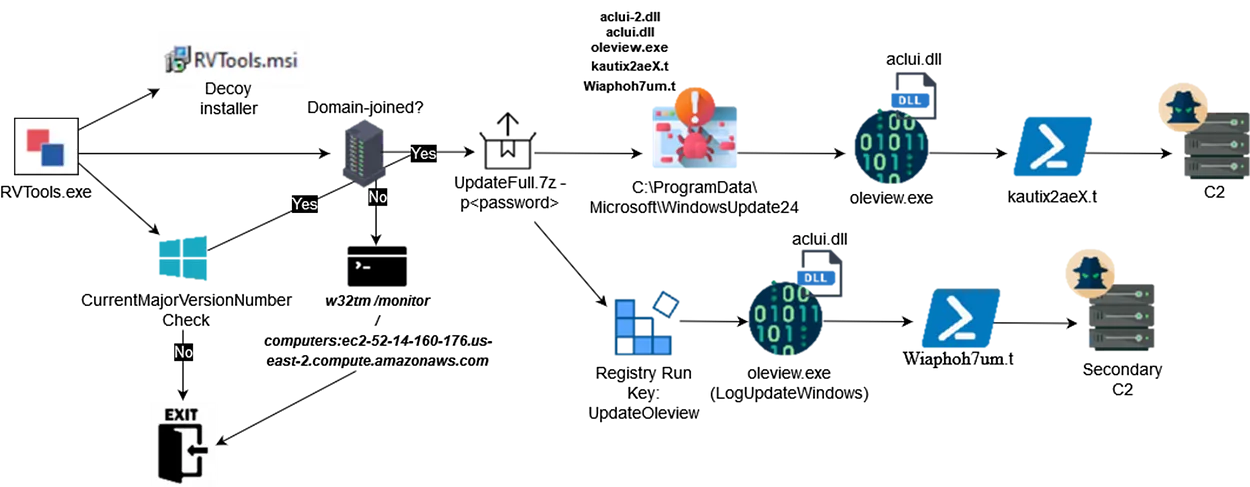
The NSIS script checks whether the device belongs to a DOMAIN, and if not, it queries specific data from an Amazon EC2 instance. Persistence is achieved by copying a legitimate file, “oleview.exe,” along with a renamed malicious DLL and creating a registry entry for autostart.
In one documented attack, the adversaries used the “systeminfo” command and directory listings to gather system information. A PowerShell script with malicious instructions was then delivered via a Dropbox link. The script created a directory in ProgramData and downloaded additional files, including a modified “winlogon.exe” and UltraVNC remote access configurations (UltraVNC.ini).
The modified “winlogon.exe” was subsequently launched, establishing a remote connection to the attackers’ server via UltraVNC over port 443. This demonstrated the attackers’ intent to secure remote access and escalate privileges within the system.
The analyzed case underscores how modern cybercriminals skillfully blend social engineering, legitimate tools, and advanced technical methods to craft multilayered attacks that evade traditional security measures.
What raises particular alarm is their ability to disguise malicious activity as legitimate operations, emphasizing the need for a holistic cybersecurity strategy that transcends standard antivirus solutions.