
Specialists from the Graz University of Technology (Austria) have unveiled a new cross-cache attack on the Linux kernel called SLUBStick, which transforms a limited heap vulnerability into an arbitrary memory read and write capability, allowing attackers to elevate privileges or break out of containers.
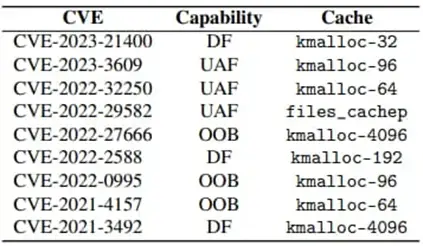
The attack has been tested on Linux kernel versions 5.9 and 6.2, demonstrating its high versatility. The experiments employed nine existing vulnerabilities on both 32-bit and 64-bit systems.
SLUBStick proved effective even with modern kernel protections such as Supervisor Mode Execution Prevention (SMEP), Supervisor Mode Access Prevention (SMAP), and Kernel Address Space Layout Randomization (KASLR) active.
Details of the attack will be presented at the Usenix Security Symposium at the end of August. Researchers will demonstrate privilege escalation and container escape on the latest Linux version with enabled protections.
Technical Details of SLUBStick
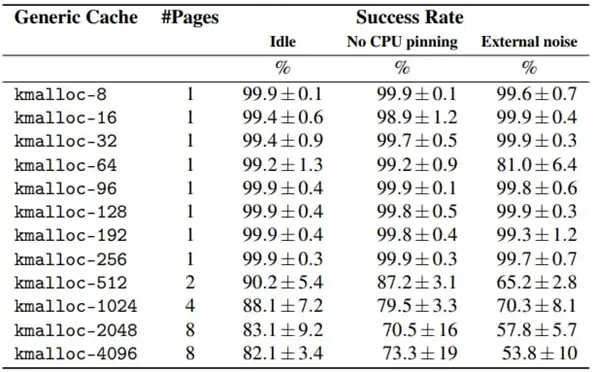
The Linux kernel manages memory by allocating and freeing memory blocks (slabs) for various types of data structures. Vulnerabilities in the memory management process can allow attackers to distort or manipulate these data structures, known as a cross-cache attack. Typically, such attacks succeed approximately 40% of the time and often cause system crashes.
SLUBStick leverages heap vulnerabilities such as double-free, use-after-free (UAF), or out-of-bounds write to manipulate the memory allocation process. The attack then uses a synchronization side channel to determine the precise timing of memory block allocation and deallocation, enabling the attacker to predict and control memory reuse.
With this information, the likelihood of successfully exploiting a cross-cache attack increases to 99%, making SLUBStick highly practical.
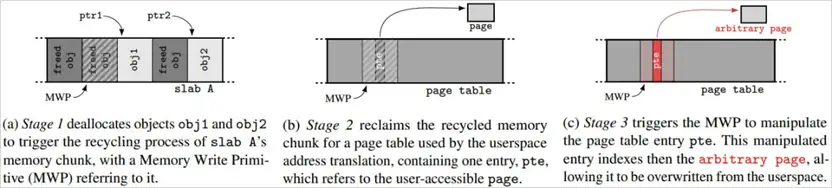
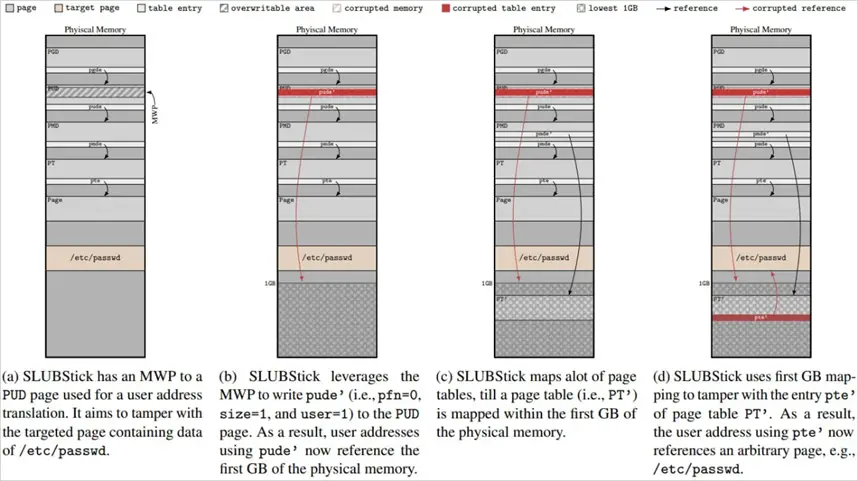
Conversion of Heap Vulnerability into Arbitrary Memory Access
The conversion process involves three stages:
1. Freeing specific memory blocks and waiting for the kernel to reuse them;
2. Reallocating the blocks in a controlled manner so they are used for critical data structures such as page tables;
3. After the blocks are returned, the attacker overwrites the page table entries, gaining the ability to read and write data to any memory area.
Real-World Security Impact
Like most side-channel attacks, SLUBStick requires local access to the target machine with code execution capabilities. Additionally, the attack requires a heap vulnerability in the Linux kernel to gain memory access.
The attack offers several advantages for malicious actors. Even for those who already possess code execution capabilities, SLUBStick provides the means to escalate privileges, bypass kernel protections, break out of containers, or be used as part of a complex attack chain.
Privilege escalation can be used to gain root access, allowing the execution of any operations, while container escape enables breaking out of an isolated environment and accessing the host system. In the post-exploitation phase, SLUBStick can modify kernel structures or hooks to maintain persistence, making malware detection more challenging.
For those interested in delving deeper into SLUBStick and experimenting with vulnerability exploitation, the researchers have published all details in a technical report and made the code available on GitHub.


