Specialists from Securonix Threat Research have uncovered a campaign likely linked to the North Korean APT37 group. The attack, named SHROUDED#SLEEP, targets countries in Southeast Asia. A key feature of the attack is the use of a stealthy PowerShell backdoor known as VeilShell.
The primary target of APT37 (also known as Reaper, Group123) appears to be Cambodia, though the scope of the attack may extend to other Southeast Asian nations. The specific industries and companies impacted are not detailed in the Securonix report.
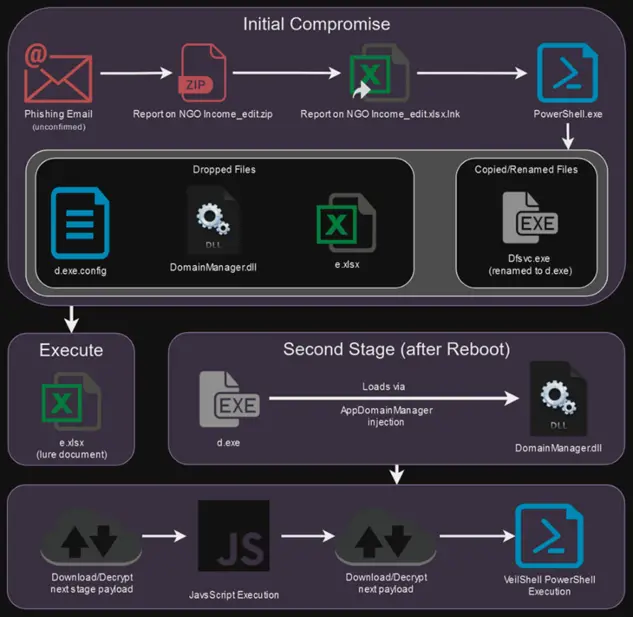
The initial phase of the attack begins when the victim opens a ZIP file attached to an email. Inside the archive are executable files in the form of shortcuts (.lnk), which, when launched, trigger a series of PowerShell commands. These shortcuts may have double extensions (.pdf.lnk or .xlsx.lnk) to masquerade as legitimate PDF or Excel documents. The attackers also alter the shortcut icons to make them appear credible.
The encrypted malicious components are embedded within the LNK file and are automatically extracted. The main objective of the attack is to install the VeilShell backdoor, which grants remote access to the compromised system (RAT), enabling file uploads/downloads, task creation, and registry modification.
A distinguishing feature of SHROUDED#SLEEP is the extended delay before initiating certain stages of the attack, designed to evade heuristic detection systems. Once VeilShell is installed, the code does not execute immediately; instead, it activates only after the system is rebooted.
To maintain persistence within the system, the attackers employ AppDomainManager Hijacking, a technique that allows the inconspicuous injection of malicious code into .NET applications. This is achieved by utilizing a file named “d.exe,” which appears to be a legitimate Microsoft .NET Framework component. The EXE file launches a malicious DLL, “DomainManager.dll,” allowing the execution of malicious code before the legitimate application begins.
Securonix recommends that to defend against such attacks, users should avoid downloading suspicious files from untrusted sources, particularly ZIP archives and PDF documents. It is also crucial to monitor registry changes, network activity, and actions within startup directories. Implementing logging at the process and PowerShell levels can aid in detecting such malicious activities at an early stage.


