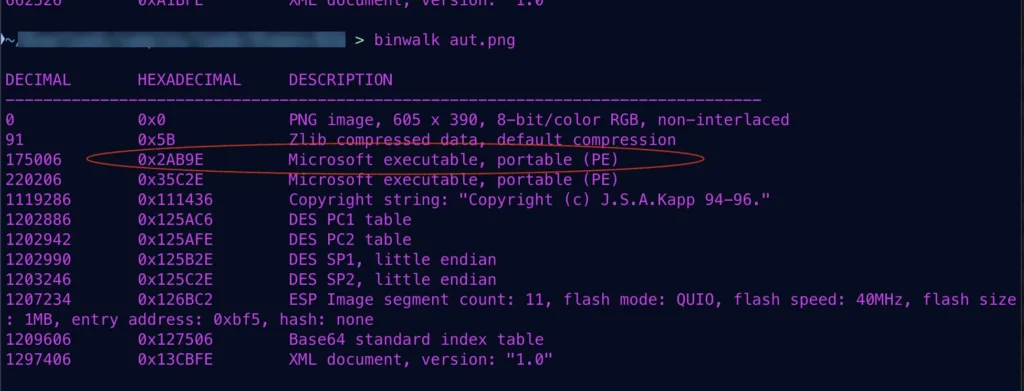
Binwalk output for one of the PNG files used by the loader
Researchers from Intezer Labs have uncovered a series of cyberattacks targeting organizations in Chinese-speaking regions, including Hong Kong, Taiwan, and mainland China. These attacks leverage a multi-stage loader, PNGPlug, to deliver the sophisticated malware known as ValleyRAT.
The attack begins with a phishing page designed to lure victims into downloading a malicious MSI file disguised as legitimate software. Upon execution, the MSI file performs two actions: it installs a harmless application to create the illusion of legitimacy and extracts an encrypted archive containing malicious components.
The MSI file exploits the Windows Installer CustomAction feature to execute malicious code. The encrypted archive, named all.zip, is decrypted using the embedded password hello202411. Key components include libcef.dll (the loader), down.exe (a legitimate application), and files aut.png and view.png, which are camouflaged as images but actually contain malicious payloads.
The loader, libcef.dll, sets up the environment for malware execution by modifying the system file ntdll.dll to inject data into memory and analyzing command-line parameters. If the /aut parameter is detected, the loader extracts the path to down.exe, writes it to the registry, and executes the payload from aut.png. Otherwise, it triggers view.png, injecting its contents into the colorcpl.exe process.
ValleyRAT, deployed via PNGPlug, is an advanced piece of malware attributed to the Silver Fox group. It features multi-layered execution mechanisms, including in-memory shellcode execution, privileged operations, and persistence through the registry and scheduled tasks.
The analysis highlights the attackers’ extensive tactics, including phishing sites, disguising malicious files as legitimate applications, and exploiting free software often used by employees due to a lack of corporate tools.
The APT group Silver Fox is known for conducting espionage campaigns targeting Chinese-speaking organizations. They utilize tools like ValleyRAT and Gh0st RAT to collect data, monitor activity, and deploy additional modules. The campaign’s linguistic focus underscores its strategic scale and purpose. Victims’ lack of investment in cybersecurity further amplifies their vulnerability to such sophisticated attacks.
The modular PNGPlug loader allows attackers to tailor threats to various campaigns, significantly enhancing their adaptability and potency. These events underscore the critical need for advanced detection and defense measures to combat the ever-evolving landscape of cyber threats.