Researchers at Seqrite Labs have uncovered a new malicious campaign orchestrated by the Silent Lynx hacking group. Previously known for targeting institutions across Eastern Europe and Central Asia, including think tanks and financial institutions involved in economic planning, the group has now shifted its focus toward Kyrgyzstan’s National Bank and the country’s Ministry of Finance.
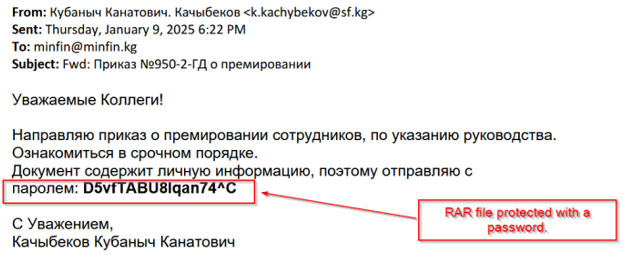
The attack begins with meticulously crafted phishing emails that closely resemble legitimate corporate correspondence. Victims receive messages purportedly from colleagues or superiors, marked with urgent subject lines to heighten credibility.
The emails claim that the attached archive contains critical documents, such as bank reports or bonus payout notifications. To enhance the illusion of authenticity, the attackers incorporate real employee names and company details, while the subject line—e.g., “Order on Employee Bonuses”—is designed to appear official and convincing.
The RAR archive is password-protected, ostensibly to ensure confidentiality, further reinforcing the impression that the email is legitimate.
The topic of bonuses naturally piques curiosity, particularly in corporate and governmental environments, prompting recipients to open the archive to review the details. Within the compressed file, victims find two documents:
- A decoy file, appearing as an official order regarding bonuses.
- A malicious executable, developed in Golang.
The embedded decoy documents exhibit a high level of sophistication, featuring real job titles, names, and timestamps, making the forgery almost indistinguishable from genuine correspondence. The meticulous attention to detail ensures that recipients perceive the message as a routine workplace interaction, making opening the file seem like a natural course of action.
Once executed, the Golang-based malware acts as a reverse shell, establishing a connection with the group’s command-and-control (C2) server. This grants the attackers remote access to the victim’s system, enabling them to exfiltrate confidential data and maintain prolonged access.
By leveraging social engineering and crafting highly convincing counterfeit documents, Silent Lynx has made this campaign particularly insidious—even seasoned professionals may unwittingly open the malicious files, misled by the authenticity of the correspondence.
Seqrite Labs researchers have identified notable similarities between Silent Lynx and the Kazakhstan-based YoroTrooper group. Both employ PowerShell, rely on similar toolkits and attack methodologies, and focus their operations on intelligence gathering.
This latest campaign underscores the evolving sophistication of cyber threats, demonstrating how precision-crafted phishing tactics continue to be one of the most effective tools for infiltrating high-value targets.