Bitdefender has unveiled a decryption tool for the ransomware ShrinkLocker, a threat that has recently alarmed incident response specialists due to its increasing prevalence in attacks.
Alongside the decryption tool, the company published a comprehensive analysis detailing the virus’s mechanisms. ShrinkLocker exploits a built-in Windows feature—BitLocker—to encrypt files and disable all system recovery options. Unlike other ransomware strains that rely on sophisticated algorithms, ShrinkLocker employs a legitimate tool for encryption, enabling it to swiftly encrypt entire disks, including system drives.
The development of the decryption tool was initiated following an investigation into an attack on a healthcare organization in the Middle East. Hackers compromised an unmanaged device before infiltrating the company’s network and deploying ShrinkLocker.
This threat first came to light in the spring, when several organizations issued warnings about its deployment by hackers. In May, Kaspersky Lab reported instances of ShrinkLocker attacks in Mexico, Indonesia, and Jordan. Victims included companies in the steel industry, pharmaceutical enterprises, and government agencies.
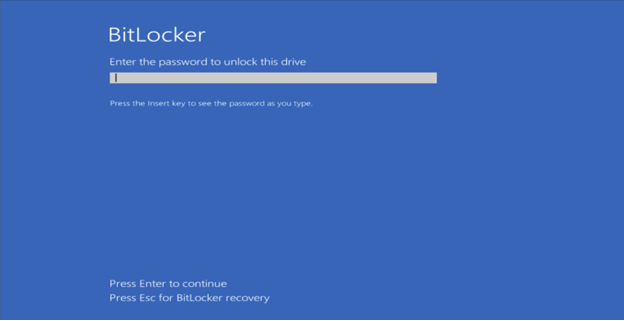
ShrinkLocker checks whether BitLocker is installed on the targeted device. If not, it downloads and configures it autonomously. The program then encrypts the disk using a randomly generated password, which is transmitted to the attackers’ server. Upon reboot, the victim must enter this password to unlock the disk. The screen also displays the attackers’ contact email for ransom negotiations.
According to Bitdefender, ShrinkLocker can encrypt multiple systems simultaneously, with each device taking as little as 10 minutes. Its simplicity makes it an attractive tool for novice hackers seeking to avoid the complexities of schemes like Ransomware-as-a-Service (RaaS). Researchers highlighted that this low barrier to entry allows many cybercriminals to easily adapt the malware to their objectives.
The malware is predominantly used in less sophisticated attacks and targets outdated operating systems such as Windows 7 and 8, as well as server versions like Windows Server 2008 and 2012. Bitdefender experts recommended configuring BitLocker to store all encryption keys in Active Directory, a measure that could thwart such attacks by preventing hackers from completing the encryption process without access to the keys.


