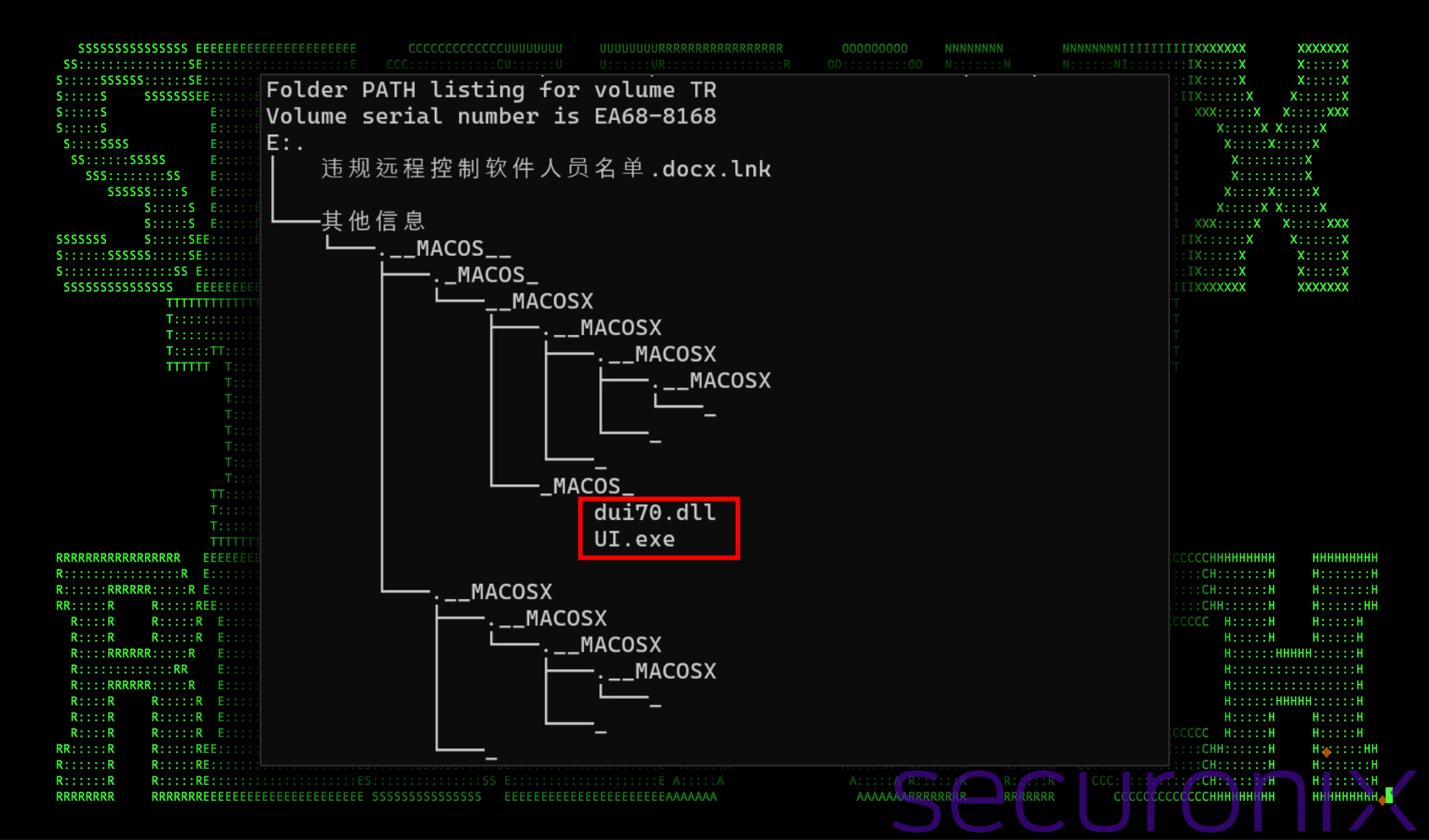
Output of the “tree” command upon the extracted zip file contents
Securonix has uncovered a major espionage operation named “Slow#Tempest,” targeting individuals and organizations in China. The hackers aimed to gain prolonged access to systems for espionage and potential sabotage, with the capability to launch ransomware attacks or steal data. Experts assert that the primary objective of the campaign was long-term control over networks and the execution of strategic goals that may align with state interests.
The researchers were unable to precisely pinpoint the attackers’ location or their affiliation with any specific group. However, the sophisticated nature of the malware and the tools used for data scanning and theft suggest that government institutions or large business entities were the likely targets.
While Securonix experts did not disclose the specific victims of the attack, they noted that the phishing emails used in the campaign were written in Chinese, and the hackers’ infrastructure was hosted on servers belonging to the Chinese company Shenzhen Tencent Computer Systems. These factors, along with telemetry data, indicate that the primary target of the attack was indeed in China.
Moreover, the researchers observed that the attackers had a deep understanding of the Chinese language, infrastructure, and the characteristics of potential victims. However, there is a possibility that the attack could have been orchestrated from other Chinese-speaking regions—Taiwan, Singapore, or Hong Kong.
The investigation began with a single incident, but it led to the discovery of several other attacks, indicating a larger number of victims. The campaign is still ongoing and is unlike previous ones. The unique combination of tools and methods used by the hackers suggests that this is an independent operation, rather than a continuation of known campaigns.
The attacks started with the delivery of malicious ZIP files through phishing emails. The files were disguised as documents related to personnel matters, allowing the cybercriminals to evade antivirus programs. One such file, attractively named “List of individuals who violated the remote control software usage rules,” upon being opened, implanted backdoors that went undetected by security systems. The hackers then scanned the systems for data and extracted credentials from browsers.
The attackers made some mistakes that led to the discovery of a tool containing the username “guoyansong.” Securonix speculates that this might be an abbreviation of the name Guoyan Song, which is a real Chinese name. Despite the lack of clear evidence linking the attack to any known threat group, experts believe that the operation was conducted by a seasoned attacker, utilizing advanced exploits like CobaltStrike and a wide array of other post-exploitation tools.


